Every now and then I check my spam mail box for interesting malware (yes, I receive a lot of phishing messages and alerts that my payments are overdue), but most of the time is more of the same, effortless malware, lousy written messages and not fun to analyze.
Today I was bored (that time of the year that you need to write tons of reports, sorry boss…) and I decided to follow the trail of some of those links on the messages I got. And the first one was a “pleasant” surprise.
Usually I’d go with checking the message origin and writing about how it was sent and what was used to get control of the site, but this time I’ll write about other aspect. (If you are wondering, it is a WordPress site with a vulnerable revslider on the site’s theme that allowed the attacker to have privileged access to the site).
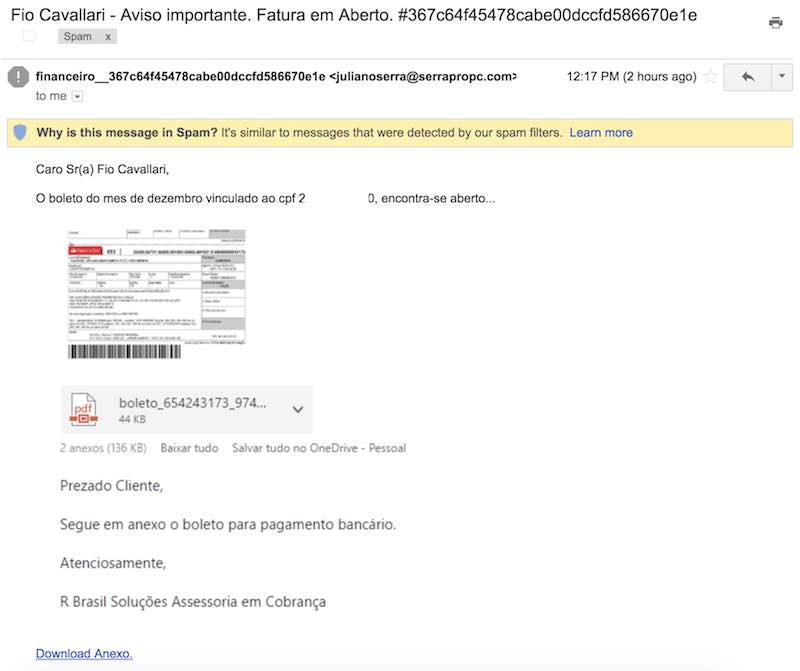
For those not fluent in Brazilian Portuguese, this message is telling that I have a payment overdue and a new “boleto” (a common barcode payment method in Brazil) is attached. The interesting part is that they are referring to me by my personal email alias and not the full name, however they got my CPF (Brazil’s Social Security Number) correct, probably it’s is related to some leaked data (not that uncommon here).
Everything on this message is clickable and all them will send you to the same Google shortened URL. Which translates to the Facebook’s fbsbx.com domain, which is used by Facebook as the domain where the attachments shared on chats and groups are stored.
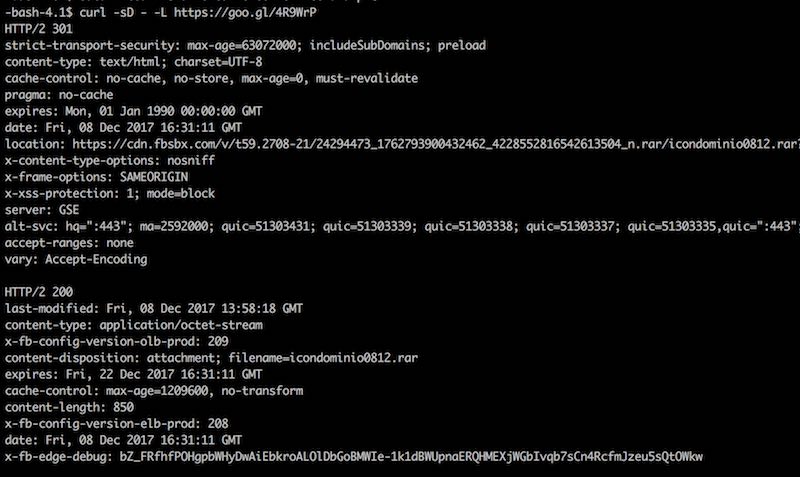
It is pretty interesting that they are relying on such services to “host” their files instead of using another hacked site to store the malware. I monitored this file and although the link was set to expire on Fri, 22 Dec 2017 16:15:47 GMT, it was taken down less than 24h after I receive the email scam, probably by a Facebook malware scan process.