Continuing a series on how to better strengthen your personal online privacy, we are looking to take personal inventory of how we connect online. These were themes covered during our webinar “Security Beyond Your Website: Personal Online Privacy” and in a Twitter conversation (through the #Digiblogchat weekly forum) on this same topic.
The first posts in this short series aimed at answering:
Now let’s talk about: How much of a digital footprint are we leaving behind?
Online Account Management
The online account management best practice principle is straightforward – review or delete account information where necessary. Often that comes in the form of getting rid of old accounts we forget we made. For example, I can still vaguely remember that I used LiveJournal on a daily basis.
If you’ve seen any of my webinars, you know that I tout “If you don’t use it, lose it” probably more than anyone. Well, you can use that same philosophy for online accounts!
So what can we do to review our online history?
Google Search for Usernames
Go online and search for your username. If it’s unique enough, you might end up seeing it pop up in search results. Here is an example of what happened with mine:
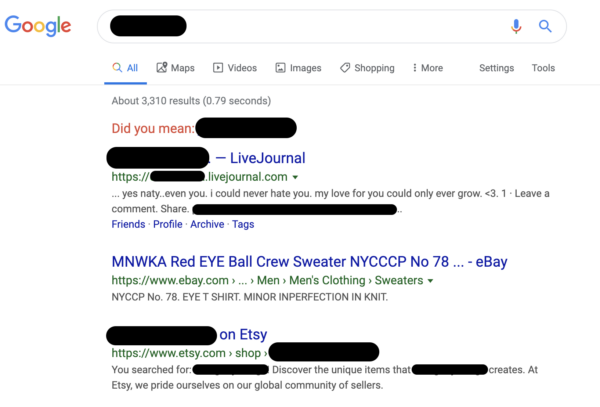
I’ve blocked out the important details here but just as interesting:
As I mentioned: LiveJournal. Oh, goodness but I also forgot I created an Etsy account. I don’t intend to use it so best delete it. I’ll get right on that!
Inbox Search
Look through your old emails. It will be easy enough to identify where you’ve logged into when you’re likely getting marketing campaigns being sent to your inbox; or receiving important account updates.
If you’re getting updates from somewhere, you’ve probably logged in at some point. It does seem odd that my personal email has received 80 emails from The Care.com Team and I can’t remember the last time I logged in there.
Go Through Your Saved Logins (LastPass)
If you’re using LastPass or KeePass, go through your entire inventory to see what you have in there. As an example, I performed a recent personal cleanup through LastPass.
I decided to perform their Security Challenge found in their main panel, see:
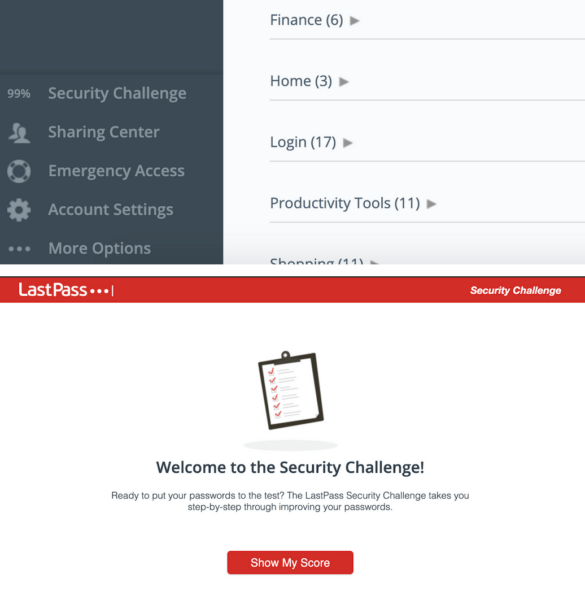
It’s a very useful measure of the strength and complexity of your password inventory. You can read more on what comprises their scoring.
So my initial review produced the following results:
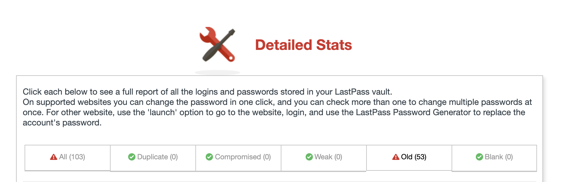
So I had 53 passwords that were older than six months! I needed some major review of 103 accounts. As I was doing my cleanup, I realized I did not need nearly 20 of those accounts. So I went online and deleted those accounts outright which produced:
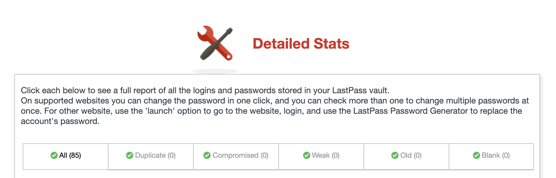
I’m in a much better position now than I was before I did this purge.
You’ll notice that LastPass also offers other important insights into the overall quality of the password you’re generating for your accounts. Here are some key highlights:
- Duplicates: Ensuring you’re not re-using the same password for different accounts.
- Weak: Ensuring the passwords are following strong best practices.
- Old: Ensuring passwords are not older than a year, as an example.
Additional Online Resources
I’ll also highlight using something such as haveibeenpwned.com as an online resource. It’s really effective because it will also provide an indication if your email may have been compromised in a prior data breach, which we read often in the news.
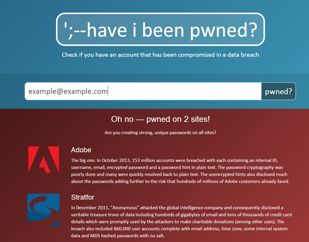
If you see anything produced from the results, you know to review those accounts as well. Whether it’s deleting them, resetting your password and enabling multi-factor authentication.
Deseat.me is another resource for which sites have an active online account with you. It works by finding emails confirming your signup from different services provider.
A10. As a UK Cyber Champion (not a term I refer to much) this link is good: https://t.co/5bP9ZX7V1u #digiblogchat
— Larry Mount (@LazBlazter) October 1, 2019
Larry Mount offers another great resource with Stay Safe Online’s guidance on identifying hacked online accounts.
Conclusion
Apple’s CEO, Tim Cook was once quoted;
“If you put a key under the mat for the cops, a burglar can find it, too. Criminals are using every technology tool at their disposal to hack into people’s accounts. If they know there’s a key hidden somewhere, they won’t stop until they find it.”
Data is a major commodity these days. Why? Because that’s access to your financial information, or whatever socio-political motivations that your information can help exploit. Data is everywhere and it’s ultimately our responsibility to ensure that if you no longer have an account with Capital One, delete all pertinent information.
You will find that these extra steps are reassuring in a world where data security threats are real. If you are interested in website security, sign up to receive information on the latest threats. Stay safe online!