Update: We identified the root cause: MailPoet Vulnerability Exploited in the Wild – Breaking Thousands of WordPress Sites.
The last few days has brought about a massive influx of broken WordPress websites. What makes it so unique is that the malicious payload is being blindly injected which is causing websites to break. While we’re still researching, we do want to share share some observations:
- This infection is aimed at websites built on the popular WordPress CMS.
- It is targeting sites with outdated (vulnerable) plugins or weak admin passwords.
- Malware is highly obfuscated and attempts to inject SPAM to the hacked website.
There is, however, one very unpleasant impact of this infection. The infector PHP code is buggy and corrupting legitimate website files. It is targeting not only the core WordPress files, but also theme and plugins files. The results are various PHP errors being displayed instead of the normal site content. If you see this error on your site…
Parse error: syntax error, unexpected ‘)’ in /home/user/public_html/site/wp-config.php on line 91
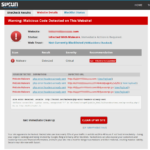
… it means your site is likely hacked. Our sitecheck scanner will warn of this error as well:
The only known solution (after removal of injected malware)is restoring these corrupted files from a clean backup. If you are curious about the malware injection, this is what it looks like (it is randomly generated):
<?php $pblquldqei = ‘5c%x7824-%x5c%x7824*!|!%x5c%x7824-%x5c%x7824%x5c%x785c%x5c%x7825j^%xq%x5c%x7825%x5c%x7827Y%x5c%x78256<.msv%x5c%x7860ftsbqA7>q7825)3of:opjudovg<~%x5c%x7824<!%x5c%x7825o:!>!%x5c%x782421787825!|!*!***b%x5c%x7825)…
We’ll continue the investigation and will provide more details as they become available. If you suspect you have been impacted by this infection rest assured that our team is ready and actively cleaning this mess up on all websites.









83 comments
I have had five sites that have been compromised over the past few days that sound markedly similar to this. When cleaning I found that once I removed the code that it was giving parsing errors. I found that randomly (or so it seems) the last 20 characters of a php file is being duplicated at the end of the file, sometimes adding endif or closes that aren’t supposed to be there which caused parse errors. In the five sites that were compromised each php file had injected code and only a handful (maybe 10) of files had the additional code at the end of the file.
Yes, exactly. That’s the same thing we’re seeing. It’s really nasty and annoying.
There also seems to be a backdoor somewhere. I cleaned up the original site three days ago and all seemed to be well, but it was reinfected less than 72 hours later. I may have missed a file, but I’m not sure, I’ve cleaned it and locked it down again and now I wait. Nothing in the database that I found so far.
Check your users, I found a blank one in there.
Thanks Trev, I thought of that too. I didn’t see anything in mine, searched for the common eval and decode strings in the DB too. After this last fight with it we’re about 20 hours in and going strong so far, I changed every password that existed and I even changed the WP passwords through PHPmyAdmin. This has made me pretty paranoid even though I have good backups. I’m hoping we’re in the clear now and the last reinfection was an oversight on my part during the original cleanup.
Yes. Most of them have a rogue admin user with blank name and user ID 1001001 (in case you are checking the DB)
be sure to check the file wp-admin/admin-post.php
or search through your .php files for the term $cookey you will probably find some more junk to remove. I too had removed what I thought was all the offending code/changed pw and was still re-infected.
also obviously make sure you remove mailpoet.
Yup, I completely deleted and replaced all core files. I only manually cleaned the theme and/or custom plugins that were being worked on (development sites). I never even looked inside those files past the general look to see if they were all affected. I think it’s all taken care of now.
Hi, yes, this is very likely same infection. Unfortunately, not all files have this duplicated part of code appended (it’s always constant count of chars within one infection) but we’re seeing also duplicated code in the middle of files, etc. Unfortunately, this seems to be very buggy infection. That’s why restore is recommended right now. We’re performing further investigation..
I totally understand that 🙂 I have a very limited set to base my assumptions from (5 sites is a drop in the bucket) – so far I haven’t ran into any in the middle of code, but I have been restoring all the files that I have been able to (core files, plugin files) the only files I’ve had to try to clean manually have been some customized theme files.
We have Wordfence installed along with renaming the wp-login.php, ive seen massive increases in blocked access attempts and excessive requests, we use wordfence to block more than 5 404 hits in less than 30 seconds, this prevents the majority of vulnerable plugin scanning and wp-admin login attempts because of the way its setup. Between Saturday and today there has been a huge amount of attempts as wordpress is also setup to send emails on blocks, user logins and file edits.
