Every year we see an increase in website attacks during the holidays.
While business owners see their sales go up due to promotional Black Friday and Cyber Monday campaigns, hackers are in the background working nonstop to create malicious, fraudulent websites as well as take advantage of legitimate ones.
Main Cyber Monday Threats
Phishing Pages
One of the major risks to consumers is phishing campaigns.
Carefully crafted phishing login pages convince users they are logging into a valid service. When users fail to notice the login page is fake, attackers receive their login details or credit card information. The stolen credentials and personal information are then used to perform identity theft and fraudulent activities.
If you believe you have been a victim of a phishing campaign, act quickly. Here are the main actions you should do first:
- Change your passwords
- Adopt a multi-factor credential (if available)
- Check your bank account for unusual transactions
- Block your credit card
- Contact the site where the phishing page originated
In most cases, phishing lures are a simple copy of a login page for Facebook, Google, banks, insurance companies, and others.
To produce almost identical copies of the original login page, attackers can include:
- locally-stored images,
- CSS,
- Similar domain names using typos or phrases (even using HTTPS)
- JavaScript.
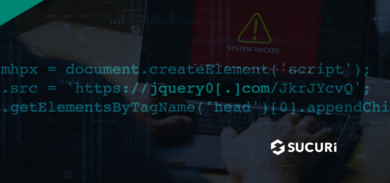
The main difference between a legitimate page and a phishing page is the malicious PHP scripts. These scripts send the username and password directly to the attacker.
The biggest challenge phishing injections pose to website owners is that they are difficult to detect. The fake page uses valid codes in nefarious ways that can fit perfectly within the construct of websites.
Attackers know this and further complicate the process by embedding the pages deep within the file structure of your website.
To address this, it’s important you’re actively monitoring the integrity of your site files and directories.
If you suspect your website is a part of a phishing lure campaign, let us know. We’d love to clean your site and help in any way we can.
Phishing Email Campaigns
Phishing email is a basic social engineering tactic consisting of emails that trick users to perform an action. At first glance, these emails appear to be benign, but there is always a trick.
In September, we were notified of phishing emails targeting WordPress users. The content informed site owners of a required database upgrade.
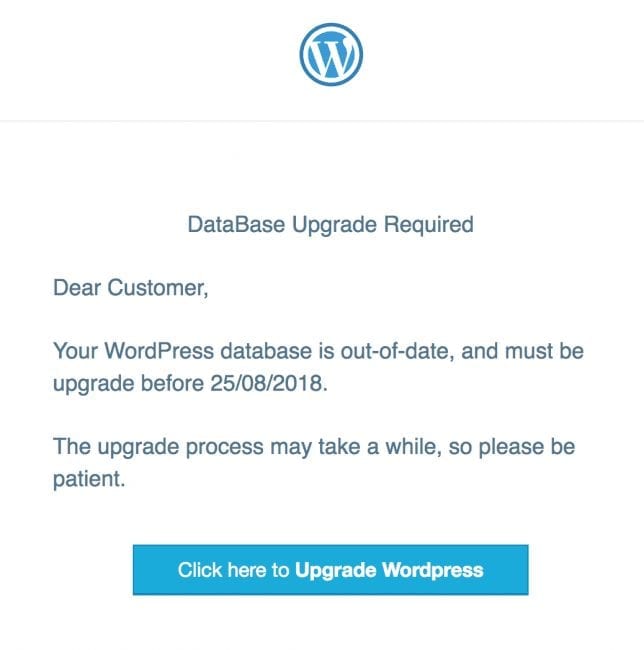
Even though the email looked quite similar to a legitimate WordPress update message, there were some red flags:
- Sender
- Typos
- Suspicious messaging style
- Timestamp format
In order to avoid being a victim of phishing emails, follow these advised steps:
- Never trust an email that asks you to perform an action you didn’t request, especially if you haven’t received this type before.
- Verify that the sender matches the content in the email.
- Check the content for typos.
- Watch out for poor formatting.
- Inspect URLs for legitimate domain names.
As a website owner, you should be aware that mailers are a category of scripts bad actors install to distribute spam emails and phishing campaigns.
Here at Sucuri, we find mailers sending unwanted emails in large batches in about 19% of all compromised websites we clean up.
Support Scams
A technical support scam refers to fraudulent activities in which a scammer claims to offer a legitimate technical support service. The first support scam dates back to 2008 using a call center in India. Unfortunately, this type of attack has become more popular.
The main objective of the scammer is to gain remote control to the victim’s computer in order to retrieve sensitive information, such as banking data.
