HSTS or HTTP Strict Transport Security is a protocol that can make it more difficult for attackers to modify or intercept traffic between a user and your website. Understanding what HSTS is and how it functions is crucial for anyone keen on protecting their site, as proper implementation can help to ensure that your website’s visitors are protected from attacks.
In this post, we’ll take a closer look at this feature, benefits and advantages to enabling it on your web server, and how to implement it in Apache, NGINX, and the Sucuri Firewall.
Contents:
- What is HSTS
- Why HTTPS alone doesn’t cut it
- Understanding HTTP Strict Transport Security
- How to enable on your web server
- How to test if HSTS is enabled
- Disabling HSTS in Chrome
- Advantages and limitations of using HSTS
What is HSTS?
HSTS stands for HTTP Strict Transport Security. It’s a web server directive that dictates browsers to only connect via HTTPS, ensuring a secure connection by default. This significantly minimizes the risk associated with the unencrypted HTTP connections, making it harder for attackers to exploit the connection.
Why HTTPS alone doesn’t cut it
HTTPS is a robust security protocol that encrypts data in transit, making it difficult to spy on malicious actors. However, due to a small technical issue, HTTPS may be vulnerable to man-in-the-middle attacks.
When a visitor types in your website address, their browser initially attempts to connect via HTTP and only switches to HTTPS after receiving a directive from your server. This brief moment of vulnerability, known as SSL stripping, is where attackers can swoop in and hijack the connection.
The following figure demonstrates an SSL stripping attack in action:
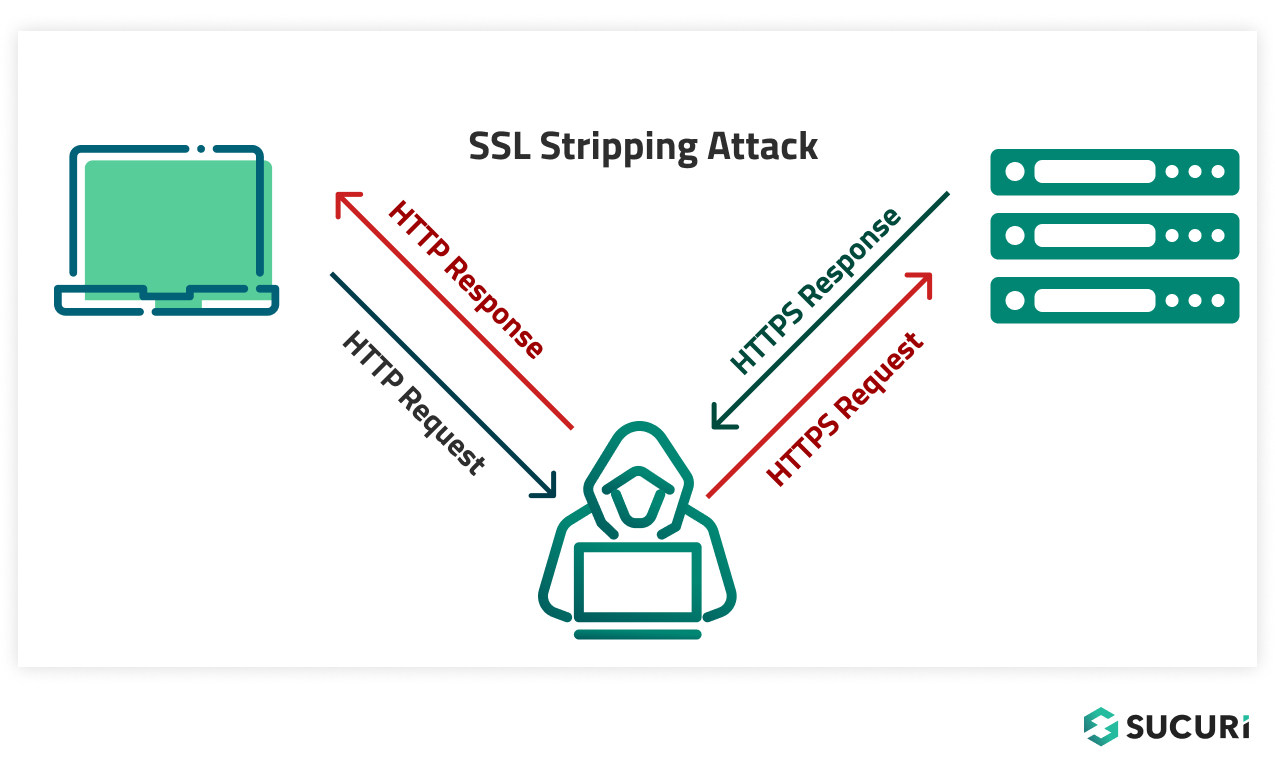 Here, the web server accepts only HTTPS requests. However, the browser is unaware about it, and hence it sends an HTTP request. The attackers hijack all HTTP traffic to their machines.
