Visiting websites throughout the decades has always had its risks. With the creation of Flashplayer and JavaScript, site visitors could potentially be impacted by malicious viruses, like the notorious YouAreAnIdiot[.]org pop-ups that caused computers to be overrun by a massive amount of pop-ups until their computer rebooted. Unfortunately, infections can, and likely always, will exist when accessing infected sites.
In this article, we’ll discuss the kinds of hacked sites that are still out there and how to avoid them. As we go through these various attacks it’s important to consider proactive measures to avoid them as a site owner. With the number of vulnerabilities existing on the web, malware infections have always been a common nuisance. In my article Why are WordPress Websites Targeted by Hackers? I elaborate further on how these infections occur, and best practices to minimize their risks.
Phishing Campaigns
Phishing can occur in many forms whether it’s through email, SMS, or accessing a certain website. These campaigns can obtain tons of information on their victims. From names, addresses, social security numbers, phone numbers, credit card information, etc. The collection of information obtained can be detrimental to a person’s identity and privacy online.
With the steady incline of online services following the pandemic, it’s become even more crucial in ensuring you’re visiting the correct URLs for what you need. For example, this website appears as a login portal for Microsoft when it in fact is not:
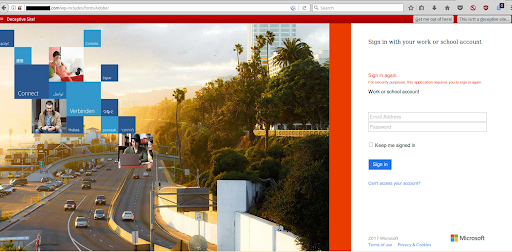
At first glance, this looks like the typical login portal for Microsoft, despite the “Deceptive Site” warning. Luckily, this one was detected by blocklist authorities. For smaller, newly made sites this may not always be the case though. We recommend always carefully inspecting a domain from any site links, emails, texts, etc. so you’re not being manipulated into providing sensitive credentials to a bad actor.
A helpful tool in determining if a site has been reported as suspicious and reported for malware is running it through a tool such as virustotal.com.
Tools such as VirusTotal as a part of your security arsenal will include binary properties, antivirus detection verdicts, static features, behavior patterns such as communication with specific hosts or IP addresses, submission metadata, and many other notions. They can be beneficial in a variety of ways.
Drive-by downloads
This type of infection persists on a website generally without a website owner’s knowledge. It can be injected through various methods if website security isn’t intact, as mentioned in our previous article What do hackers get by hacking any website?
Ransomware can also occur in these instances, where the site visitor’s OS is completely locked down and encrypted unless paying the hacker a hefty price in cryptocurrency. They can include keyloggers, spying on your activity, and fully hijacking your devices.
As you can see, it becomes quite apparent how detrimental this can be if these persist on your website. Drive-by downloads can be avoided on both the site owner’s end through efficient website security measures, as well as reliable anti-virus software installed client-side.
As a site owner, you or a personal administrator/developer should regularly be scanning, protecting, and hardening your website against any potential threats and vulnerabilities. As the average site visitor, however, you should ensure there’s at least some form of protection both browser-side and within your local OS. You should also check for any software/browser updates regularly.
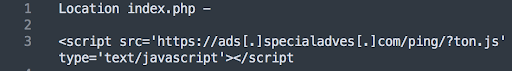
As an example, here’s a recent malicious script injected into a site our malware research team found:
In Conclusion
Mischievous infections such as these are not only severely damaging to the website visitor, but also any business that perpetually has them on the back-end. A website owner must be diligent in ensuring logins are secure, updates and malware scans are regularly completed, and checking network activity logs to confirm if any malicious activity is occurring.
If your browser or antivirus program issues any warnings to you when trying to visit a website, don’t ignore them! This is particularly true if you see an alarming red notification warning of harm to your computer.
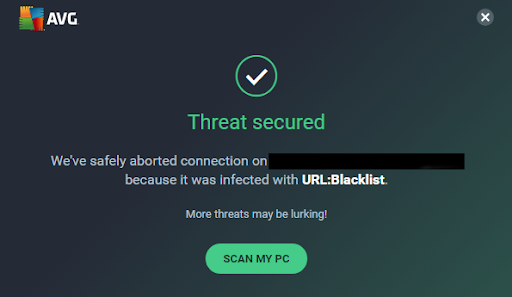
Having Firewall protection in place before malicious requests reach the server will help prevent anything that slips through the cracks. Essentially the Web Application Firewall will function as a middle man between the site visitor and hosting original server, detecting and filtering out any potentially malicious requests.
If you believe your website has already been infected, however, don’t wait to get it cleaned up. The longer you wait the more likely your site will be added to blacklists by blacklist authorities.











