As a child, I loved sending secret messages to my friends using invisible ink. A quick squeeze of lemon juice was all I needed to jot down my secret message. When combined with a simple heat source (I used the heat of the wood stove), the contents of my top secret note were revealed in shades of brown on the paper.
If this sounds familiar to you, then you too have participated in the ancient art of steganography. But how does it relate to website security? In this blog post, we will delve into the world of steganography, exploring what it is, how it works in the context of malware, and implications for your website’s environment.
What is steganography?
Steganography is the art of concealing secret information within (or even on top of) seemingly innocuous files or objects. It’s a bit like playing hide and seek, where data is hidden in a way that nobody even suspects it’s there.
In the context of website security, steganography is sometimes used by bad actors to camouflage their malware in typical website files — for example, by embedding malware within CSS files or concealing a credit card skimmer inside a seemingly benign audio file.
Don’t make the mistake of confusing steganography with cryptography, which involves scrambling data and secret keys for decoding. While it’s common for them to appear hand-in-hand in the real world, cryptography aims to ensure privacy — steganography’s main objective is secrecy and deception.
How does steganography work?
One popular method of steganography is called least significant bit (LSB) steganography, which essentially tucks away secret data in the tiniest bits of a media file.
For example, imagine you have an image file. Each pixel has three bytes of data for red, green, and blue colors (and sometimes a fourth one for transparency, called “alpha”). With LSB steganography, the last bit of each of these bytes is altered to hide secret data. So, if you want to hide 1 MB of data, you’ll need an 8 MB image file.
Most importantly, changing the last bit of the pixel value doesn’t actually change how the image looks. So, when someone’s looking at the original and the modified images, they won’t be able to spot any difference. Sneaky, right?
You can accomplish the same result with other digital media, like audio and video files, by hiding data in parts of the file that don’t really change how it sounds or looks.
Another less common steganography technique involves hiding the message in a larger text by using word or letter substitutions. The sender hides the message by putting the secret words at specific intervals. This method is easy to use, but it can make the text look weird and out of place since the hidden words might not fit well in their sentences.
Recent examples of steganography
While detecting steganography on websites can be a challenging task, we rounded up a few recent examples of steganography found on hacked websites in recent years:
Steganography conceals web shell in PHP malware
In 2021, Sucuri Malware Researcher Denis Sinegubko documented how seemingly benign CSS and PHP files were being used to hide malicious code. An inconspicuously named license.php file was found to contain text for a license agreement, but hidden within the file on line 134 was a gap between two comments containing malicious PHP containing a whitespace decoder.
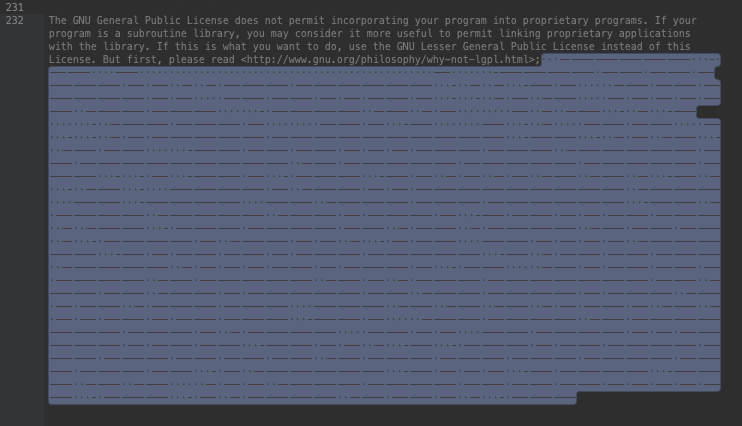
The hidden payload was found to contain nearly 300KB of invisible tabs and spaces, which when decoded, revealed a web shell that provided hackers with tools to access files and databases on the server, collect sensitive information, infect files, and conduct brute force attacks.
Malware uses whitespace to hide malicious JavaScript in CSS files
In another case from 2020, malware was found concealed below empty lines in a seemingly benign.CSS file. The fonts.css file appeared to contain only CSS rules at first glance, but further investigation revealed numerous empty lines at the bottom which were hiding malicious JavaScript code.