Here, the web server accepts only HTTPS requests. However, the browser is unaware about it, and hence it sends an HTTP request. The attackers hijack all HTTP traffic to their machines.
Once they receive the HTTP request they grab the request data and then repackage it into HTTPS request before sending it to the server.
Since the server does not have any identity of the sender, it responds back with the HTTPS response, which is again intercepted by the attackers to farm out data, and then the attackers convert that HTTPS request to HTTP before sending it to the original sender.
In this way, despite having an SSL certificate, both server and client are ignorant about the traffic interception going on somewhere in between.
Understanding HTTP Strict Transport Security
When a website has HSTS enabled, it strictly instructs the browser saying, “Only connect to me via HTTPS“.
This instruction gets cached in the browser, so the next time the user visits the site, the browser skips the initial unsecured handshake and jumps straight to a secure HTTPS connection.
Let’s understand how it works with a diagram:
- Step 1 – A user requests a website abc.com from the browser. By default, the request goes to http://abc.com
- Step 2 – The server responds by sending a ‘301 redirect’ to https://abc.com
Now, if it was just a normal HTTPS website, this cycle will be repeated for every HTTP request sent by the user.
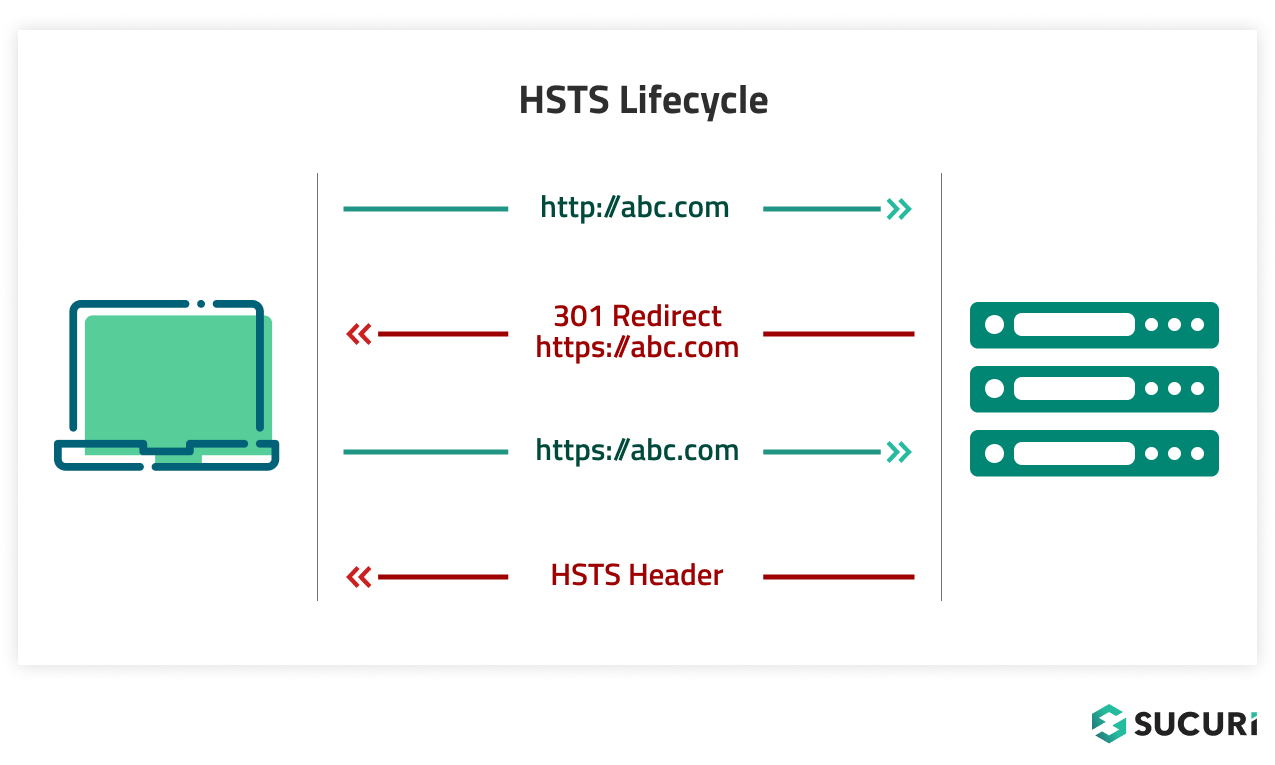 Once HSTS is enabled, the website instructs browsers to bypass the initial insecure HTTP connection altogether and jump straight to HTTPS.
