Phishing kits are the back end components to a phishing attack and are often designed to make it easier to deploy a phishing page.
These kits are typically bundled in compressed files, such as .zip archives, and contain the entire file infrastructure needed to operate a phishing page. Once a kit is uploaded to a compromised website or hosting environment, the attacker can simply unzip it and launch operational phishing pages within a short period of time.
In some cases, attackers create phishing kits to sell to other attackers. To increase the value of these phishing kits, they incorporate features that make the phishing page(s) easier to manage and employ countermeasures to prevent detection from automated bots like Phishtank or other unintended visitors.
Phishing for Chase Victims
During a recent investigation, a phishing kit was found on a compromised website. Inconspicuously named account-verification.zip, the archive had already been unzipped by the attacker to deploy phishing pages targeting Chase bank customers.
As is the case with a large majority of phishing campaigns, victims were directed to these pages through a phishing email which contained social engineering text and a link to the phishing page URL.
Phishing Behavior
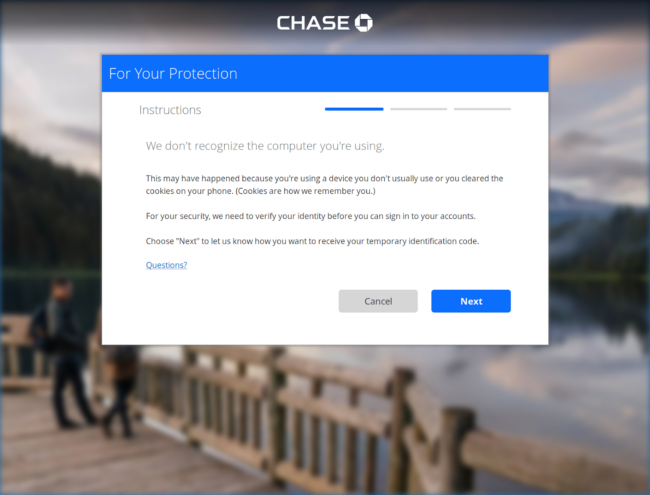
The phishing kit generates four pages used to steal data from victims. The initial part of the workflow starts with a landing page that appears to be the Chase internet banking login page.
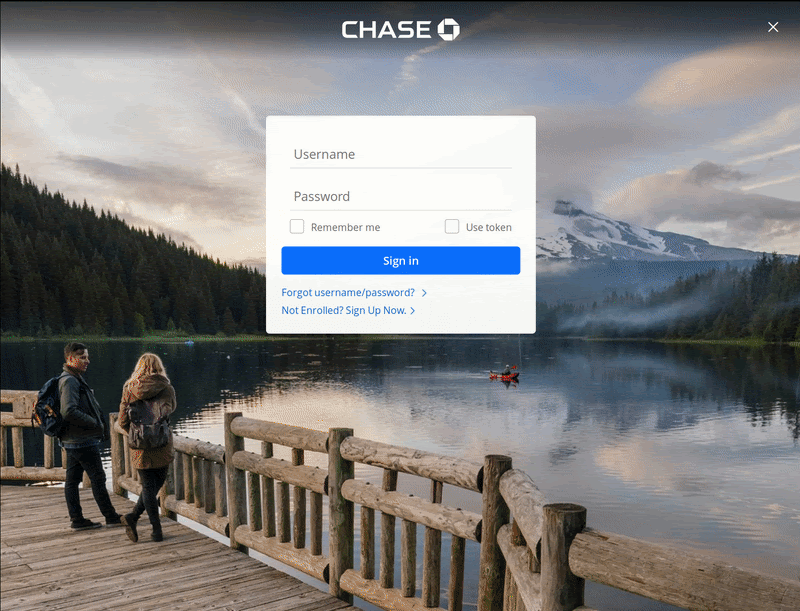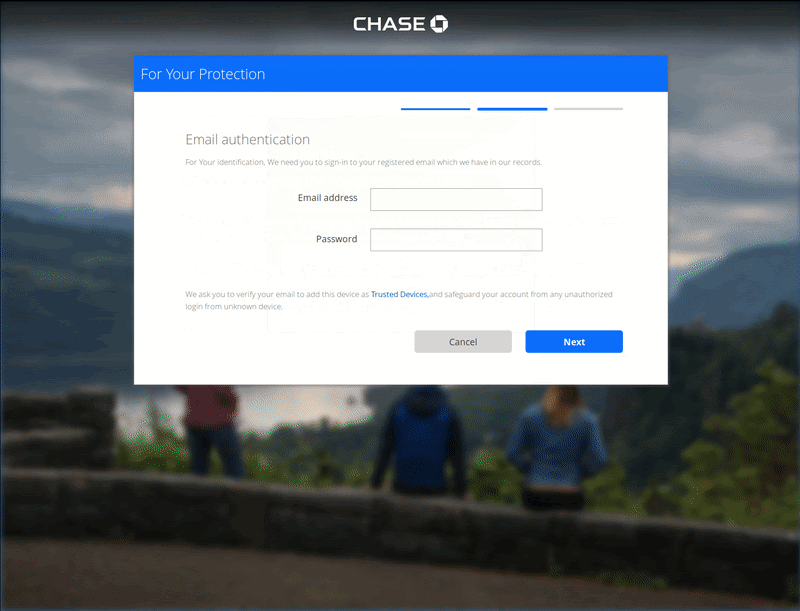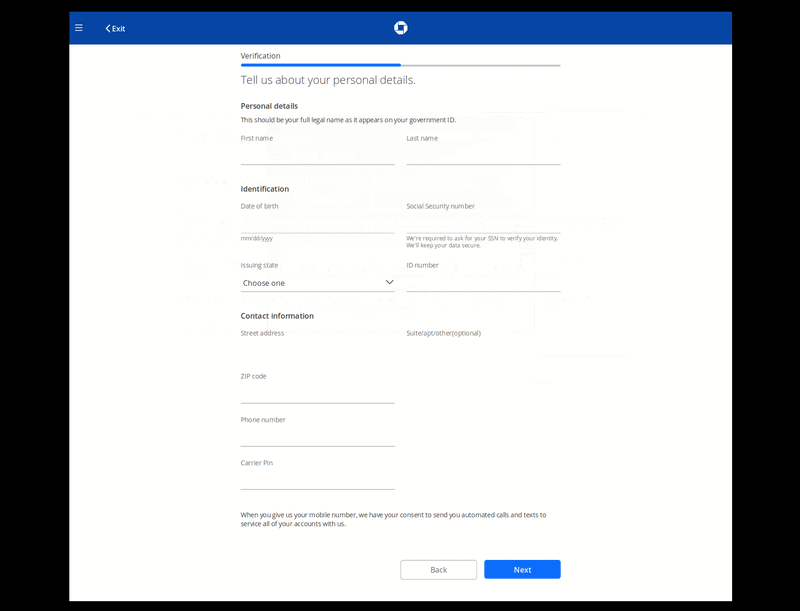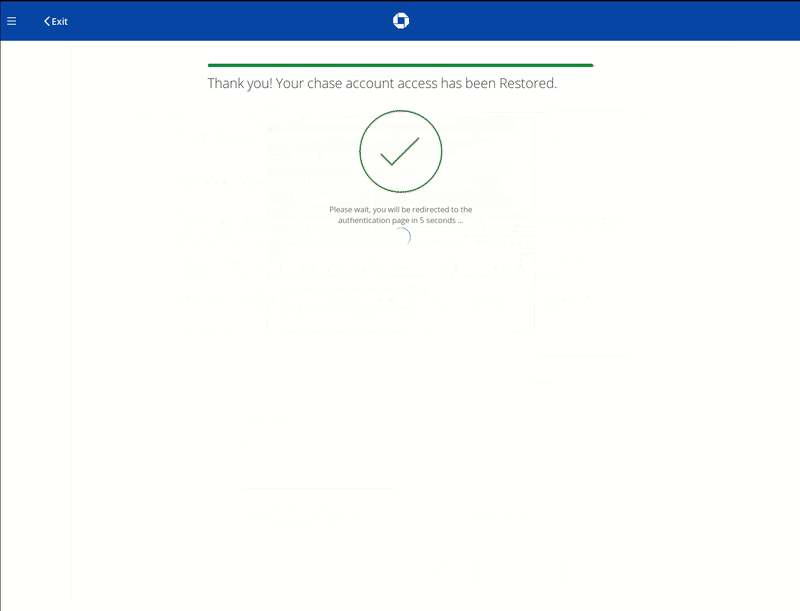
Immediately after a victim attempts to sign in on this initial Chase login page, they are redirected to a page warning that the user’s device has not been recognized and additional authentication will be necessary:
Clicking Next and navigating further through the workflow leads the victim to a series of phishing pages asking for the victim’s email account login information, personal data, and payment card details.
