The final actor of the stolen payment data supply chain is the end user. Rather than just selling or reselling payment data, the end user plans on fraudulently monetizing it.
This malicious end user typically buys payment data in limited quantities, since:
- The price per stolen data greatly increases from when it was originally sold by the source.
- There’s an unknown amount of time until the financial institution revokes the issued stolen data. As a result, it’s in their best interest to use the stolen payment data beforehand.
We can break down this end user group further into two subgroupings based on the nature of the fraudulent transactions they commit: Physical transactions or Card-Not-Present (CNP) scenarios.
Physical Transactions
This form of transaction occurs when the user makes a physical payment with the stolen data during the fraudulent transaction. In this case, the card is physically swiped or inserted and the criminal obtains possession of an item. This fraudulently purchased merchandise is then resold to a buyer who pays with USD. Cryptocurrencies may also be accepted for online transactions.
The implementation of EMV chip payment cards has been ongoing for years within the United States, however not all businesses have the POS terminals required to support this standard (despite changes to the liability for fraud transactions). As a result, payment card issuers are still including magnetic stripes on newly issued payment cards.
Before the criminal can actually use any stolen data, they must generate a physical payment card with the information purchased from the darknet. It’s possible to pay someone to generate a payment card with the stolen data, but that usually takes a long time and is costly. Or they could just rip you off and steal the payment data you gave to them.
Ideally, the criminal wants the payment card to accurately reflect the stolen data that they encode onto the magnetic stripe.
A blank payment card with a design (e.g Chase Visa) matching the stolen payment data is also preferred for authenticity purposes. While this step isn’t necessary and is an additional cost to the criminal, it reduces the risk of a merchant noticing a discrepancy between names and account numbers, further preventing detection.
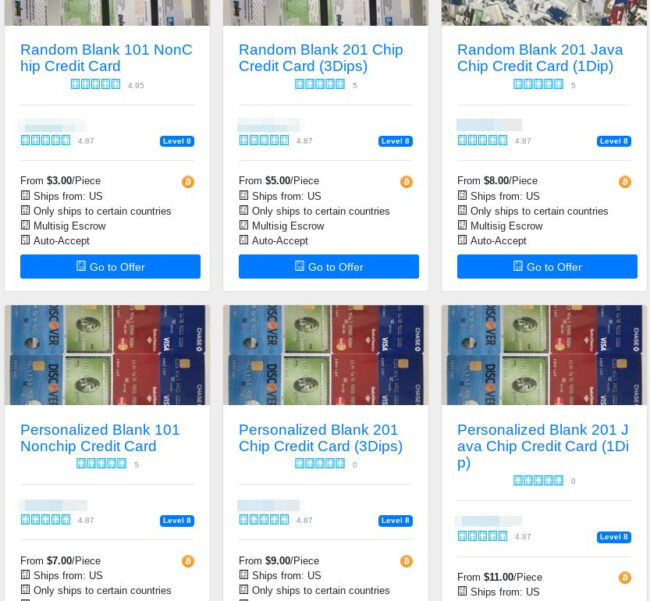
Once the criminal has the stolen data and blank payment card, they can begin generating a physical payment card on their own. Two necessary tools are typically employed for this purpose, and can be easily found on popular websites like Amazon:
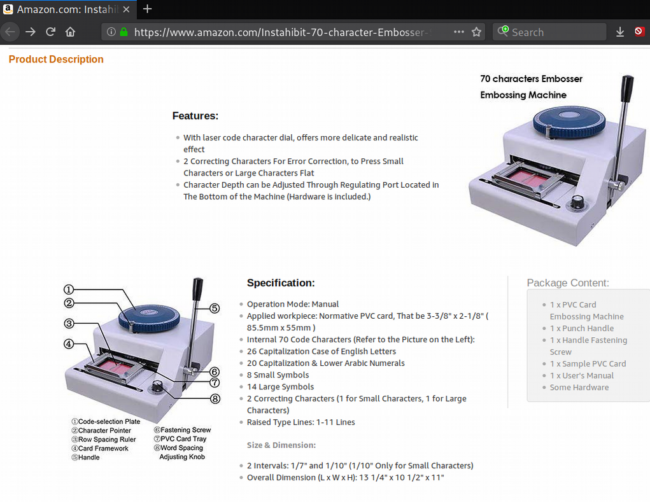
Embosser
This is a printing device used to create the embossed text on payment cards. This is the raised, three dimensional text that is slowly being phased out in favor of laser etched payment cards (text is not raised and cannot be removed easily).