We’ve noticed this too, started a couple weeks ago. Such an uptick that I had to decrease the number of notification emails I get.
Funny thing is 10 mins after commenting on this post our server started mass mailing, someone obviously saw my comment and thought they’d have a proper go at it. Guess thats my night now taken up. Wont be tempting fate and commenting on this blog again.
Sadly I concur on this. Had me hopping all weekend as “help!” calls streamed in regarding website’s with broken home pages and the like. Quite a bear to recover as well. The hacker coding is randomized and sloppy coding injections are being made to the header of most files.
Again, driving home the importance of maintaining a good daily and weekly backup folks…
Backups without security is like fish without water. You need to ensure your system is fully clean by quarantining every file that enters and checking all files regularly. No matter how many times you backup, if you are infected, you are just backing up infected files. If you do not find out about the attack for a month or so, you could have no backups left that are not infected.
Sitecheck doesn’t always pick it up. The best thing to do is to go in and open up your wp-config file and check it out. If it’s got that random code at the top $ad;flkajsf=asdjfhaskdjfasd;lfkj then it’s infected.
This one affects multiple files, not only wp-config.php. Just finished cleaning a site where the list of cleaned files contained over 2,000 items (of course this depends on the number of plugins and themes you use)
Yeah, I just picked an easy file for people to find. I can’t imagine what it must be like at Sucuri right now. I’ve got two different clients in two different environments dealing with this. Any idea what plugin/theme/files are more vulnerable?
We don’t have full information yet (a few plugins suspected) but generally you can think that having not updated version of plugins (or old unsupported themes/plugins) is a bad idea. Some times a new version of plugin mean that authors fixed some security hole (and they don’t always disclose it).
Popular commercial themes and plugins are also at risk especially when they are not up-to-date. And, of course, blogs that have open user registrations may be an easier target (quite a few plugins has/had role escalation vulnerabilities)
Is it possible to write on a wp-config.php file with permissions 444?
Sure, if the infection script works with the same user permissions. Needs just chmod it before modification. (and then chmod back and touch with the original timestamp 😉
We see it all the time.
Massive attack on Friday, but most infected sites are now back to normal. A highly time consuming and frustrating operation. Lucky that our webmasters weren’t on vacation!!
You are fantastic, nothing serious about this on WordPress.org
Does anyone have a log of what the attack sequence actually IS. I saw what the injected garbage looks like, but the infection route is more important to me.
Reason: ZB Block would like to counter this threat.
If this is a LFI from an uploaded file, the $tring “< ? php" is already not allowed in uploaded files (must zip first). Also eval() and several other statements are banned when sent in executable form.
If it's an SQL injection attack, then my best guess is infection via AJAX (which does not properly sanitize HTTP_POST). AJAX has been a constant thorn in my side due to the loose and fast way it is written without regard to security, and ZB Block, to avoid complaints, had to cut AJAX users loose from several (severe) detection signatures. Note however, they must choose to opt out of the protections.
Of course, it could be something I've overlooked (will be adding injections through cookie abuse detection soon).
So if someone could bop over to the forum at www (dot) spambotsecurity (dot) com and share any info on the infection route, it would be appreciated.
At this point I can say that some plugin vulnerability may be involved. It helps create a rogue admin user. You can scan your logs for “94.136.150.28” IP and see some part of the attack.
We are still investigating the infection vector.
Let us know if you find more details
Did find one thing… if you remove the spaces from “< ? php" Disqus will truncate the post at the first quote mark. Is it the vector itself? Is it actually trying to execute the code?
Searching that ip brings up many hits on google – 94.136.150.28
Seems a newsletter plugin may be the culprit.
Agreed all the log hits were for a particular plugin, however one of the affected sites that I’ve had did not have the plugin activated, the other did. Anecdotal at this point of course, I can’t wait to hear more about it, it has been the bane of my existence for the past couple of days.
Are those two site on the same server account? If yes, one vulnerable site is enough to compromise all sites that share the account.
No they were not. The server with the site that had the plugin deactivated actually had several other sites on it that had the plugin activated that luckily were not affected. Files were still being tried on both sites according to the logs for that ip anyway.
Just to make sure I understand: If one site gets hacked, and it has the same username/password as other sites on that server ALL files can be hacked because they use the login on all other sites?
