In the past couple of years, we’ve been tracking a long-lasting campaign responsible for injecting malicious scripts into WordPress sites.
This campaign leverages old vulnerabilities (patched a long time ago) found in a variety of outdated themes and plugins. However, it also adds new vulnerabilities as soon as they are disclosed—like the recent Social Warfare and Yuzo-Related-Posts issue, as well as some zero-days.
The attack is known to redirect infected site visitors to various traffic monetization schemes, such as fake tech support scams. These bad actors have been using disposable .tk domains as intermediate destinations in their redirect chains for quite some time now.
New Monetization Channel: Pushka Browser Notification Scams
We’ve recently noticed the addition of a new monetization channel which sometimes replaces the .tk redirects — and sometimes complements it by using both .tk redirects and push notifications at the same time.
The redirects pass visitors along to various .info domains that belong to a PushKa browser notification scam.
Here is one of the many landing page variants that the injected scripts redirect to:
![Landing page on hxxps-__hellofromhony[.]org_f1](https://blog.sucuri.net/wp-content/uploads/2019/04/Landing-page-on-hxxps-__hellofromhony.org_f1.png)
Another obfuscated version of a script found on hellofromhony[.]org (and later on destinywall[.]org) has this code where a long array of numbers decodes to “hxxps://notifymepush[.]info/rs/1088?count=5&declCount=3&fullScreenMode=enabled&utm_source=clarkthread”.
![Obfuscated notifymepush[.]info redirect](https://blog.sucuri.net/wp-content/uploads/2019/04/Obfuscated-notifymepush.info-redirect-1.png)
Fake reCAPTCHA
Under normal conditions, site visitors are redirected to a page where they see a familiar picture with a reCAPTCHA logo and the following message:
“I’m not a robot. Click to Allow to confirm, that you are not a robot” (original spelling and grammar preserved).
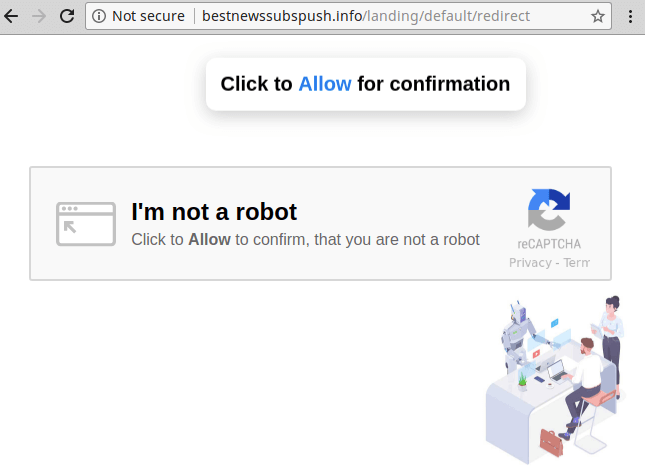
However, it doesn’t ask users to perform the usual reCAPTCHA interactions like clicking on a checkbox or selecting street signs.
The goal is to trick visitors into clicking “Allow” when the site asks to subscribe to push notifications. Once the call-to-action has been clicked, the spammers are able to send spam ads to the visitors’ desktops whenever they want — even if the user closes the website and never visits it again.
You can think about these push notifications as a more persistent type of pop-up advertisement.
Redirects
Regardless of whether a site visitor subscribes to the notifications or not, they’ll be redirected to one of the following subdomains on the ad-filled news-tap[.]com site:
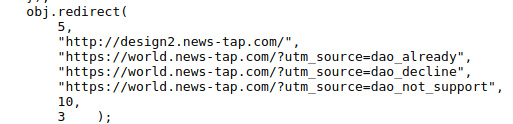
The “world.” subdomain masquerades as a “news” site with catchy headlines featuring last year’s news articles mixed with questionable ads.
![Old “news” and sketchy ads on world.news-tap[.]com](https://blog.sucuri.net/wp-content/uploads/2019/04/Old-“news”-and-sketchy-ads-on-world.news-tap.com-1.png)
![Ads on design2.news-tap[.]com](https://blog.sucuri.net/wp-content/uploads/2019/04/Ads-on-design2.news-tap.com-2.png)
Unsubscribing from Push Notifications
If you have accidentally subscribed to unwanted push notifications, there is a way to remove them from your browser settings.
