We recently worked on an interesting case where Casino spam was visible in the page source, but couldn’t be located in any of the usual database rows or site files. Sitecheck flagged this as well.
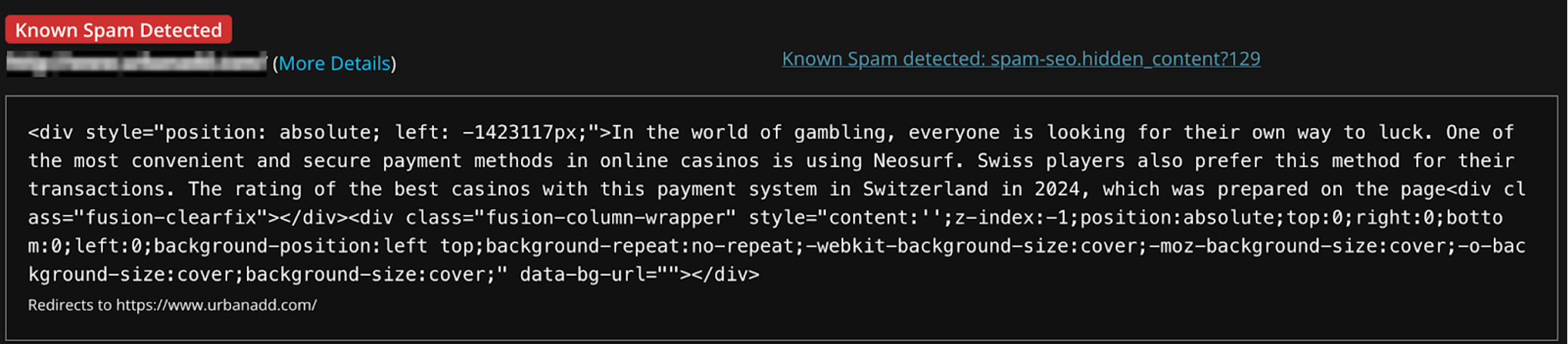
Casino and gambling spam is one of the most common types of spam attackers use. They are hoping that victims will submit personal information and credit card data on those pages. When search engines crawl infected sites, the spam pages will be indexed leading to malicious gambling pages appearing in search results that visitors may be tempted to click.
Hunting the Malware Down
My first step was to search the database and files for a key identifier, in this case -142311px. Since that didn’t turn up anything, and by taking a look in wp-admin I already knew that the site was using Fusion Builder, a popular page builder for WordPress, I turned to inspecting the database contents directly. As is often the case with page builder plugins, I assumed the content might be base64 encoded. However, upon examining the database row of the infected page I couldn’t find anything containing the spam content.
When editing pages in wp-admin built with page builder plugins, you’ll usually need to use the edit links specific to the plugin in order to gain access to any widgets and other components that the plugin uses. After inspecting the page with the Fusion Builder utility, I still couldn’t find the spam content so I decided to fall back to the default WordPress editor.
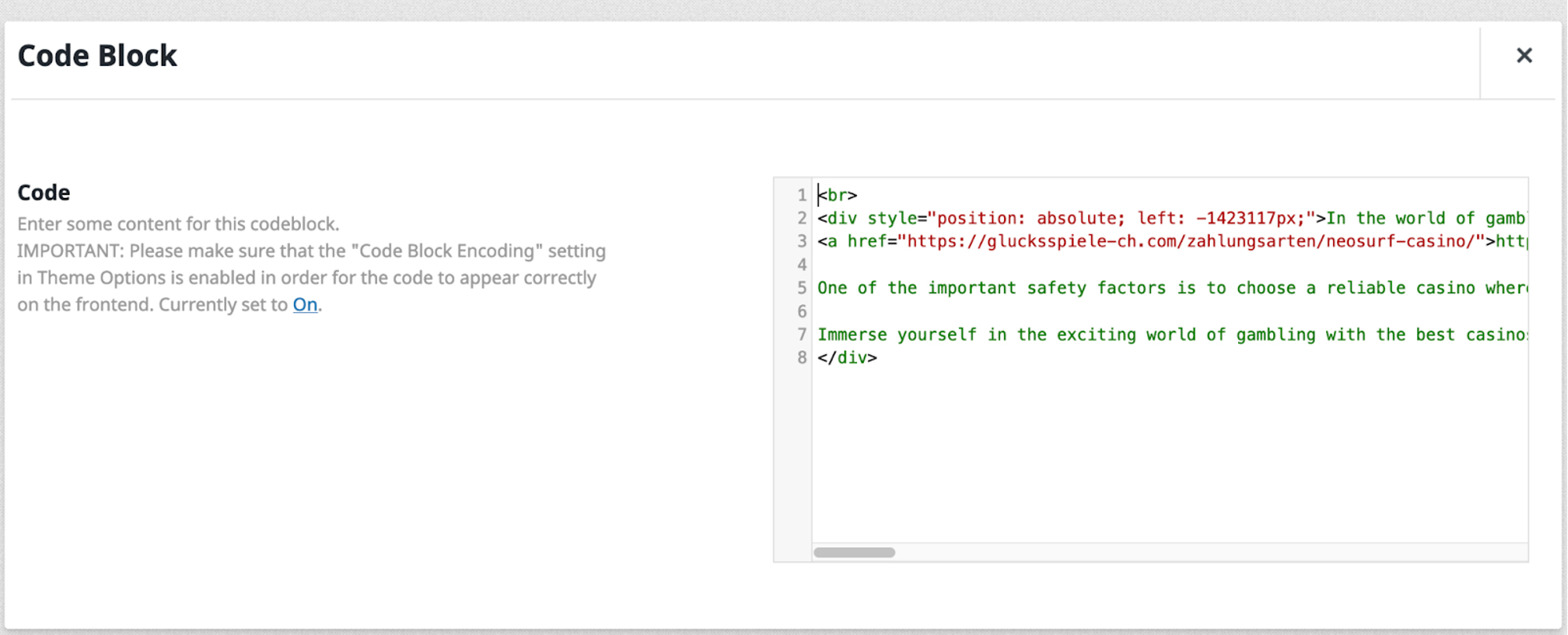
In most cases, doing this will only provide access to settings like the permalink name and some generic utilities for defining how the page is categorized. Interestingly, I found that the Fusion Builder plugin allows for some additional widget customizations and code blocks not directly accessible in the page builder.
