Continuing a series on how to strengthen your personal online privacy, we are taking personal inventory of how we connect online. These were themes covered during our webinar on “Security Beyond Your Website: Personal Online Privacy” and during a Twitter conversation (through the #Digiblogchat weekly forum).
The first post in this series answers the question: How are we connecting online? Today we are going to answer: How can we stay safe and keep our data private?
Data Privacy Best Practices
After connecting to our WiFi router via our device of choice, we’ll typically enter some interface or browser to start visiting the very websites Sucuri help protect from hackers.
However, that browser is one of the most common reasons for infections. Most viruses, ransomware, and unwanted programs are spread by visiting hacked or malicious websites through the browser. Therefore, we need to ensure that this is properly secured.
Update Your Browser
For Firefox and Chrome, two of the most popular browser applications, the instructions are essentially identical:
Go to Firefox > About Mozilla Firefox

Go to Chrome > About Google Chrome
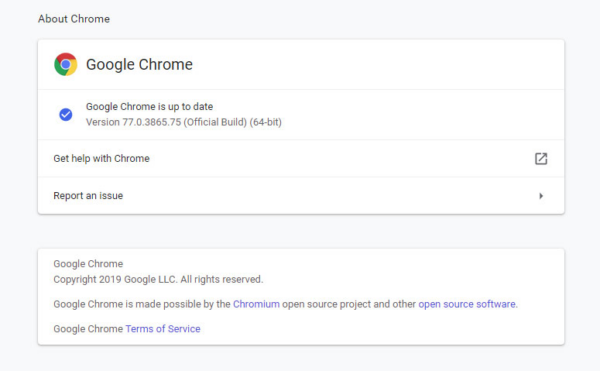
Make sure the browser is up to date, so you know you are using the current version. Like your website, it’s important to keep software updated for the latest security patches.
Be sure to use this precise method to verify accurate updates. We described earlier this year how a malicious campaign injected scripts that pushed fake browser updates onto site visitors. This helped distribute ransomware or bank malware through small .JPG images that would’ve been normally dismissed based on their small size.
Browser Fingerprinting
Cookies can provide an interesting function for businesses. When you visit a website, third-party trackers (cookies, web beacons, flash cookies, pixel tags, etc.) get stored on your computer. Most companies will use these trackers to fingerprint a browser
Cookies can collect a lot of information about somebody; including:
- IP
- Browser history
- Screen size
- Time-zone
- Plugins
- Operating system
There are various browser tools that can help protect personal data by denying that tracking capability. For example, Panopticlick is a site which will analyze how well a browser and add-ons protect a user from online tracking. It will initiate a scan in an effort to answer questions such as:
- Is the browser blocking tracking ads?
- Is the browser blocking invisible trackers?
- Does the browser unblock third parties that promise to honor Do Not Track?
So what happens if you answer “No” to any of those questions? One tool I’m actively using is known as “Privacy Badger”.
Here is an example of the types of attempted trackers faced when visiting ESPN.com:
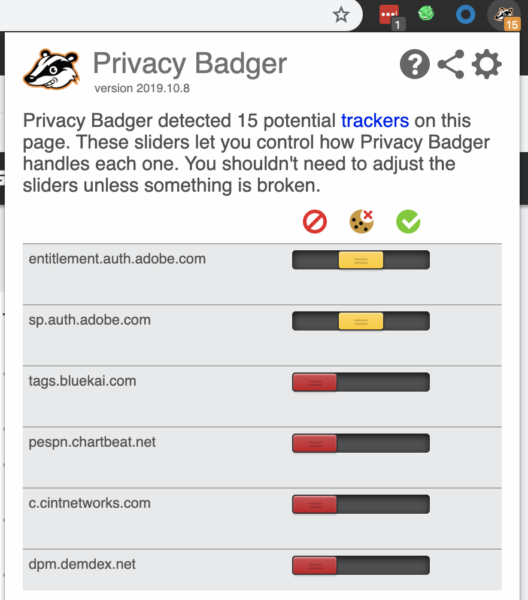
There are 15 trackers.