All my sites are on the same server, but totally different accounts (but where hacked anyway).
First sign of infection: User with a space as a name and 1001001 as username and a file called License.php in the root of your WordPress.
None of my sites have the mailpoet plugin btw…
We are in the process of cleaning up about 15 sites that have been compromised. There is no commonality to the plugins or Theme used among these infected sites however all sites were not on v3.9.1 when originally infected. First sign of infection was on 6/30/2014. Thought it was a fluke… until now.
Common to all our infected sites:
1. All PHP files in the entire Web directory have the malicious code at the top of the page. This includes non-WordPress PHP files that may reside above a WP sub-directory.
2. A blank User had been added to the MySQL _Users table with ID 1001001.
3. When viewing the Plugins page in wp-admin of an infected site, all plugins load with errors and are disabled. On some sites the entire plugin directories are removed.
4. The PHP files “last modification date” is not changed, although the malicious code has been added to the top of each file.
We experienced one instance (site) so far where the data in some of the files (below the code at the top) was slightly garbled making the code unreadable. However, the files from that site were downloaded and cleaned and something may have went wrong with .zip compression or in the FTP transmission.. but unlikely. Regardless, restoring from backup may be the best solution, but make certain to restore the database also or remove the blank admin account.
Recently saw some of this behavior affecting a site I host. Were you able to determine source?
No… unfortunately, we have been restoring sites and have even rebuilt sites by installing a fresh version of WP4.0 rebuilding the site from scratch. The only piece that wasn’t rebuilt from the ground up was the database. However, we did check the posts table for malicious code, but there is a lot of post data, so I guess we’re going back to that to dig a bit deeper to see if there was some code added to a post somewhere causing the re-infection.
There still is no common plugin used across these infected sites. We do not use MailPoet on “any” of the sites that got hacked, so although that may appear to be a source of the infection, it is not “the” source. My feeling from the start of this (now 4 months in) is that there is a vulnerability somewhere in the WordPress core that perhaps we don’t know about yet…
The truly scary thing about this is that every .php file on the site gets infected. The malicious code that is being added to these files is fairly nondestructive. What I mean, is that since this seems to be such a wide-spread issue, this hack could do disastrous things if the code were used in a much more malicious way.
hi buddy i have 3 wordpress sites all using the same plugins that ware infected the same way…the databases are all intacked i just need to know how i can rebuild the site from scratch or find someone that can help me rebuild these 3 wordpress sites.
can you or anyone give me any pointers or advice on what to do?
Hi Jo, the first thing is to reinstall wordpress, the delele the current theme and reupload it (with clean php files). Then do the same with th plugin, delete them all and then reinstall them.
This doesn’t help. The source to the bug has buried itself somewhere far deeper, I suspect in the database itself.
Yes, the malware creates a user with a space as name.
Best bet:
Backup your entire site to a local installation.
Backup the database too.
Then remove _every_ file on your server. Including your uploads and other directories on your webserver. (100% clean). I’m not kidding. Every directory can contain malware that would bring it right back.
Change passwords to the servers controlpanel, FTP and database since they have been compromised.
Then reinstall a clean freshly downloaded WordPress + plugins + themes. Remove unwanted or old (not updated) plugins. Install security plugins like Wordfence and iThemes security. Activate them and harden your install. Use firewalls.
Do not use _any_ of the old files(!)
Restore the site+database on a local WP-installation (use USBwebserver or something easy).
– Delete unknown users from the database.
– delete unknown posts, comments, etc etc.
– make an export of that DB and scan it for code like ‘eval(‘,'<php', 'base64'
Scan the uploads file for the same codes.
Remove weird out-of-place files.
Make sure a PNG or JPG is really a correct PNG or JPG… and not a PHP file in disguise.
If possible you replace most uploads with fresh new files.
If you are sure the uploads and DB is clean you can restore it back to the cleaned server.
This should make your new installed WP clean and hack-proof.
BUT….. using bad plugins is just like locking your front door, but leaving the backdoor wide open. So cut out unnecessary ones…
What i wanted to say:
Scan the uploads file for the same codes.
Remove weird out-of-place files.
Make sure a PNG or JPG is really a correct PNG or JPG… and not a PHP file in disguise.
If possible you replace most uploads with fresh new files.
If you are sure the uploads and DB is clean you can restore it back to the cleaned server.
This should make your new installed WP clean and hack-proof.