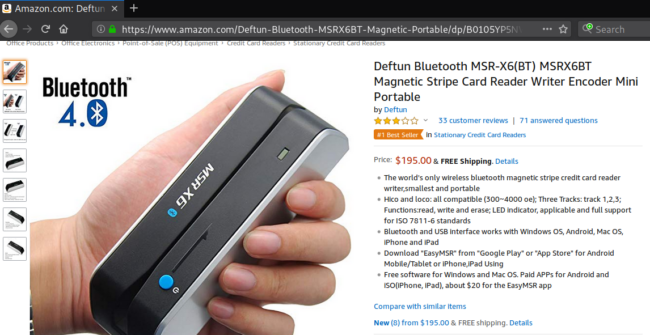
Encoder
This is a device used to encode (or decode) stolen payment data to the magnetic stripe on the back of a payment card, which doesn’t have to be blank. Attackers can connect it to a device via USB or Bluetooth to transmit and receive the stolen payment card data collected from the stripe.
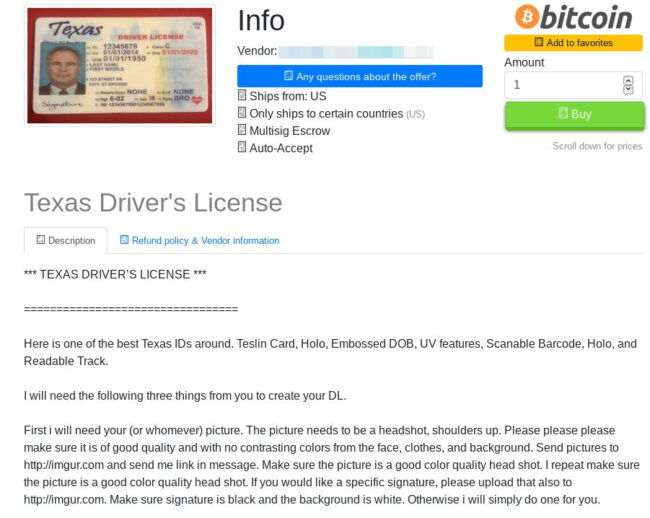
Matching Fake ID
A counterfeit license helps the attacker pass all of the major security tests by matching stolen payment data along with a picture of the criminal. If a merchant requests to see identification at the time of purchase, the criminal can simply show their counterfeit ID. It’s an optional tool for the criminal, but it can serve as a very beneficial credibility indicator for fraudulent transactions.
Now that the criminal has their physical payment card loaded with stolen payment data, they can begin searching for vulnerable businesses where they can commit fraudulent transaction(s) to obtain high value items for resale. Consumer electronics, like iPhones or Macbooks, are frequently targeted as they have a high demand and can be quickly resold at prices cheaper than legitimate sellers. A matching fake ID makes it possible to obtain even higher value items like rental cars or used cars.
Card-Not-Present (CNP)
CNP occurs when the payment card used for the fraudulent transaction is not physically present. Nowadays, the majority of CNP is done through online transactions, but telephone and postal services may also be used.
Since criminals are not physically present during fraudulent transactions, it’s easier for international criminals to exploit stolen payment data from foreign countries. In fact, some governments even release statements discouraging their citizens from traveling to countries with extradition treaties for the United States.
One method used to cash out payment cards without the use of physical drops (e.g receiving stolen goods to an address resale) is to exploit payment processors in conjunction with a fake ecommerce website set up by the criminal. A great example for Stripe’s payment platform is outlined here.
