During a recent investigation, I found a new piece of malicious code being used to steal credit card information from compromised Magento sites.
What I didn’t know was how many domains would be uncovered as part of the malware campaign. Each of the malicious domain names was specifically chosen to appear as legitimate as possible to the website owner. The hosting provider used for these domains also turned out to be used for much more.
Magento Database Injections
Let’s start with the malicious code that was injected inside the Magento database, specifically under the core_config_data table.
This was the JavaScript injected into the database:
![]()
The JavaScript is loading malware from mcloudjs[.]com
Here is some of the hex encoded malware we discovered:
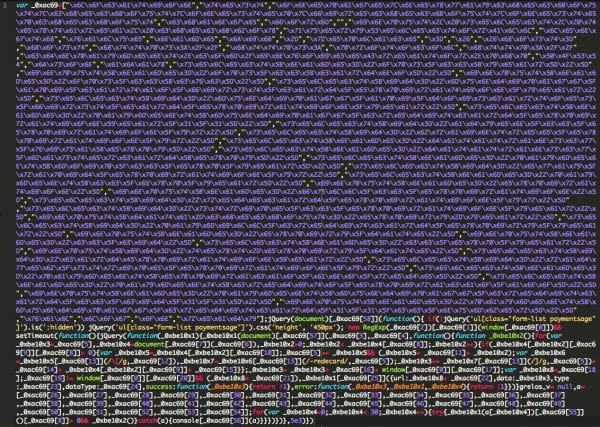
Once decoded, we see that the code is looking for the payment form where users enter their credit card information. The malware then attempts to send this data to cdnpayment[.]com
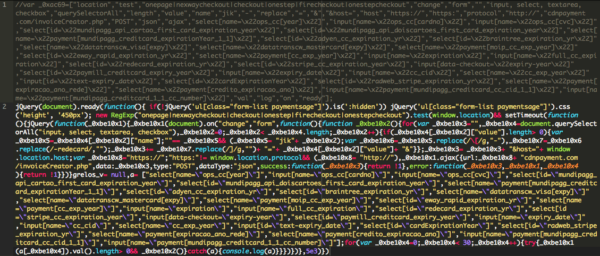
We took a look at this domain to see if there was anything more we could learn about how it was being used.
Server Hosting Multiple Malicious Domains
This was the response to a DNS query for the IP address associated with the domain cdnpayment[.]com:
;; ANSWER SECTION: cdnpayment[.]com. 27036 IN A 185.172.110.203
We dug a bit deeper to find out where this IP address was being hosted and what else was being stored there.
Here is the range of IP addresses owned by LeaseVPS:
inetnum: 185.172.110.0 - 185.172.111.255 netname: LeaseVPS country: NL
The same server with IP 185.172.110.203 appears to be home to quite a few questionable domains; some are also blacklisted by Google:
- apissystem[.]com
- codesmagento[.]com
- controlmage[.]com
- cdnppay[.]com
- resselerratings[.]com
- cdngoogle[.]com
- apismanagers[.]com
- verpayments[.]com
- myageverify[.]com
- assetsbraln[.]com
- verpayment[.]com
- magesources[.]co
- traskedlink[.]com
- magejavascripts[.]com
- mjs24[.]com
- m24js[.]com
- cdnassels[.]com
- magescripts[.]pw
- jscriptscloud[.]com
All of these domains are crafted to appear legitimate, and it seems there is a much larger campaign at play here that could have widespread impacts if the attacker is successful.
Domains4Bitcoins Used Maliciously
It looks like the original domain we found on the hacked Magento site was registered back in June of 2017, so we can assume that this campaign has been active for a few months.
Domain Name: CDNPAYMENT[.]COM Registry Domain ID: 2136693814_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.PublicDomainRegistry.com Registrar URL: http://www.publicdomainregistry.com Updated Date: 2017-06-25T09:16:25Z Creation Date: 2017-06-24T10:30:28Z Registry Expiry Date: 2018-06-24T10:30:28Z Name Server: 1A7EA920.BITCOIN-DNS.HOSTING Name Server: A8332F3A.BITCOIN-DNS.HOSTING Name Server: AD636824.BITCOIN-DNS.HOSTING Name Server: C358EA2D.BITCOIN-DNS.HOSTING
Based on the name servers used by the domain, I found that the VPS was most likely purchased from domains4bitcoins [.] com. It appears that they’re offering hosting which malicious users can pay for using bitcoins. This helps attackers avoid getting caught, as the payments are not traceable.
Same Campaign on Different Domains
I did some further investigation into the other domains hosted on that server and found that you can access the same malicious code from pretty much all of them.
Here are a few examples
- hxxps://controlmage [.] com/e/tracking.js
- hxxp://assetsbraln [.] com/e/tasking.js
- hxxp://codesmagento [.] com/e/tracking.js
- hxxp://cdngoogle [.] com/e/tracking.js
The following scripts are also available on all the domains:
- /ex-payment.js
- /e/tracking.js
- /cv5/tasking.js
- /e/ms.css
- /ext/htc.css
- /hdt.js
It’s even possible to use a random script name and get the same malicious code. Here is an example:
- hxxp://controlmage[.]com/ext/really.pdf
Ransomware and Credit Card Scrapers
I also did some research on the name servers, specifically other domains using BITCOIN-DNS.HOSTING. I found that not only was the Magento malware hosted on servers provided by the same company – it looks like ransomware is also involved.
Some users reported that an email under aolonline [.] top had been used as a buyout email for the ransom. The domain aolonline [.] top used the same name servers along with a few other domains involved in other ransomware attacks like mortalkombat[.]top
Conclusion
Hackers have no problem finding hosting services for their malware and ransomware campaigns. Even if one hosting provider is taken down, in no time there would be three more to take their place.
As we approach the holidays, we expect to see a rise in attacks on ecommerce sites. Hackers are getting ready to take advantage of the increase in online shopping being done throughout the next few months.
Service providers need to be taking more steps to educate their growing audience of new website owners who expect security to be included with website hosting and development.
As a website owner, you can reduce the risks by keeping your software up to date, or by virtually patching with a website firewall. This helps close any security holes in your framework. The other piece is using good account management, including passwords and least privileged access principles. These two elements do the most to protect your website and your visitors.
In the event of an incident, integrity monitoring services and professional incident response are the best ways to ensure you can respond quickly.