BUT….. using bad plugins is just like locking your front door, but leaving the backdoor wide open. So cut out unnecessary ones…
Yep – had recently migrated a client site that was infected from another host. WP 4.x does seem to knock it out. Cheers!
I’ve had about 10 WP 4.0 installations be infected over and over. Each time (its such a bore now) I get the random php header, I unpack a zip of the whole server to overwrite all the files with the non-injected version. I’ve searched around for oddities and added files, but nothing. I did have mail poet, but long ago deleted all associated files – there could still be some rogue file somewhere but I wouldn’t know how to detect it. I deleted all the 1001001 user and meta-user rows from the databases. They don’t return with the php injections. My guess is that some malicious code resides on the databases (it makes sense if the user data was able to inject itself, there are plenty of places to hide on a database). I’m really eager for someone to nail the source of these attacks, they’re happening every few days now and like you say affect every php file. Sometimes the sites break, recently they haven’t been (which suggests that the sites might be forcing trojans on visitors until I’m able to restore them). Bleh, such a mess, I feel for the WP users who don’t have sufficient skills to deal with this (they probably don’t even know if their sites are still showing).
I am very reluctant to say that we may have found a fix. Truly too soon to tell though because it seems our sites all get hit at one time over the course of a few days when the attack occurs. Sometimes the attack interval is a week, two weeks, a month… We are watching closely and monitoring the logs daily to see if they hold with this latest security fix. All I can say at this point without revealing too much for prying eyes is that we use iTheme security and have most all options turned on, activated and set at their highest security level settings.
Will reveal more in time. For now continuing to hold fingers crossed.
Just wondering how your potential fix/solution found via iTheme security(?) was working out? Any news for us? I haven’t had an attack for a week so I’m (perhaps naively) hopeful.
Well, we manage 24 WordPress sites and all of them have remained clean seemingly due to the last security adjustments made in iTheme Security. In addition to banning and blocking users that try to hack in to the site, we specifically enabled additional options (all but one on most sites) in the sections “System Tweaks” and “WordPress Tweaks” that we hadn’t enabled before. Enabling these options seems to have snuffed out this problem (hopefully for good). Please be forewarned that some of these options may conflict with other plugins or themes, so test your site after enabling each setting. We completely disabled XML-RPC and have verified that each site is using a safe version of jQuery. I hope that our findings can help others who have been struggling with this problem.
Just had a fresh attack, after 9 days of everything being ok. BLEH.
We detect this infection so many times too.
And, useful signature to find some hacked files is
‘explode.?(chr.?(.?([0-9]{3}.?-.?[0-9]{3}.?).?)’
Finally,
common point of a series of attacks looks like that, ‘wp-content/uploads/wordpress/index.php’ and ‘wp-content/uploads/tmp/index*.php’ is installed.
Yes. On many sites we can trace the beginning of the attack back to the very end of June or beginning of July. However, it looks like the early versions of it were less buggy and didn’t corrupt many PHP files.
In our service, these attacks recently was observed in 7/17 JST time.
As you know, They used some recently Vulnerability like a MailPoet.
Log such as the following have been found on all hosts that were hacked.
94.136.150.28 – – [04/Jul/2014:XX:XX:XX +0900] “GET /wp-content/plugins/wysija-newsletters/js/thickbox/macFFBgHack.png HTTP/1.1” 404 271 “-” “Mozilla/3.0 (windows)” “-”
or
94.136.150.28 – – [19/Jul/2014:XX:XX:XX +0900] “GET /wp-content/plugins/wysija-newsletters/css/admin.css HTTP/1.1” 404 257 “-” “Mozilla/3.0 (windows)” “-”
But is interesting to note that the attack has been established even though returns a 404 as described above.
And in additional research to these hosts, login after the formation of the ‘wp-login.php’, use a plug-in upload function to upload a file called ‘license.php’, you have to attack a starting point it There was evidence like.
macFFBgHack.png – is just a request to test if MailPoet is installed. Most likely they didn’t use that vulnerability on that particular site. However, if the MailPoet was found on a neighbor site, that could lead to cross-infection.
Do you have a log record for the ‘license.php’ upload request?
Thanks!
I had 2 sites compromised with this very same attack, both of which had the MailPoet plugin installed.. Both had the header code injected, both had the blank user placed into the database. I assumed it was the MailPoet hack previous mentioned on this blog. Can anyone else confirm that they had the vulnerable MailPoet version installed on all of their hacked sites?