Once HSTS is enabled, the website instructs browsers to bypass the initial insecure HTTP connection altogether and jump straight to HTTPS.
The HSTS header syntax
The HSTS header is added to the HTTP response headers from your server with a syntax like so:
Strict-Transport-Security: max-age=<expire-time>; includeSubDomains; preloadLet’s dissect the components of this header.
1. max-age:
This is the duration for which your website should be accessed exclusively over HTTPS. It’s specified in seconds. For instance, max-age=31536000 instructs the browser to access the site securely for the next 1 year (31,536,000 seconds).
2. includeSubDomains:
When included, this option extends the HSTS policy to all subdomains of your website, ensuring comprehensive security. Without this option, only the exact domain specified in the HSTS header is protected.
3. preload:
This option is a consent from the site owner to be included in the HSTS preload list, which is a list of websites hardcoded into browsers as being HTTPS-only. However, before opting for preload, it’s vital to understand the implications and ensure that your site will remain available over HTTPS indefinitely.
How to enable HSTS on your web server
Enabling HSTS on your web server is a proactive step towards bolstering the overall security of your website.
Enabling HSTS in Apache
Follow these steps to enable HSTS for Apache:
- Access your virtual hosts configuration file (usually /etc/apache2/sites-available/default.conf) and go to the block <VirtualHost *:443>.
- Add the following code in the block:
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
- Restart your server.
Enabling HSTS in NGINX
Follow these steps to enable HSTS for NGINX:
- Open the configuration file for your Nginx server, generally located at /etc/nginx/sites-available/default or /etc/nginx/nginx.conf.
- Locate the server block for your website.
- Add the following line within this block:
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains"- Restart your server.
Enabling HSTS in the Sucuri Firewall
Enabling HSTS in Sucuri Firewall takes just a couple of clicks and does not require any modification in the configuration files of your servers.
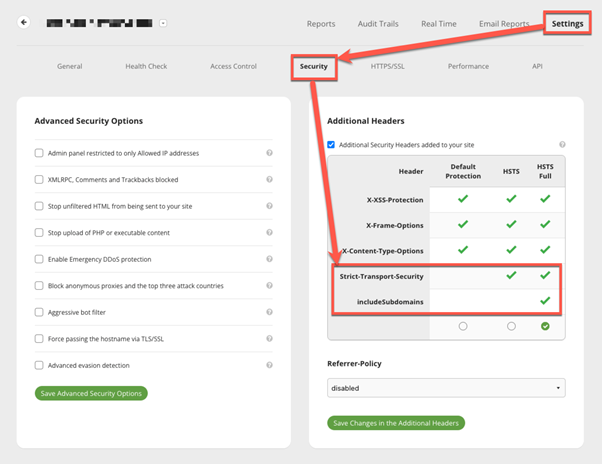
- To enable HSTS in Sucuri Firewall, go to Settings → Security → Additional Headers.
- Check the options “Strict-Transport-Security”.
- If you have subdomains, check “IncludeSubDomains”.
How to test if HSTS is enabled
Testing whether HSTS (HTTP Strict Transport Security) is enabled and functioning correctly on your website is a vital step to ensure that your security configurations are in place. Here’s how you can go about it:
1. Online tools
There are online tools such as the Qualys SSL Labs Server Test or the HSTS Preload Checker that you can use to test HSTS.
Simply enter your website URL, and these tools will provide you with a detailed analysis, including whether HSTS is enabled.
2. Browser developer tools
You can use the developer tools in your browser to check the headers returned by your website.
- Navigate to your website in your browser.
- Right-click anywhere on the page and select ‘Inspect’ or press `Ctrl+Shift+I` (or `Cmd+Opt+I` on Mac).
- Go to the ‘Network‘ tab.
- Reload the page (press `F5` or `Cmd+R` on Mac).
- Click on the first request made to your website in the list.
