PHP hack tools are created and used by attackers to help automate frequent or tedious tasks. During a recent investigation, we came across a hack tool used to simplify the process of sending predefined HTML emails to a list of email addresses.
The tool runs on top of PHPMailer’s library, which handles the connection and sending of the malicious emails.
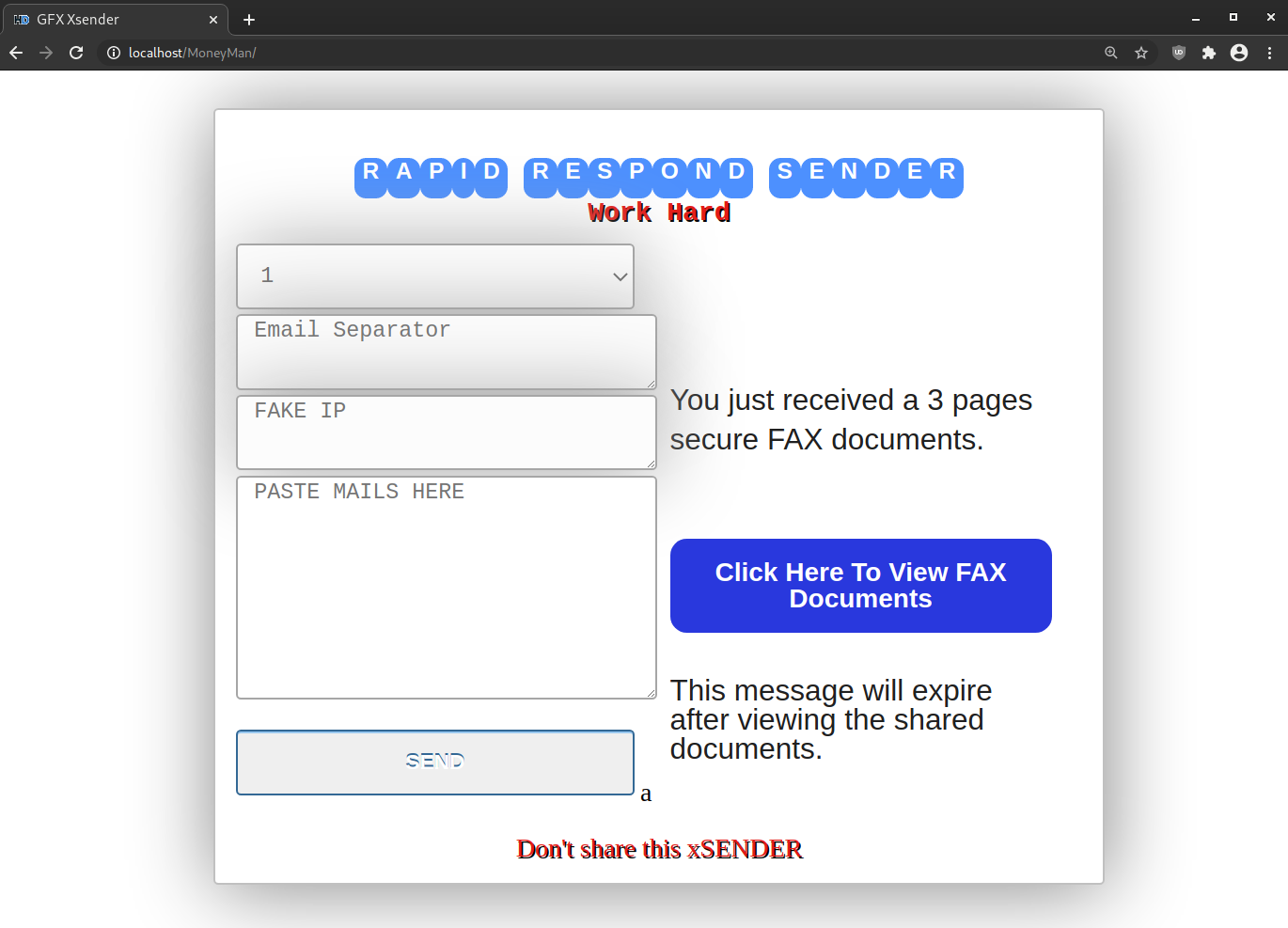
The hack tool also grants the ability to authenticate to an email address on a remote server. Once authenticated, an attacker can use the to send out malicious email on the victim’s behalf.
These settings can be hard coded to the configuration variables found within the PHP file:
$website="hxxps://evil[.]com/"; //Make this full url including folders of where login files reside //$website="http://www.website.com"; //Make this full url including folders of where login files reside define('SMTPENABLE', true); // enable smtp true or false define('HOST', '[ipaddress or hostname]'); //smtp host define('PORT', 465); //smtp port define('USERNAME', 'attackercontrolled@example.com'); // smtp username define('PASSWORD', 'password'); //smtp password define('AUTH', true); // is smtp require authentication true or false define('ENC', 'ssl'); // is smtp require encryption (ssl|tls|) or leave false for none define('SMTPSENDEREMAIL', 'spoofed@nottherealsender.com');
By doing this, the email header logs of the malicious email will show the IP address of the server hosting the hack tool and not the attacker’s IP address — effectively acting as a proxy.
Attackers can use any email account on the Internet that accepts SMTP connections, essentially spoofing the From email to send unsolicited spam, phishing, or other unwanted emails.
One of the best ways to detect this type of malicious activity is to use a server side scanner and monitoring service to identify any indicators of compromise on your website.