It was from the MailPoet plugin. Despite claims that the latest version was secure, it is not. My sites and a colleagues were shut down because of the plugin.
Can you confirm that the latest version is indeed still vulnerable?
We also saw that some of these infections exploited the MailPoet (wysija-nesletters) vulnerability. But not sure about the latest version. When did you upgrade it? The attack actually began in the very end of June/beginning of July, so it could use a window before the plugin was updated.
This infection was driving me nuts since Friday. I first noticed encrypted code in index.php and the rogue admin (which for some reason added +10 to the admin count). After restoring backups, the code swiftly injected itself into the files again, this time into almost all of the files in the WordPress root.
I solved the problem by changing all passwords and restricting access to my site to my IP address and removing what I suspect was the offending plugin.
Which plugin did you suspect?
It’s called Job Manager by Gary Pendergast. I did manage to find a great substute for a job board (http://wordpress.org/plugins/wp-job-manager/). It could have also been brute force, wince Wordfence was indicating that admin passwords were too weak.
A hosting company I work with also had many websites affected by this. To ease detection of compromised accounts I’ve made a php script for admins which quickly scans all databases and raise alert if suspicious user is found. It also checks if MailPoet has been installed, so client can be contacted by staff and told to update if necessary.
Here is it, hope it may help: http://artefact.io/massive-wordpress-hack-seems-underway/#detection
Just to let you know – my site was hacked and i do not have MailPoet. So it is possible that another user on my shared server has this? Or are there similar plugins?
All hacked sites had the “google-analytics-dashboard-for-wp” plugin, but also SEO plugins from Yoast and w3 total cache… Anyone else see similarities?
Someone on the shared server was hit, and your site was likely a secondary infection. 🙁
What i don’t get is that my provider says that 1 account is totally separated from other accounts. All my sites have an own account. So when I log in as USER1 there is NO way I can access files for USER2 on that same unix shared server. (Unless the php-script has 1337-Un1x-h4cking-skillz 😉 )
Conclusion: there are more plugins vulnerable. And I have one. But which one. 😉 What code should I look for? ‘is_admin’ pops up many times in lots of plugins…
Hi guys, we also had a massive attack on various clients. We have found there is a messed up file called license.php
Also you can clean the code from plugin files, this will allow you to reactivate them. Once reactivated, update all plugins to latest version to clear the rest of the code out and then go to your Updates under dashboard and update your wordpress to the latest. I know this isnt an ideal fix and cleaning files is a pain but its a sollution. Be sure to change your admin passwords and remove any unwanted users. The ID seems to be 101101 for the new user that is added to your site and has no name/email address.
I noticed this about 10 days ago all my file sizes are increased when i connect through ftp on one of my vps server. So i checked wp-config and saw the malicious code. There are two domains and one subdomain on this server. One is active news portal site with mailpoet installed but not active at the time. The other one is default installed wp site. Under the subdomain i have 6 other demo wp sites for a client.
First i re-upgrade the wordpress from admin panel of the news portal. The core wp files cleaned but not the plugins and theme files. When i open plugins page from admin all the plugins disabled. Then i install Antimalware (Get of Malicious Scripts) plugin and scan the whole site. It found the affected files. When im waiting for the scan i check the other 6 site on subfolders. But they are completely blank frontend and backend. Lucklily i found a plesk backup of the system from 4-5 days ago. Download it and upload all sites files one by one, login and scan and clean malicious code from them too.
When i check the old backup zip, i noticed only the news portal sites wp-admin/admin.php file was infected. May be its a start point or i just backed it up in the middle of infection being spread.
Until i saw this post i didnt know and check the new admin user. I deleted all of them.
Dont forget to make a clean backup after you sure its all cleaned. I saw the importance of backups one more time.
Ps: Sorry for my english if i made mistakes.
I noticed today that one of my client’s sites had been hacked.
They did not have MailPoet, but had the blank user, infected PHP files, etc.
Interestingly, when I restored from backup, the PHP files were fine, but the blank user and license.php still existed (suggesting they took place a lot earlier)
I’ve been getting these too, but sadly I wonder if I am the cause as when I first log into the site, everything is fine. Within minutes the blank user account appears, all the plugins stop working (and disappear from Plugins menu) and almost every PHP has a code injection.