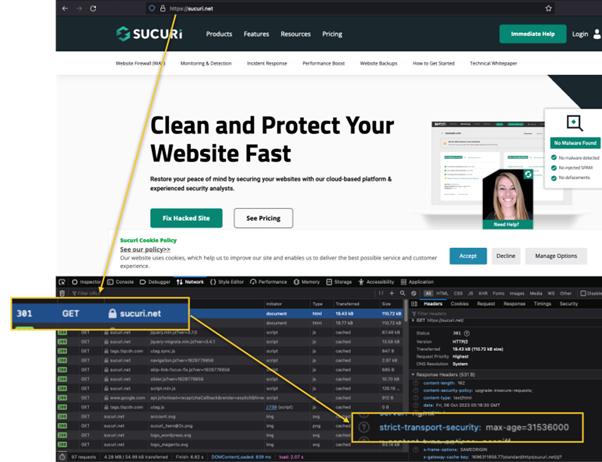
- Look for a response header named `Strict-Transport-Security`. If it’s present, HSTS is enabled.
3. CommandLine with cURL:
You can use the cURL command-line tool to check the headers of your website.
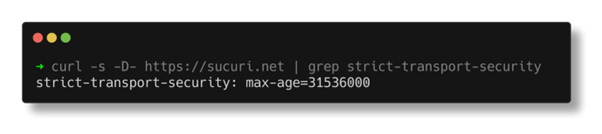 If HSTS is enabled, you’ll see a line starting with `Strict-Transport-Security`.
If HSTS is enabled, you’ll see a line starting with `Strict-Transport-Security`.
These methods provide a straightforward way to verify that HSTS is active and configured properly, ensuring that your website maintains a secure environment for its visitors.
Remember, a properly configured HSTS setup is a strong statement of your commitment to website security.
Disabling HSTS in Chrome
Though it’s a rare necessity, there could be instances where disabling HSTS (particularly in Chrome) becomes essential.
Here are the steps you can use to disable HSTS in Chrome:
- Open Chrome: Fire up your Chrome browser.
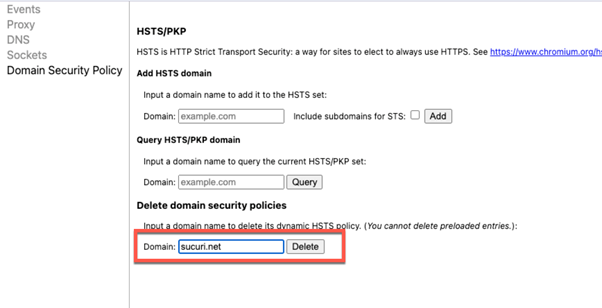
- Type in the Address: Key in chrome://net-internals/#hsts in the address bar.
Enter Domain: Scroll down to the ‘Delete domain’ section, type in the domain name you wish to clear HSTS for, and hit the ‘Delete‘ button.
Advantages and limitations to using HSTS
There are a number of clear advantages to using HTTP Strict Transport Security. HSTS doesn’t wait for the initial insecure handshake to happen. Instead, it instructs browsers to directly establish a secure connection, leaving no window for SSL Stripping to intercept.
Browsers remember the HSTS instruction from previous visits. So, even if a user manually types in an HTTP address or clicks on an HTTP link, the browser knows to override that and use HTTPS instead.
HSTS can be configured to secure all subdomains as well without any additional configuration. Some websites go a step further and enlist in HSTS Preload lists. This is a list of websites known to require HTTPS, and modern browsers come pre-loaded with these lists, ensuring that the first-ever connection to the site is secure, closing the loophole that attackers could exploit.
And while HSTS enhances website security, it’s also important to be aware of its limitations. HSTS can tag browsers with identifiable information from super cookies when visiting an HSTS-enabled website, posing privacy concerns as this information can persist even in privacy modes and be used to identify visitors across different domains.
Additionally, HSTS doesn’t prevent DNS-based attacks, where attackers utilize misleading or artificial domains not on the HSTS Preload list. HSTS is also ineffective against advanced attacks targeting the Transport Layer Security (TLS) protocol, such as the BEAST or CRIME attacks.
Closing thoughts
In summary, HTTP Strict Transport Security (HSTS) is a critical protocol that enhances your website’s security and safeguards your site’s visitors.
Understanding how it works and correctly implementing it on your web server, be it via Apache, NGINX, or from Sucuri Firewall, can significantly boost your website security.
Despite its advantages, it’s important to be aware of HSTS limitations and take additional measures to address them. Testing your HSTS setup and ensuring its proper configuration is crucial.