Note: It is best practice to create a backup before making any changes in these areas.
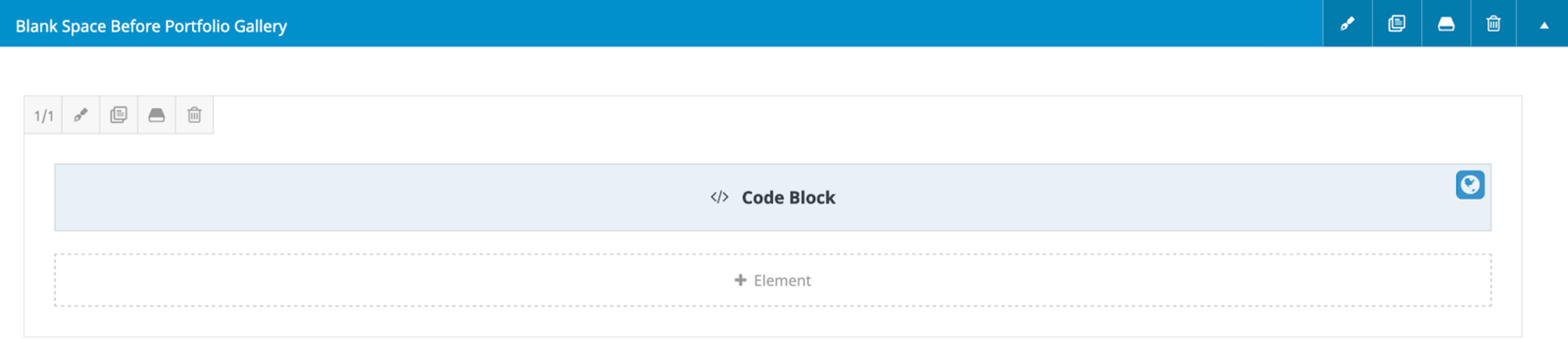
Upon editing the code block, I was able to see the spam in plain text.
Take Away
Attackers are always looking for ways to circumvent malware scans and better hide their injections. As we can see here, they took advantage of a simple trick that would be easy to overlook.
In addition to stealing personal and financial details, spam injections are one of the most common methods attackers use to redirect traffic to their own sites for further malicious activity and to further boost their own ratings by leveraging easy traffic hits, and that spam can destroy a site’s SEO ratings.
Prevention
As a website owner, it’s important to take a proactive approach to security to mitigate risk from threats:
- Regularly audit the plugins and themes in use and remove any that are no longer needed. Keep all plugins and themes up to date.
- Generate strong and unique passwords for all of your accounts, including website administrators, FTP, database, and hosting.
- Monitor your website and check for suspicious activity or unexpected website admin users.
- Consider using 2FA and restricting access to your WordPress admin and sensitive pages to allow access to only trusted IP addresses.
- Use a web application firewall to help prevent vulnerability exploits, malicious code, and hack attempts.
If you think your website has been infected with malware but you’re not sure what to do next, we can help! Reach out to us on chat. Our experienced security analysts are available 24/7 to assist you clean up website malware, and restore your website.