There’s an issue with how some people define the word “hacker.” For some, it’s a word synonymous with “cybercriminal,” but not in the infosec community.
White hat hackers (the good guys) are the ones who find security issues so they can be fixed. The world is a lot better off because of them.
Every day we interact with web applications and services built using programming languages. Hackers, both the white and black hat, comb through millions of lines of source code. They hunt for any little oversight in its creation, a security flaw that offers unauthorized access.
While monitoring solutions can identify when a compromise occurs, they are often too late. According to a study by IBM and Ponemon Institute, it takes an average of 196 days for organizations to detect a data breach. This does not include the time it takes to remediate the problem.
Protection is possible, but it’s not realistic to expect guarantees in a world built on software. It is important that developers and programmers learn best practices to prevent a security incident.
However, it takes one set of skills to build code – and an entirely different set of skills to break it.
Famous Ethical Hackers
Who are these intrepid warriors on the front lines of cybersecurity? Here’s a few notable white-hat hackers who have made the world a safer place.
Kevin Mitnick
One of the most prolific hackers is, without a doubt, Kevin Mitnick. After running from the law after a string of unauthorized access and wire fraud, he became the most wanted cybercriminal in America.
“Should we fear hackers? Intention is at the heart of this discussion.”
– Kevin Mitnick
Following his five-year stint in prison, Mitnick wrote several books and turned his skills to the white hat arena. His white-hat firm, Mitnick Security, now offers pentesting and security consulting for Fortune 500 companies (brands we probably use often).
Fun fact: His business card includes a functioning lock-picking set; a totem of hacking communities.

Charlie Miller
Prior to becoming well known for hacking cars and Apple products, Charlie Miller worked at the NSA and Uber. He was the first person to remotely hack an iPhone, and in 2008, he discovered a critical bug in MacBook Air during the Pwn2Own conference in Vancouver, BC, Canada.
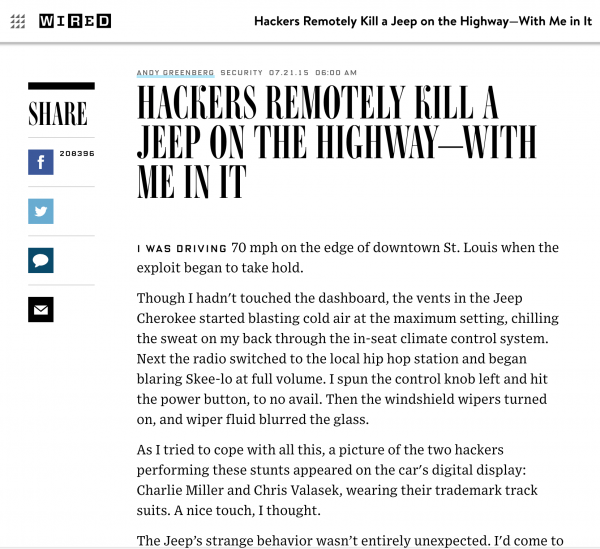
In 2015, Charlie Miller and Chris Valasek hacked a vehicle remotely while Andy Greenberg, a writer from Wired, drove it down the highway. With no physical access to the vehicle, they were able to control air-conditioning, radio, windshield wipers, even cutting the transmission and brakes. Their research was shared with the auto maker over a period of nine months, allowing them to patch issues and keep the streets safer.
Kevin Poulsen
Arrested by the FBI in 1991 after evading authorities for almost two years, Kevin Poulsen served 5 years in prison for computer fraud. His most delightful hack was winning a radio contest by compromising the phone company and ensuring his spot as the 102nd caller. For this, he won a Porsche 944 and $20K.
“Information is secure when it costs more to get it than its worth.”
– Kevin Poulsen
Like the other Kevin on this list, Poulsen turned over a new leaf once he left prison. His white hat achievements are pretty badass too. Poulsen wrote software that identified sex offenders on MySpace, resulting in new federal legislation and the actual arrest of an active pedophile. Since then, he’s been working as a journalist, gaining awards for his coverage of technology and cybersecurity. Poulsen also famously worked with Adrian Lamo, another hacker-journalist who helped the FBI apprehend Chelsea Manning for giving secret military documents to Wikileaks.

Greg Hoglund
In 2005, there were 5 million people playing Word of Warcraft. It was around this time Greg Hoglund blew the whistle on Blizzard Entertainment’s undisclosed “Warden” client. This program, which comes along with Blizzard titles like WoW and Diablo, scans user’s RAM and external processes for signs of cheating software. This had major privacy implications, and was called out by the EFF as spyware. Hoglund even created his own program, “The Governor,” to monitor Warden’s activity.
In addition to helping gamers, Hoglund made a massive impact on white hat security through his extensive research on rootkits, perhaps one of the most difficult and persistent forms of malware.
Fun fact: In 2011, Hoglund worked for the tech security firm, HBGary. His email was hacked, leading to a massively publicized hack. As CTO, that’s not good. It also serves as a reminder that the risk is never zero.
Dan Kaminsky
Big props to Dan Kaminsky for making sure the entire internet didn’t crumble in 2008. If you aren’t already familiar, DNS is what connects web addresses (www.example.com) to the physical address of the web server (example: 127.0.0.1). Kaminsky discovered a flaw in the architecture of the entire system.
The vulnerability would have allowed cache poisoning attacks against literally any site. Translation: a victim could enter a URL into the browser and be redirected to a malicious phishing site (i.e. your bank or email provider) without any malware needing to be present on the website or the victim’s computer.
“There exist threats to the continued correct running of the Internet. We have found one of them. There may be more.” – Dan Kaminsky
He worked in secret with experts in the DNS community from March through July, culminating in the release of one of the largest simultaneous security updates in history. While the patch remained secret during its development, a leak exposed the vulnerability halfway though the rollout, and black hats were quick to exploit it. By then, thankfully the largest DNS providers were already patched and the rest would be soon.
Thank You, Hackers
Not all hackers are malicious. The one trait they all truly share is curiosity.
The social stigma and laws against hacking have been a strong deterrent against pursuing a profession in cybersecurity. Bug bounty programs and penetration testing allow hackers to profit from their skills, but they are still largely misunderstood by the general public.
The scale of innovation in computer sciences is impossible to keep up with. If we want to minimize the risk of cyber crime, we need to embrace the hackers who live to break code so that it might be mended.