We’ve all seen sketchy looking emails or texts with malicious links to click on. There are still people who fall for these more obvious types of scams, however, phishing scam messages are designed to be deceiving. They use methods that appear valid or of some urgent matter, encouraging its victim to hand over their data.
Phishing Campaigns
Phishing attempts happen in many ways, such as:
- deceptive email campaigns
- suspicious SMS alerts (called smishing)
- fake websites designed to look and sound authentic
Cybercriminals apply these social engineering techniques to trick people into providing sensitive information like credit card data and login credentials.
Analyzing an Unexpected Phishing Attempt
As a malware researcher, we do a lot of reporting about interesting malware we discover. Typically, malware reports are a three-step process:
- check the message origin,
- check how it was sent,
- check method used to control the site.
Recently, I checked my own spam mailbox (which occasionally lends itself to finding interesting malware). I followed the trail to a particular set of phishing links in a message that happened to be infected, originating from a WordPress website with a vulnerable plugin that would allow the attacker to have privileged access. This is a popular vulnerability from 2014, according to our industry report on hacked website trends.
Here is a screenshot of the phishing email:
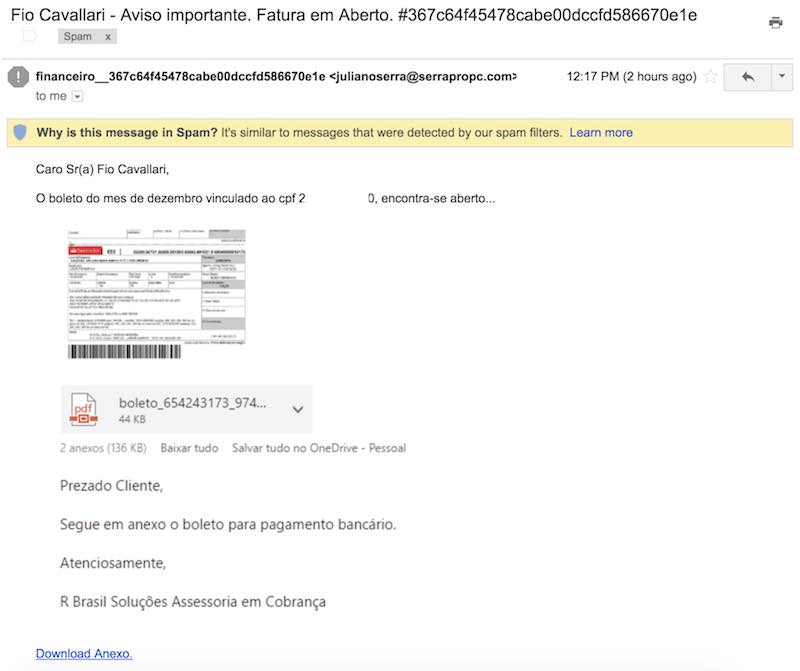
For those not familiar with Brazilian Portuguese, the content of this message is quite straightforward. It says that I have a payment overdue with an attachment – “boleto” – a common barcode payment method in Brazil.
The attackers reached me by my personal email alias (not my full name), however, they retrieved my CPF (Brazil’s Social Security Number) correctly! We can infer that they accessed my personal information due to the exploiting of leaked data, which unfortunately is not very uncommon in Brazil.
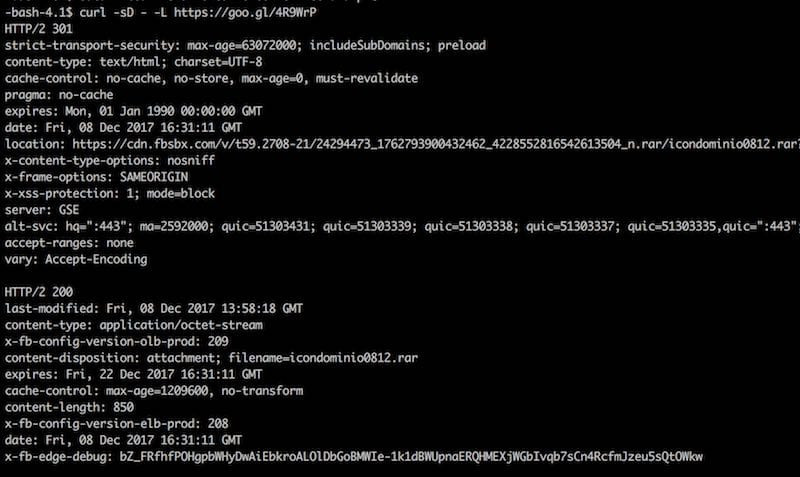
Everything on the message is clickable; all the links will send you to the same place. It is a Google shortened URL that translates to the Facebook‘s fbsbx.com domain. This is used by Facebook as the domain where the attachments on chats and groups are shared and stored.
Why Attackers Use URL Shorteners
Hackers are known to use URL shortening services to obfuscate their real landing pages. It’s very effective on social networks. Some hackers think that using URL shorteners in site injections makes it less likely to be flagged.
Here are other reasons why shortened URLs are used:
- they may not scare the victims as much as long URLs that look odd and not reliable;
- they give the victim a sense of validity; especially in this case, since it is a Google service, people think it is probably safe;
- hackers tend to use tracking tools, such as the ones available in bit.ly, to see if their malicious campaigns were successful;
- hackers use additional tools to create their spam campaigns that shorten links automatically.
Conclusion
Attackers are relying on Facebook services to “host” their files, instead of using another hacked site to store the malware. I monitored this file and although the link was set to expire on Fri, 22 Dec 2017 16:15:47 GMT, it was taken down less than 24h after the email scam was received (probably by a Facebook malware scan process).
Our goal at Sucuri is to make the internet a safer place. If you want to receive email alerts on our latest blog posts, you can subscribe to our feed. Be safe!