How can Privacy Badger help? If an advertiser seems to be tracking you across multiple sites without your knowing, Privacy Badger automatically blocks them from loading any more content in your browser.
Cookies & Data Collection
Hackers can abuse cookies. We actually wrote about a case of fake malicious cookies detailing how an attacker stole active cookies, and then pretended to be that user (hijacking that user’s session). Once done, they were able to perform any actions an administrator-type user has permissions to perform.
Imagine stealing the keys and ID of a Brinks truck driver and walking into a jewelry store to “transport” (read “steal”) valuables, which can be very dangerous.
Having said that, most online accounts will automatically log out users after a certain period of inactivity. If you’re an administrator or someone with sensitive access, I would clear your cookies regularly.
On Google Chrome, you can control how cookies and site data are managed by visiting:
chrome://settings/content?search=data
On Mozilla Firefox, you can visit the Privacy & Security section to do the same by visiting:
about:preferences#privacy
Password Management
Let’s say you are logging on to your website. Well, first thing is making sure that we’re always instilling this principle of exercising strong passwords for entry into any site — and we’ve already written about the best methods for creating a strong password. Whether it’s connecting to Facebook, or going to Amazon to buy something, or getting on Salesforce for work purposes, we need to make sure that we’re using strong, long, complex, and unique passwords for each and every one of these access points.
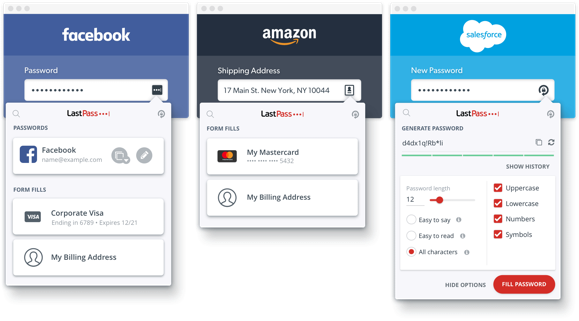
For management of these passwords, I’m going to use LastPass as an example, primarily because I use it. It’s not to speak ill of any other password keepers. I know that KeePass is another well-used one. I’m just very familiar with LastPass.
You’ll notice on the right-hand side, you can dictate what the length is and how many factors you’re using to generate unique passwords. I use 16-character passwords for my own purposes with symbols.
More interesting is you can just log into your main LastPass account, create your own master password which allows you to manage them all.
This means you only need to remember your master password. It makes it really easy. It’s also available on mobile and that way you can also take that same security experience from your desktop browser to your phone.
Multi-Factor Authentication
Personally, I believe that multi-factor authentication should be a requirement to navigate the internet safely going into 2020.
A strong password won’t always be sufficient. I use a second layer, whether it’s receiving some temporary one-time code on your phone via text, or using some type of tool like Google Authenticator to log on.

My wife and I often receive enough emails, say from Dropbox or Amazon or Instagram saying, “Hey, here is your reset token to reset your password.” We never did that. And so we know that someone’s trying to get in.
Of course, they won’t be able to because we’re getting some type of verification on our phones to validate those requests. If we didn’t, someone might’ve already compromised those accounts for us.
As I understand is, this is actually true for ALL security systems. In general, one is trading convenience for security. Of course, over time, developments can improve both, but at any stage of development, it’s a tradeoff. #DigiBlogChat
— John W Lewis (@JohnWLewis) October 1, 2019
As John Lewis describes, implementing new habits like these can often make connecting online inconvenient sometimes. However, that moment or two it takes for you to verify that you’re the true account owner will greatly minimize the risk that someone else will claim ownership of your data and assets.
In our next post, we’ll talk about what to do if an online account has already been compromised and how to retrace your digital steps to uncover accounts you likely forgot about before it’s too late. Sign up to our email feed and don’t stop learning about website security.