As soon as the victim completes this fake account verification sequence, an email is sent to the attacker with the stolen data from each phishing page — a total of four emails.
Administrative Backend
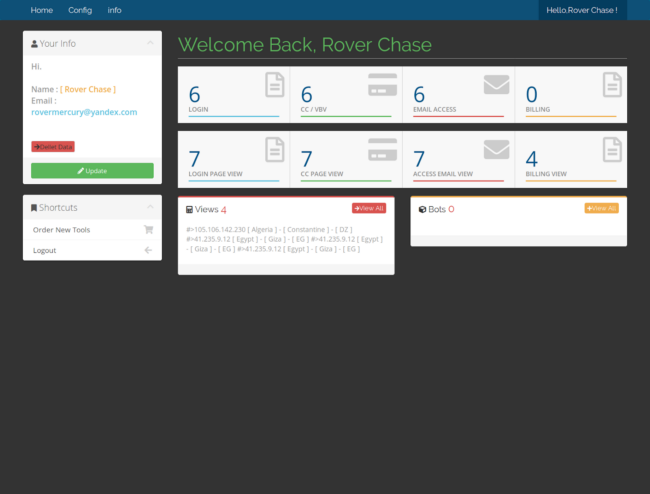
Included in this phishing kit is an admin panel backend that allows the attacker to change some of the phishing page settings, including the email address used to collect the stolen data and the various anti-bot countermeasures.
These settings are coded as variables within the phishing kit’s configuration file /admin/YOUR-CONFIG.php:
$show_start_page = "yes"; $show_email_access = "yes"; $show_contact_information = "yes"; $show_credit_card = "yes"; $show_success_page = "yes"; $anti_bot = "yes";
This backend also acts as a GUI repository for the stolen data which is stored in .txt files on the server hosting the phishing pages.
These .txt files exist as a sort of backup. In the event that anything should happen on the server that might prevent the stolen data from reaching the attacker’s configured email address, the phisher will still be able to access the stolen data from the web server.
Evasion Techniques & Bot Countermeasures
For every phishing page, multiple bot countermeasure files are loaded via the PHP include function at the beginning of the PHP code:
include'Spox/Anti/IP-BlackList.php'; include'Spox/Anti/Bot-Crawler.php'; include'Spox/Anti/Bot-Spox.php'; include'Spox/Anti/blacklist.php'; include'Spox/Anti/new.php'; include'Spox/Functions/Fuck-you.php'; include'Spox/Anti/Dila_DZ.php';
All of these files are used to filter out requests to the phishing pages. These requests are filtered based on multiple factors such as IP address ranges, IP address hostnames, user-agents, and other browser fingerprinting.
If one of these filters is triggered, the phishing kit will deliver a 404 result to the requesting device. This essentially makes it appear to the bot as if no phishing page had been set up at all.
For example, if the hostname or rDNS of a requesting device contains a list of banned words, then it is served a 404 result — it is automatically assumed the request is not from an intended victim. The 404 result is served by the PHP script through the use of the header function.
$SPOX_HOSTNAME = gethostbyaddr($_SERVER['REMOTE_ADDR']); $blocked_words = array("drweb","Dr.Web","hostinger","scanurl","above","google","facebook","softlayer","amazonaws","cyveillance","phishtank","dreamhost","netpilot","calyxinstitute","tor-exit","msnbot","p3pwgdsn","netcraft","trendmicro","ebay","paypal","torservers","messagelabs","sucuri.net","crawler","googlebot","Googlebot-Video","bingbot"[...redacted...]); foreach($blocked_words as $word) { if (substr_count($SPOX_HOSTNAME, $word) > 0) { $content = "#> ".$_SERVER['HTTP_USER_AGENT']." [ Bad word ] \r\n"; $save=fopen("../../bots.txt","a+"); fwrite($save,$content); fclose($save); header("HTTP/1.0 404 Not Found");exit();
Some of the banned words include common crawlers that may otherwise detect the phishing page.
The PHP script also records details about the request (user-agent) and the reason for serving the 404 request block to the file bots.txt. This bot.txt text file also stores block requests that occur for other reasons, such as a request originating from any IP addresses defined and “blacklisted” within this phishing kit’s IP-BlackList.php file.
Phishing Kit Author
Unfortunately, phishing continues to be a profitable cybercrime for attackers. It’s not hard to find the stolen logins being offered for sale or otherwise made available for fraudulent use.
