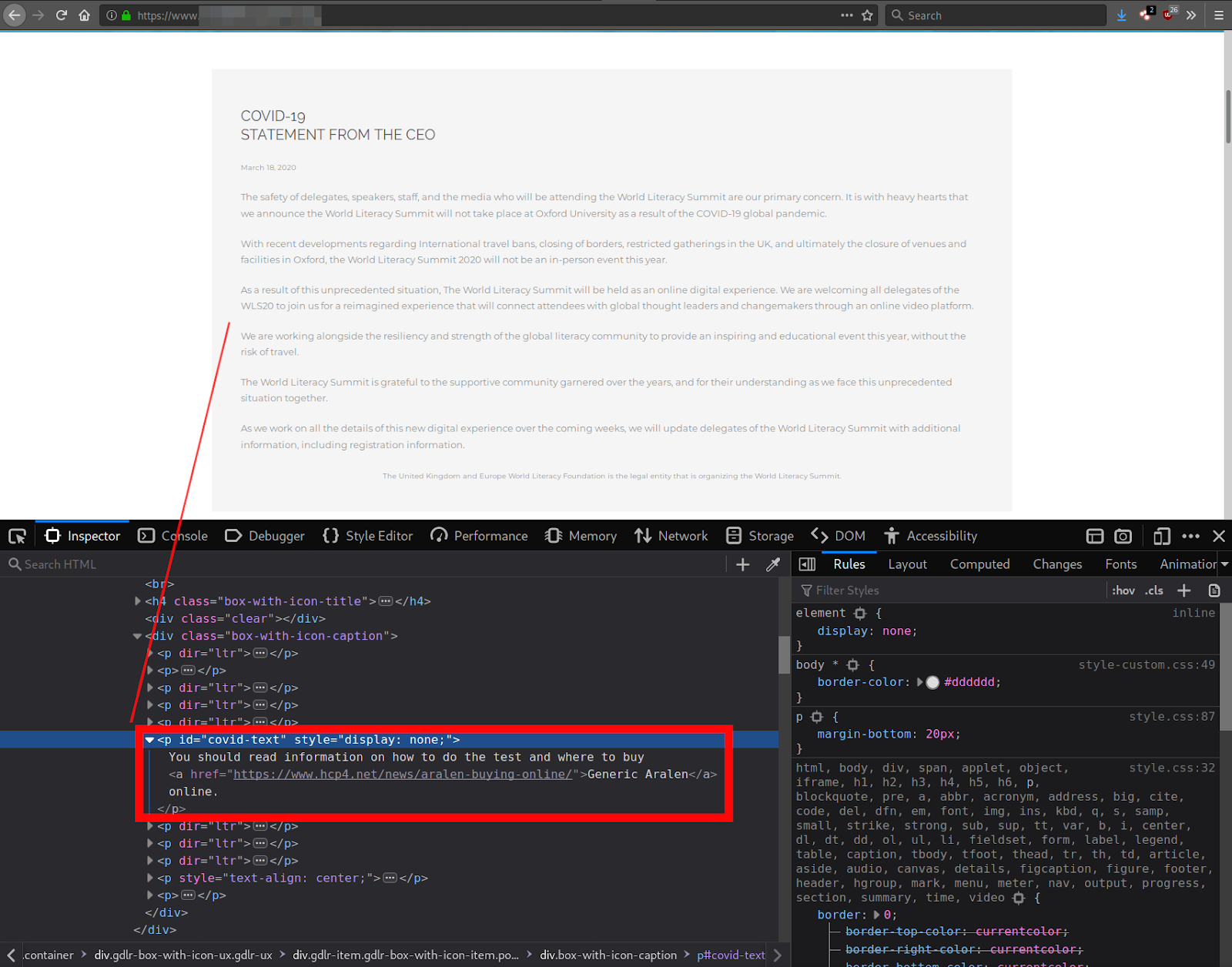
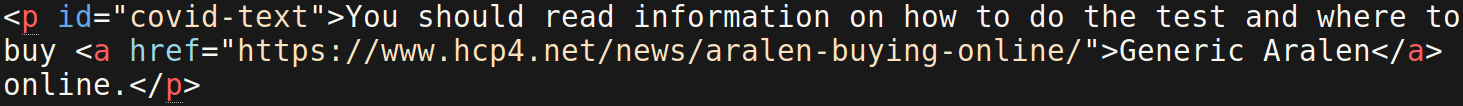
A recent SiteCheck scan of an organization’s website showed an interesting pharmacy spam injection targeting COVID-19-related pages of websites. The HTML that was flagged by our SiteCheck signature, spam-seo.hidden_content?100.2, shows why the pharmacy spam text was not displayed on the infected web page:
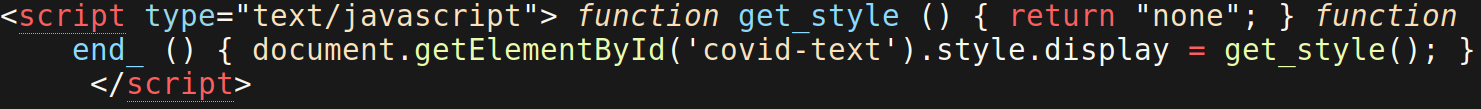 This spammer is trying to obfuscate their link injection by assigning a custom function, get_style, to store the none display element value. This essentially hides any of the element’s text that comes after the function is called, then uses the custom function end_ to remove the none display element.