Once the stolen funds have been consolidated from multiple stolen payment cards, foreign criminals use money/stolen good mules to launder their money through the mule’s personal bank accounts.
Mule Fraud
Mules are sometimes knowing participants in an illegal money laundering operation. However, cases exist where unknowing victims are targeted with “work from home” advertisements and other tempting job offers on the Internet.
Of course, these are not legitimate jobs. Criminals make them appear like the job is a foreign import/export business, providing a somewhat plausible reason for why they are “hiring” for a position in the victim’s country.
The process is similar to other forms of mule fraud:
- Mule is “hired” by a group to perform financial transactions (and may or may not be aware of the criminality).
- Mule’s established bank receives funds from a fake business account.
- Mule is instructed to withdraw the received funds and keep some portion of it as payment for their services.
- Mule uses a money transfer service (e.g. Western Union) so the criminal can collect the funds in their location.
- Repeat until bank detects the fraud and suspends the mule’s account.
If we know that the criminals can easily purchase personal information and use it to create bank accounts online, then why would they need to even use mules? The reason is that the mule’s bank account is usually already aged (a term used to describe a financial account that is in good standing and has successful, common transactions on its account history).
This results in less suspicion at banking institutions when the fraudulent funds are sent to the mule account by the criminals, and the likelihood of the mule being able to successfully withdraw the funds in cash is higher.
If the criminal simply opens an American bank account with a stolen identity and no successful account history, then they would likely be flagged for further review by the bank when cash begins circulating.
Subscription Services for One-Time Payments
Another method used by criminals is to use stolen payment data to create accounts for popular subscription-based services and then resell them to others at a steep discount.
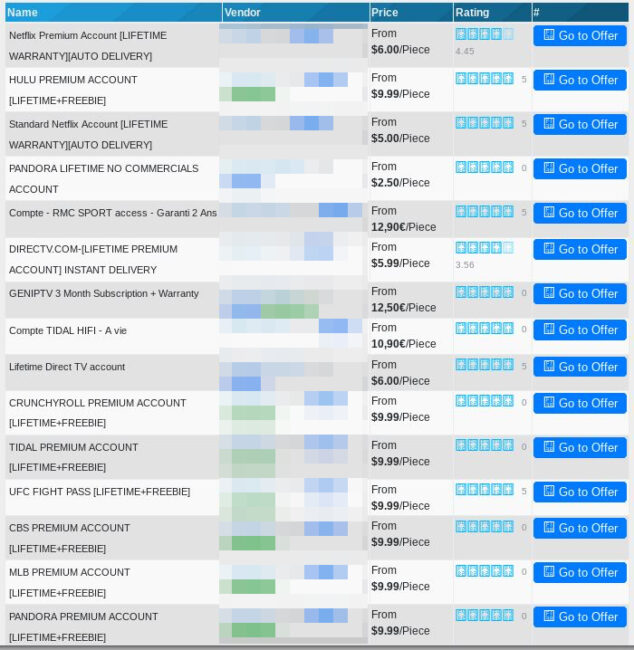
These are popular services that come with “lifetime” guarantees which means that the seller will replace the buyer’s subscription login should it stop working due to a chargeback or other fault of the seller.
Conclusion
The examples outlined here demonstrate the pipeline that stolen payment data must take to be used for fraudulent transactions with stolen payment data.
As these forms of fraud continue to grow exponentially, it’s important for consumers to be vigilant and not solely depend on credit or bank companies to defend accounts against criminals.
This is not a sponsored post and I have no affiliation with the company, but one service that I have been using for over a year now is privacy.com. This service allows you to link a bank account to generate credit cards on-the-fly with specific spending limits. You can also designate the generated credit card as a one-time use.
Virtual card services can be helpful in hiding your real credit/debit card data should it become compromised, though your name and address will still be vulnerable to theft, so do the measures you can to be as safe as you can online.