You can find detailed instructions by Googling for [remove browser push notifications <your browser>] and replacing <your browser> with the name of the browser you use — for example, “Chrome” or “Edge”.
PushKaWrapper
To work with browser push notifications, malicious sites use the so called PushKaWrapper library. PushKa is a “word play” around the English word “push” and Russian “пушка” (pushka), which means “cannon”.
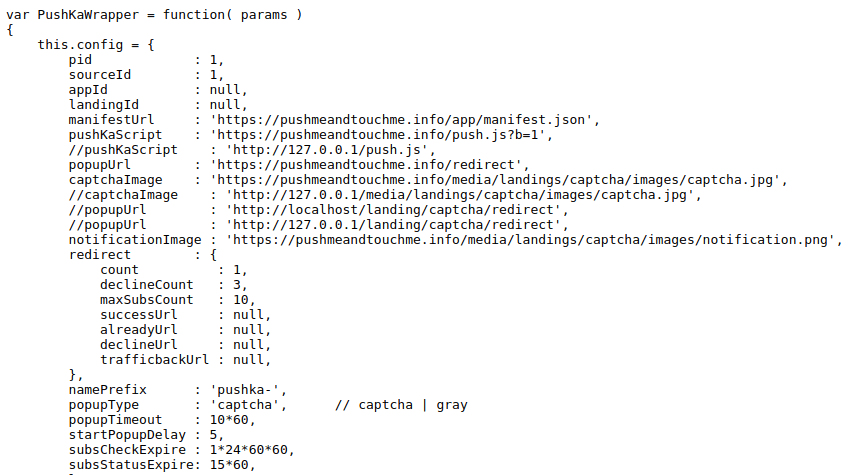
Note how this code is designed to work with fake CAPTCHA images.
Domains
The push notification scam campaign itself is not new and has been active since at least last year. Here are just some of the domains used by this campaign:
- 101newssubspush[.]info
- Bestofnewssubspush[.]info
- Burningpush[.]info
- Checkadvisefriends[.]info
- Checksayfriends[.]info
- Checksuefriends[.]info
- Conewssubspush[.]info
- Enewssubspush[.]info
- Examinenotifyfriends[.]info
- Gonewssubspush[.]info
- Hitnewssubspush[.]info
- Inewssubspush[.]info
- Inspectnotifyfriends[.]info
- Justnewssubspush[.]info
- Livenewssubspush[.]info
- Metanewssubspush[.]info
- Newnewssubspush[.]info
- Notifymepush[.]info
- Nunewssubspush[.]info
- Pushmeandtouchme[.]info
- Scannotifyfriends[.]info
- Searchnotifyfriends[.]info
- Testnotifyfriends[.]info
- Thentouchme[.]info
- Topnewssubspush[.]info
- Touchthenpush[.]info
- Trynewssubspush[.]info
- Upnewssubspush[.]info
- Usenotifyfriends[.]info
- Wenewssubspush[.]info
Alternative redirect destinations include:
hxxps://click.newsfeed[.]support/esuznxifqk and hxxps://click.newpush[.]support/esuznxifqk.
Conclusion
Hackers try to maximize the profit of their campaigns by diversifying the approaches that they use to monetize traffic from infected websites. Not all traffic comes from countries where people can pay for the removal of nonexistent security threats — even if scammers manage to trick them into believing they need it. Given the global nature of website infections, hackers try to monetize traffic from less wealthy countries by using a variety of sketchy ad networks.
With conventional pop-ups or redirects, a user is typically only exposed to ads once. With push notification schemes like the one seen above, bad actors likely expect that a fraction of users will subscribe and get constantly spammed with browser notifications indefinitely, or until they figure out how to unsubscribe. As a result, they can expect more click-throughs for every visitor who is redirected from a compromised website.
As long as hackers can find a way to monetize traffic, they will continue to actively compromise and infect websites. Webmasters should do their best to protect and monitor the integrity of their websites. If you suspect that you have been hacked, we offer a range of security solutions to help you recover and secure your site.