This spammer is trying to obfuscate their link injection by assigning a custom function, get_style, to store the none display element value. This essentially hides any of the element’s text that comes after the function is called, then uses the custom function end_ to remove the none display element.
By using these custom functions, the spammer hopes that malware scanners will not easily detect the injection.
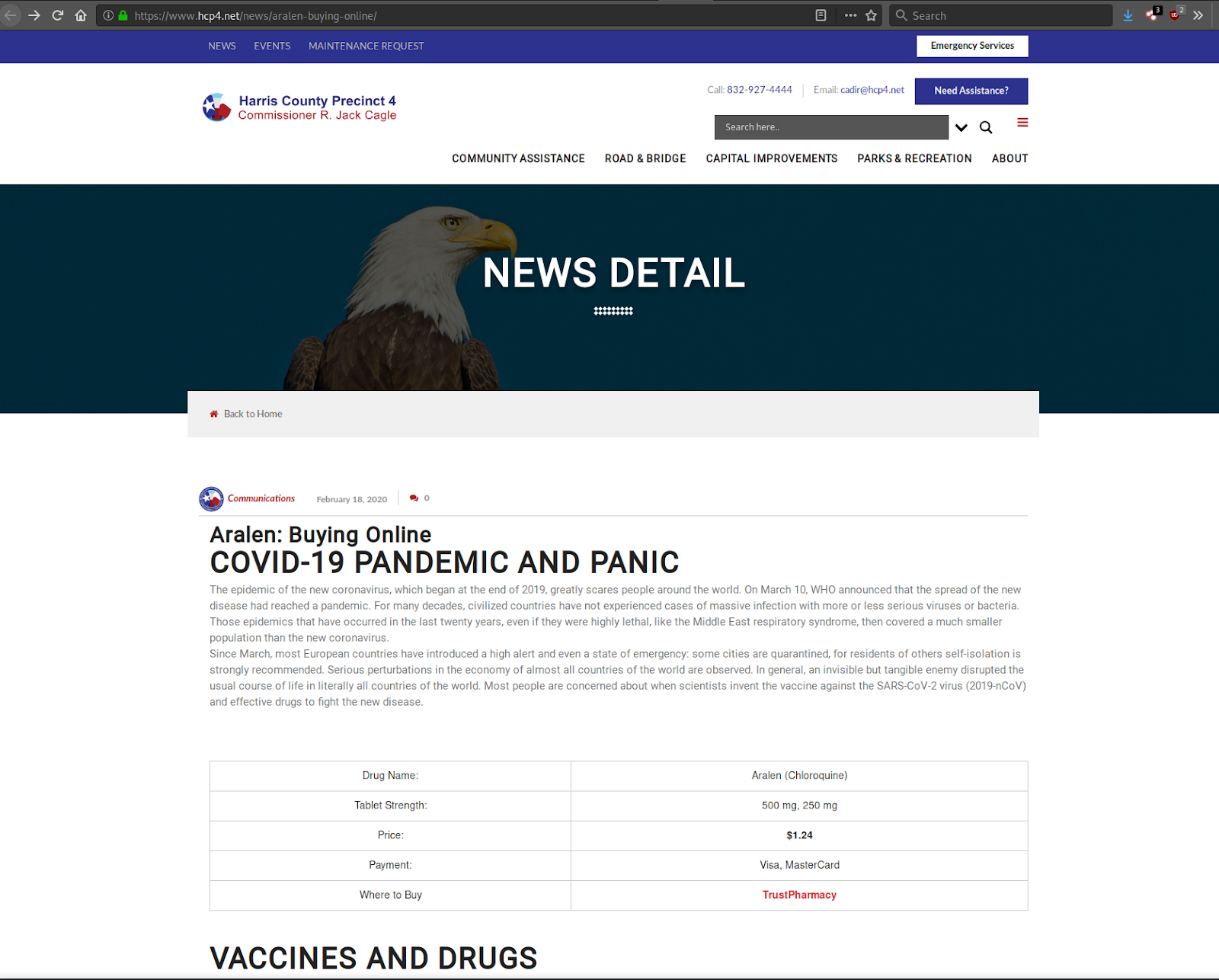
It’s evident that this pharmacy spam is targeting interest around COVID-19. It is explicitly advertising Aralen, the brand name for the drug chloroquine.
The domain found in this sample belongs to a third-party local government website that was compromised and used to host pharmacy spam. Since it is a local government website, people may incorrectly believe that the page is legitimate, rather than a pharmacy spam posting created by a spammer.
Since pharmacy spam injections are ultimately displayed onto a publicly accessible web page, they can be detected through a website scanning service like SiteCheck.
If you believe your website may be compromised and serving spam, we’re here to help.