Single sign-on (SSO) allows users to sign into a single account (e.g Google) and access other services like YouTube or Gmail without authenticating with a separate username and password.
This feature also extends to third party services such as the popular Dropbox file sharing application, which offers users the option to access their account using Google’s authentication from their sign in page.
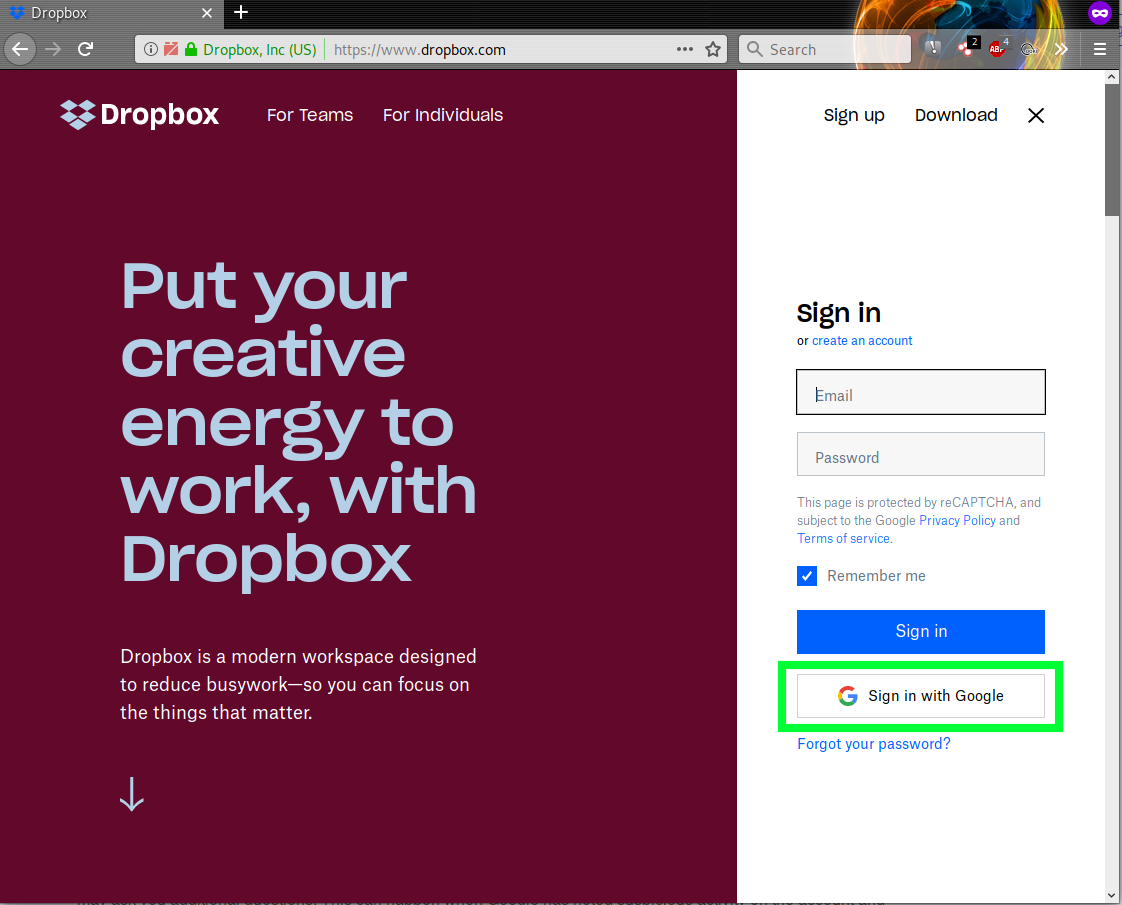
Malicious Pages Mimic Popular Login Workflows
SSO is very convenient for most users. It means they don’t need to manage an ever-increasing list of login credentials, and can instead use a single login credential to authenticate with various services.
Unfortunately, the increasing availability and adoption of SSO on popular websites also appears to have led to an increase in phishing pages.