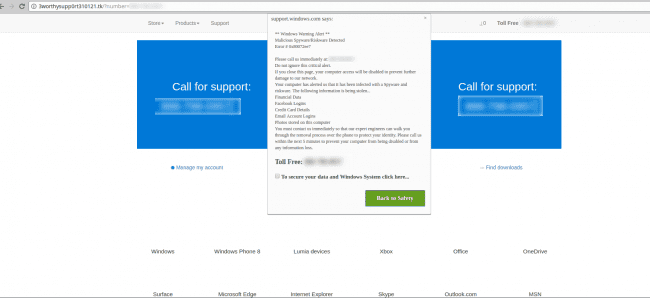
Last December, we saw a massive WordPress campaign in which the attackers used a malicious reverse JavaScript injection to redirect visitors to a support scam.
The campaign attempted to redirect visitors to a bogus Windows support page claiming that their computers were infected with ‘riskware’ and would be disabled unless they called a bogus support hotline.
This year, we have seen a massive tech support scam malware campaign that uses multiple different vectors to inject malicious scripts into WordPress websites. You can take a look at the following blog posts to understand what vectors have been used so far:
This malware campaign is still evolving. If you have a WordPress website, make sure it is secured against threats.
Credit Card Stealers
The end of the year is hackers favorite time to infect ecommerce websites with malware. It is Black Friday week and we expect credit card stealers to ramp up their campaigns as they do every year.
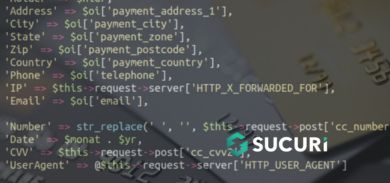
Also known as credit card swipers, credit card stealers inject a piece of malware into the checkout process which leads to payment information theft such as credit card information and other electronic payment systems credentials.
Card swipers are often injected by attackers who exploit vulnerabilities in website software and extensions. Many attackers will exploit website months in advance and inject a backdoor to retain access. It’s a matter of time before attackers execute the campaign to steal sensitive or personal information from infected ecommerce websites.
Depending on the type of infection, the hacker can retrieve the content of every POST request that contains the stolen data being sent to the malicious email account or server for storage.
Last October, we found a piece of malicious code used to steal credit card information from compromised Magento sites.
As we approach the holidays, we expect to see a rise in attacks on ecommerce sites. Hackers are getting ready to take advantage of the increase in online shopping being done throughout the next few months.
As a website owner, you can take some actions to reduce the risks of having your ecommerce website compromised:
- Keep your software up to date or virtually patched with a website firewall.
- Constantly monitor your website.
- Use good account management, such as strong passwords and the principle of the least privileged access.
Malware Downloads on Ecommerce Websites
Malware downloads is a type of attack that distributes unwanted software to visitors.
During the holidays last year, we cleaned an ecommerce Magento site that was serving malware to customers who were trying to purchase electronics.
While the website appeared innocent at first glance – it didn’t contain spam, adult content or host file-shares like a lot of malware-ridden sites–performance was significantly slower than usual.
Alongside the performance issues, an unexpected executable labeled plugin.exe was downloaded as soon as the webpage loaded. This behavior was a red flag for a compromise.
Fighting against “Unwanted Software” is a challenge, but you are not alone. Various types of “unwanted software” are widely spread and Google has been actively fighting against them since 2014.
Google’s has created a list of main unwanted software characteristics that you can take a peek of:
- It is deceptive, promising a value proposition that it does not meet.
- It tries to trick users into installing it or it piggybacks on the installation of another program.
- It doesn’t tell the user about all of its principal and significant functions.
- It affects the user’s system in unexpected ways.
- It is difficult to remove.
- It collects or transmits private information without the user’s knowledge.
- It is bundled with other software and its presence is not disclosed.
How to Prevent Suffering from Attacks
In order to avoid such attacks, we highly recommend that you use best practices with your website security.
- Use strong and unique passwords for every element of your site: hosting, CMS, payment services, etc.
- Have some integrity control of files and the database. This will help you detect unauthorized modifications. Our free WordPress security plugin offers integrity monitoring.
- Don’t host your ecommerce site on the same hosting account with other sites. The better the isolation from the rest sites, the fewer chances one of the less secure neighbor sites will be the point of penetration for your important ecommerce site.
- Use a website firewall — it will protect your sites from many web-based attacks. Ideally, the firewall should be actively maintained and updated so that no new types of attacks could bypass it.
- Monitor your website for security issues, both on the client-facing frontend, and the server-side backend.
Conclusion
Tis the season to see your sales rise and we understand that you are counting on your website to help you achieve your sales goals.
Don’t let the malicious actors take advantage of your online business. Make sure to protect your website and your visitors.