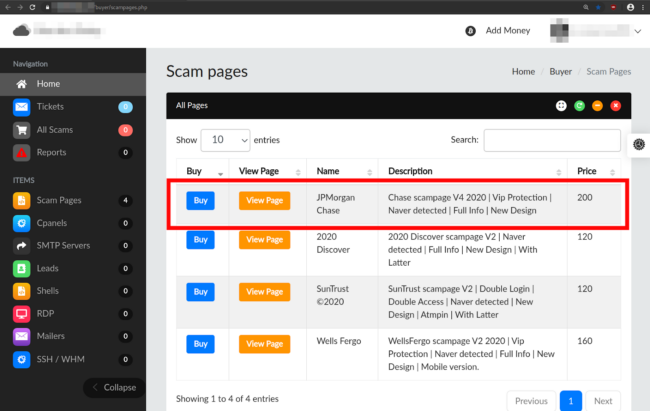
Below is an example of someone offering a sample of data that was stolen using this same Spox Chase phishing kit.
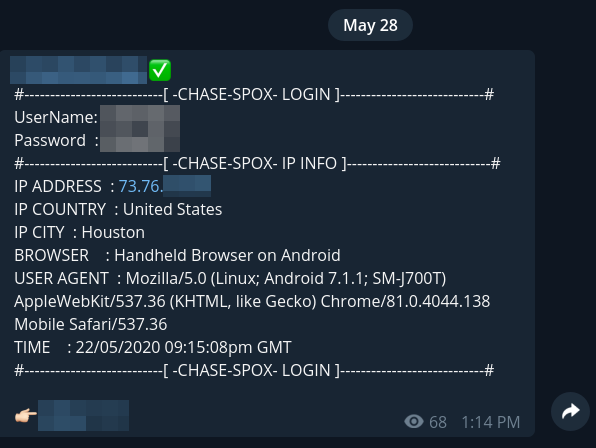
To attract more customers and to “support” existing ones, phishing kit authors are adding convenience features, like backend website panels, to help manage the phishing content and other settings. These types of features make it much easier for people with little experience to launch a phishing campaign, however the authors do charge a fee for these additional components.
The author of this Chase phishing kit, Spox, charges $200 USD for the latest version of the phishing kit.
By offering the kit without actually deploying the kit on compromised environments, the phishing kit author is able mitigate some of the risks associated with performing fraudulent transactions with phished data. Instead, they just sell the tool to others looking to perform risky fraudulent activities.
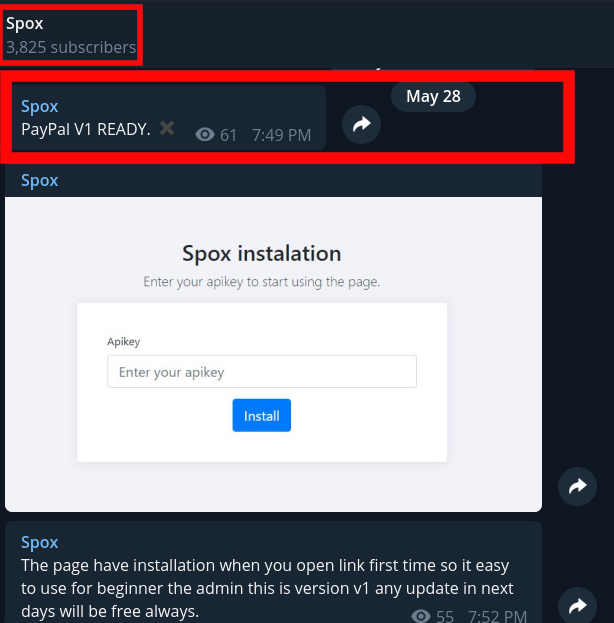
In fact, while writing this post I discovered that Spox had released a new PayPal version of the phishing kit, announcing it to over 3,000 subscribers.
 Mitigation Steps
Mitigation Steps
Detecting phishing kits can be difficult, especially if you rely solely on an external scanner. Phishing kit directories are usually set up within an existing subdirectory and won’t load on your website unless you have the exact URL.
One of the best methods to detect indicators of compromise is to employ a server-side scanner or file monitoring, which alert you if any files or modifications are made to your website. Another option is to use Google Search Console to receive notifications about phishing and other security problems.
If you think your website is hosting malicious content or phishing pages and you need assistance handling a compromise, we can help.