Well i think we all here the same problem … in my case all the php files contain a malicious code in the header which begin ” <?php $osetwzdswr = '-#T#-#E#-#G#-#H#-#I#-#K#-#L#-#M#-#[#-#Y#-#D#-#W#-#C#-#O#-#N# … " and the rest is composed from complex numbers and functions , it's an very long one . it infect all file with " *.php " in the content , admin and include . can any one give me some ideas ( i tried to cleaned the site manually but its too big ) help please .
Thing is all 30 of my sites have been hacked and your scanner doesnt seem to pick this up
Hi @RAFNewsLuke:disqus are you a client or using our free scanner? Can you send us specifics to labs@sucuri.net? That’d be awesome. Thanks
Its the free scanner does that mean it wouldnt pick up code
No, it just depends on the payload and type of infection. If it’s a server level payload with not external impact than no, it won’t. But if it’s triggering a browser action, then it should. See this: https://blog.sucuri.net/2012/10/ask-sucuri-how-does-sitecheck-work.html
If you send us the info to labs@sucuri.net we should be able to investigate.
You may want to note on the scanner that it will only find infections that are being presented. It will not find infections within the website that are not being presented and that includes backdoors too.
Hope you dont think I am complaining as no off site scanner could do that, but it is worth mentioning that on site scans should be completed as well as using a strong software firewall.
All done and sent with example file
Anyone knows when exactly started?
This really was done sloppily, but it may be a blessing in disguise.
Of the sites I have seen with this infection, they were already infected prior to this code being injected and backdoor shell files have likely been left in place by previous attackers. I doubt you will find many logs showing the attack vector.
I decrypted as much code as I could and found that the code injected into the top of every file looks for visitors with the user agent for Internet Explorer 11 which has a vulnerability that allows malware to be silently downloaded by force and the code executed on the visitors computer.
Do not assume that this was the only attack and do not assume that scanning your site with Sucuri site scanner will find it, although it is an awesome tool, it can only find infections being pushed to visitors, it will not find infections deep within your system or backdoor shell scripts.
You really need to run a full scan on your hosting account. Insist that clam AV is installed, updated and run scans yourself to see the infections.
Never assume it to be a single infection or action, always look for more. You may end up backing up infections and backdoors.
We too are being slammed by brute force attacks and various other bots trying to sniff our files.
Here is the problem I have used wordfence but it seems php files are still being injected into folders etc. Even my sub domains that are standard html website are being injected somehow. The php files are encrypted and weird named so finding them is not hard but they will get you blacklisted if not caught in time. I have no dam clue what to do, second time this month I have had to clean all my websites up html and wordpress sites.
Hey all, this has been the most useful thread on this issue I have found. Still having about 1 of my users’ wordpress sites a week being infected. Maybe they are old and just being discovered, not sure.
Most of the comments are 3 months or so old. Has there been any update on this? Where it is coming from? Any good ideas how to clean up? Any solutions on prevention?
Hi Steve, Have you got as far as removing the 1001001 user/meta entries from your database? It doesn’t stop the attacks but is a good start. I create a ZIP backup of my uninfected files, and then extract them via CPanel whenever the attack happens. Recently I’ve noticed that with the attack, I can still log in and manipulate sites. Which is a pain, as it means I have to actively look for the attack now rather than having my alertness drawn to it.
Yes have deleted all the users I found. My hosting service is looking for a way for me to search all customer databases for use 1001001.
But surely by now someone, even WordPress, has worked out how this happens. Iff someone can inject into every php file, next time the code could be catastrophic. Imagine something like exec yes | mdir -R wp-content/* (deliberately dodgy)
Unfortunately this happened to me around November and I had to Shutdown both my sites. Now I am having a beast of a time geting my apps from WordPress that i paid for.
Both are important. a) Having regular backups. b) Keep an eye on your website files. How to do that? use some kind of automated solution. I know about backup. I use EverLive to take automatic backups at defined intervals. It’s free. Not sure about the best method to detect if my website script is compromised. Specially when I am looking for a free one. Yeah, income from Adsense is very little.
wich sites have been infected
Hi Peter. My site definitely has been injected by this malware. One question though. If I upload the clean back-up they would still be able to get back in right? It won’t solve the problem I suppose?
Do you need a quick long or short term first class financial offer of different categories such as business, personal, home, auto, student, debt consolidation finance e.t.c. no matter your credit score. We are guaranteed in giving out financial services to our numerous clients all over world. With our flexible lending packages, funds can be processed and transferred to the borrower within the shortest time possible, contact our specialist for advice and finance planning. contact us today at faircentloancompany@gmail.com
Comments are closed.