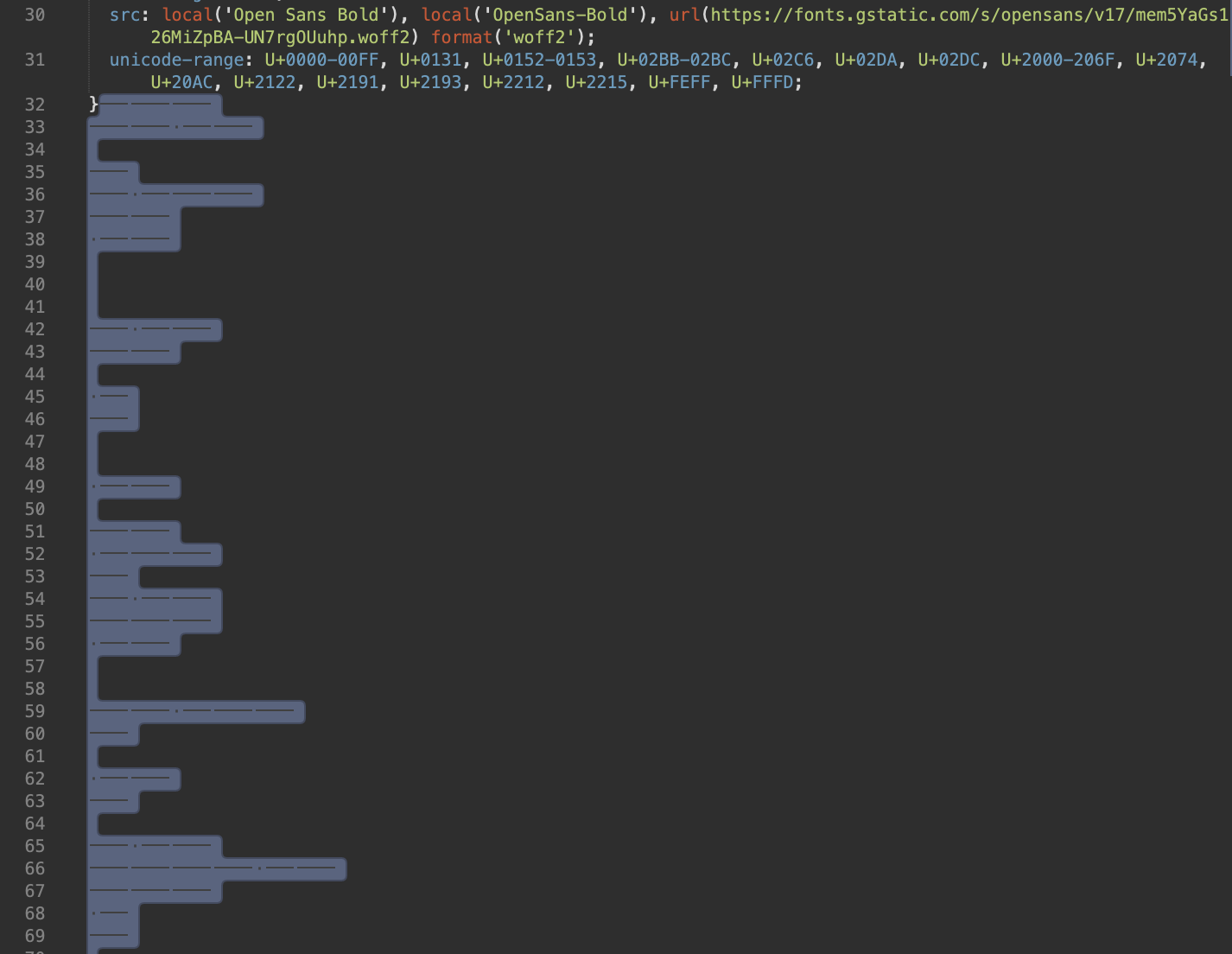
The malware was concealed using sequences of tab and non-tab characters, similar to Morse code. The algorithm then processed the file and constructed the JavaScript function character by character, which was executed once the entire file was processed.
Once decoded, theJavaScript code led to a fake Flash Player update recommendation — a popular lure for social engineering attacks. The popup was related to the Domen social engineering kit, and clicking the “Update” button would initiate the download of malicious files.
Backdoor concealed in image file
In 2023, our Malware Researcher Ben Martin documented a website backdoor with a payload concealed in a seemingly benign image. The backdoor is typically uploaded to a compromised WordPress environment as the following fake plugins: core-stab and task-controller.
The malware’s footprint is tiny, including only a front.jpg file designed to look like an innocent image file. This extra step is taken to evade detection by security scanners, which often skip scanning image files for performance reasons. By keeping the malicious footprint small and generic, the backdoor can avoid detection from basic security scanners.
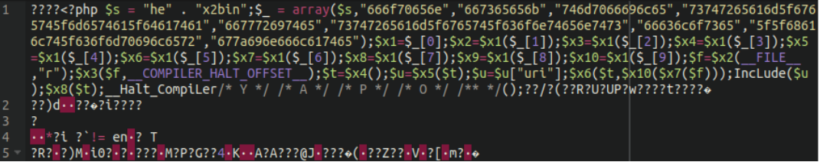
The core-stab and task-controller plugins contain two separate malicious samples that work together to assist attackers in compromising environments. The “core-stab” plugin includes the malicious front.jpeg image file containing an obfuscated remote code execution backdoor encoded with hex2bin and compressed binary data.
How to detect steganography on your website
Steganalysis, AKA the practice of detecting steganography, can be accomplished with tools like StegAlyze and StegExposure, while some analysts choose hex views to detect file anomalies. However, uncovering files on your website that have undergone steganographic manipulation can be a daunting task if you don’t have extensive experience in this field.
The good news for webmasters is you don’t have to be able to decode or understand exactly how obfuscation techniques work to find and remove malware on your website. It doesn’t matter if it’s steganography, a website backdoor, or some other form of malware — a simple integrity control solution is enough to detect these unwanted modifications in your files so you can take action to protect your environment.
Whenever you review changes and are not sure whether it’s malicious or not, the safest approach is to revert the file to the known clean version — you do have a website backup, right?
As a parting note: if you believe your website has been infected with malware, you can leverage our malware cleanup services to find and detect malicious code in image files, along with any malware on your server or at the client level.
Questions about steganography or detecting website malware in general? Reach out – our analysts love to chat!