These malicious pages replicate popular services’ login processes like Dropbox or Docusign. Instead of logging in to the intended service, the users’ SSO login credentials are phished and passed off to bad actors.
Replicated Login Process in Phishing Campaigns
The phishing pages inform users that they can log into a third party service (like Dropbox) by using their SSO email account from one of the popular providers seen below.

The only providers included on this phishing page that actually provide any sort of SSO service are Google and Microsoft.
Prior to SSO’s popularity, this was not common phishing tactic – it would be highly unusual for someone to enter their email address and password when they were trying to log into a third party service.
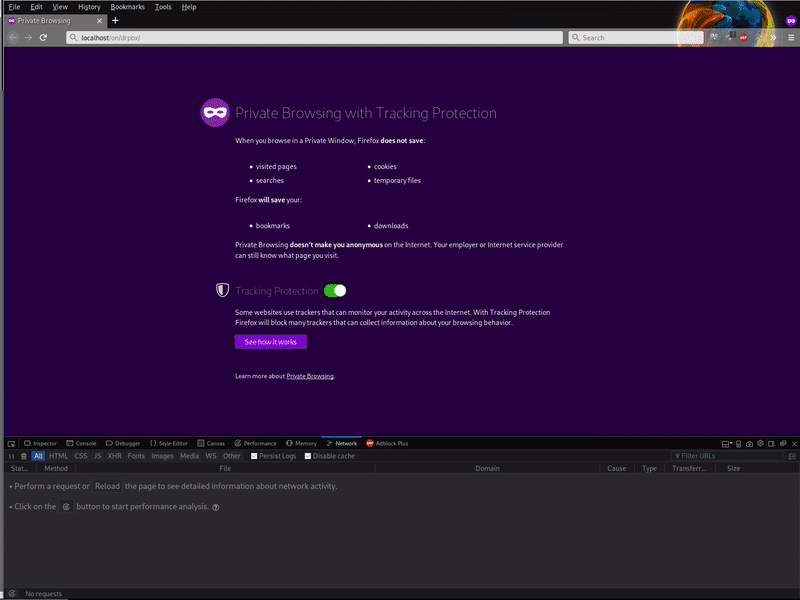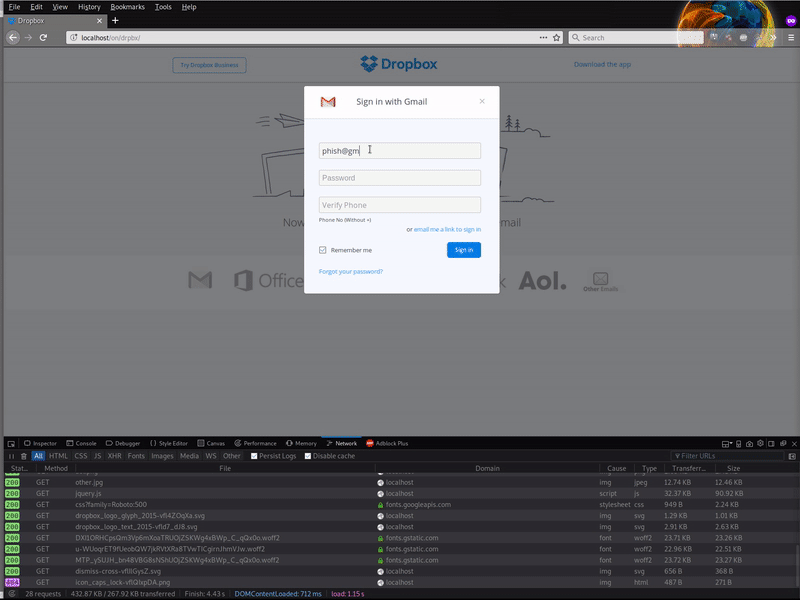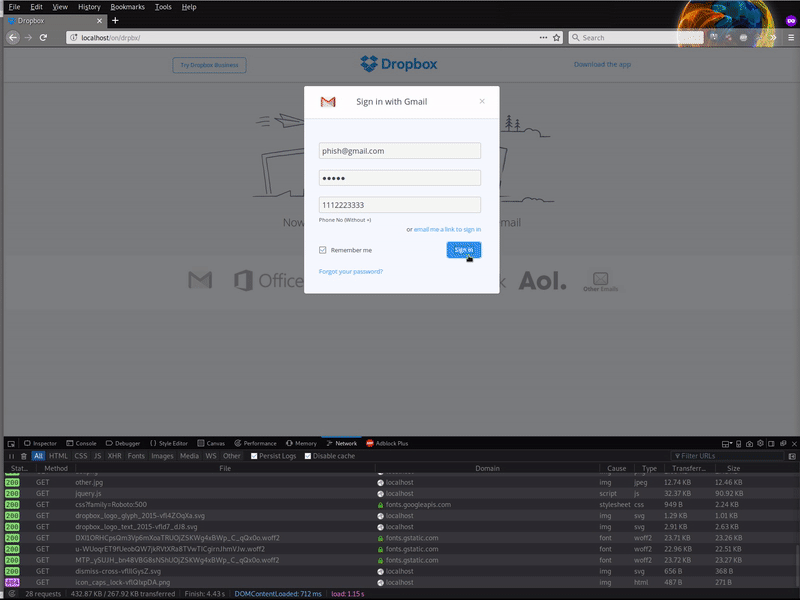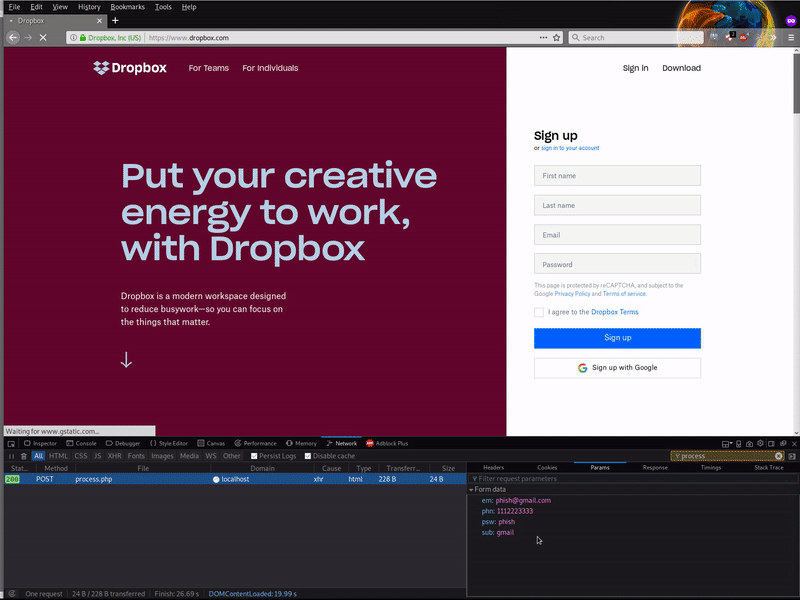
The CSS and a few images are missing from the original phishing page, so it doesn’t look as originally intended, but we can still see references in the actual index.php for the phishing page.
In the past, phishers would commonly set up individual phishing pages tailored to replicate the login page of each email provider. For example, the phishing pages for Google, Hotmail, or AOL would exist in various subdirectories so that campaigns can replicate the address bar URL of each targeted service.
Conclusion & Risk Mitigation
This post demonstrates how bad actors experiment with new phishing methods to trick humans into becoming victims and revealing their personal information.
To mitigate damage in the event that your login information is compromised, the best solution is to use 2FA authentication.
Two factor authentication makes it much more difficult for bad actors to access your account, as they require a secondary authentication method to complete the login process. We suggest avoiding SMS authentication whenever possible, as SMS messages can be intercepted and are not as secure as other multi-factor authentication methods.